Guide: Modernizing Your Security Operations Center (SOC)
SOC Security Services: What is a Security Operations Center?
The CyberProof Guide to Modernizing Your Security Operations Center (SOC) highlights common challenges faced by SOCs and suggests key strategies to bring together security teams, processes, and technology to streamline cybersecurity efforts & reduce costs.
What is a SOC?
What SOC stands for is “Security Operations Center” – a physical or virtual space that correlates all security events, validates them, and takes action to eliminate threats. The SOC monitors an enterprise’s networks, accounts, devices, appliances, information stores, and other assets for suspicious activity that may indicate a breach or an attack.
How SOC Security Services Center works?
A SOC is a on-prem., hybrid, or cloud-based strategic hub that executes and monitors security strategies in line with an organization’s people, processes, and technologies, as follows:
- People – Due to the cybersecurity skills gap, SOCs struggle to attract and retain top talent. Many companies outsource some or all of their SOC services to Managed Security Services Providers (MSSPs). It’s crucial to maintain visibility, even when outsourcing. An advanced MSSP can offer a hybrid model that allows full collaboration between the in-house team and the external provider.
What’s key in this situation is maintaining visibility, even where services are outsourced. With an advanced MSSP, you can use a hybrid engagement model that supports full collaboration between the in-house team and the external service provider. - SOC processes – SOC processes should align with industry frameworks like NIST or ISO/IEC 27001. Customizing incident management processes with playbooks tailored to specific threats is essential. The MITRE ATT&CK matrix helps identify attacker tactics and techniques for building new use cases. Continuously improving detection rules and digital playbooks through development, testing, deployment, and optimization enhances threat coverage.
- Technologies – When building or augmenting your SOC Network, you should consider incorporating key technologies to improve enrichment of your Detection & Response capabilities. Evaluating the right technologies can take a considerable amount of time, and you may want to work with a partner who is familiar with the available technologies and can help you select the best products and services for your organization.Key technologies that are essential to effective Detection & Response include a cloud-native SIEM with automation and orchestration, threat intelligence, vulnerability scanning, and Endpoint Detection & Response (EDR) capabilities.
Key functions and responsibilities of the Security Operations Center
When defining the key functions and responsibilities of the SOC, many people ask what is SOC security exactly? The answer is that SOC security not only responds to incidents in a defensive or reactive process but should also serve as the driver of your company-wide cybersecurity program.
SOC leaders looking to optimize their SOC generally follow the following process of development:
- Definition of log collection – Identifying the assets, tools, technologies, and applications that should be integrated.
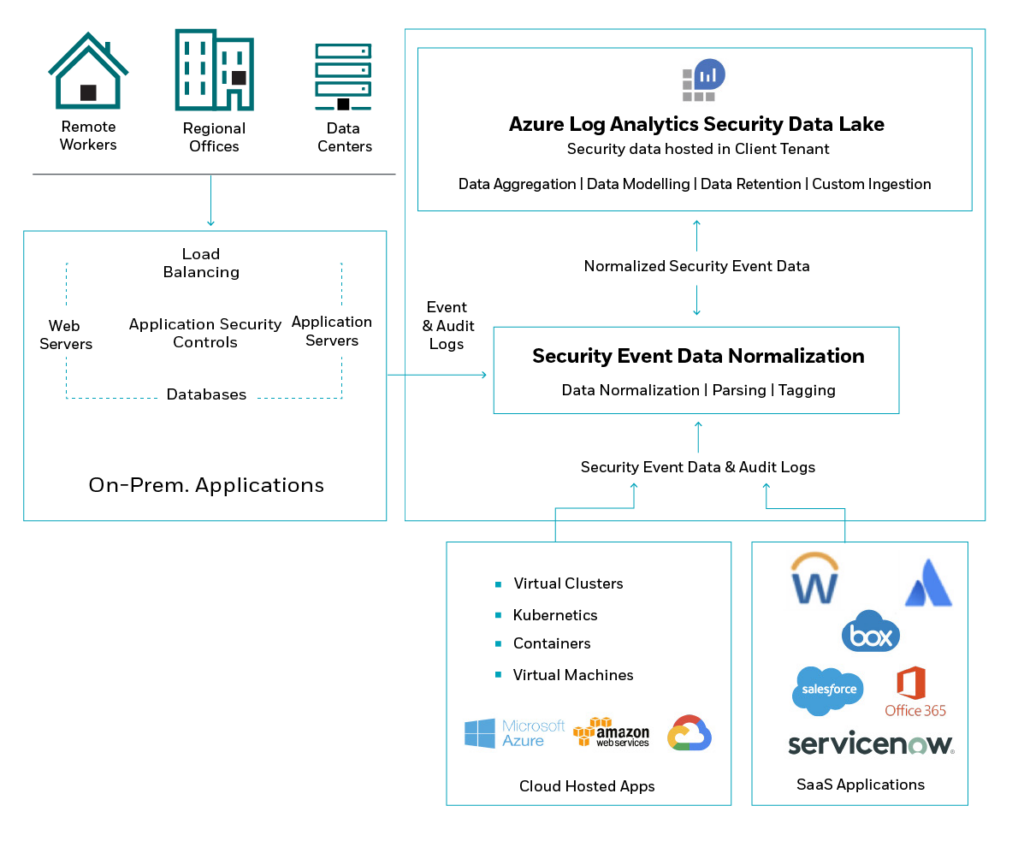
- Collection, management, and storage of data – Finding the best ways to simplify the data collection, management, and storage process. For example, at CyberProof, we leverage Azure Log Analytics and CyberProof Log Collection (CLC) to pull logs from multiple sources.
Collection, Management, and Storage of Data with Azure Log Analytics
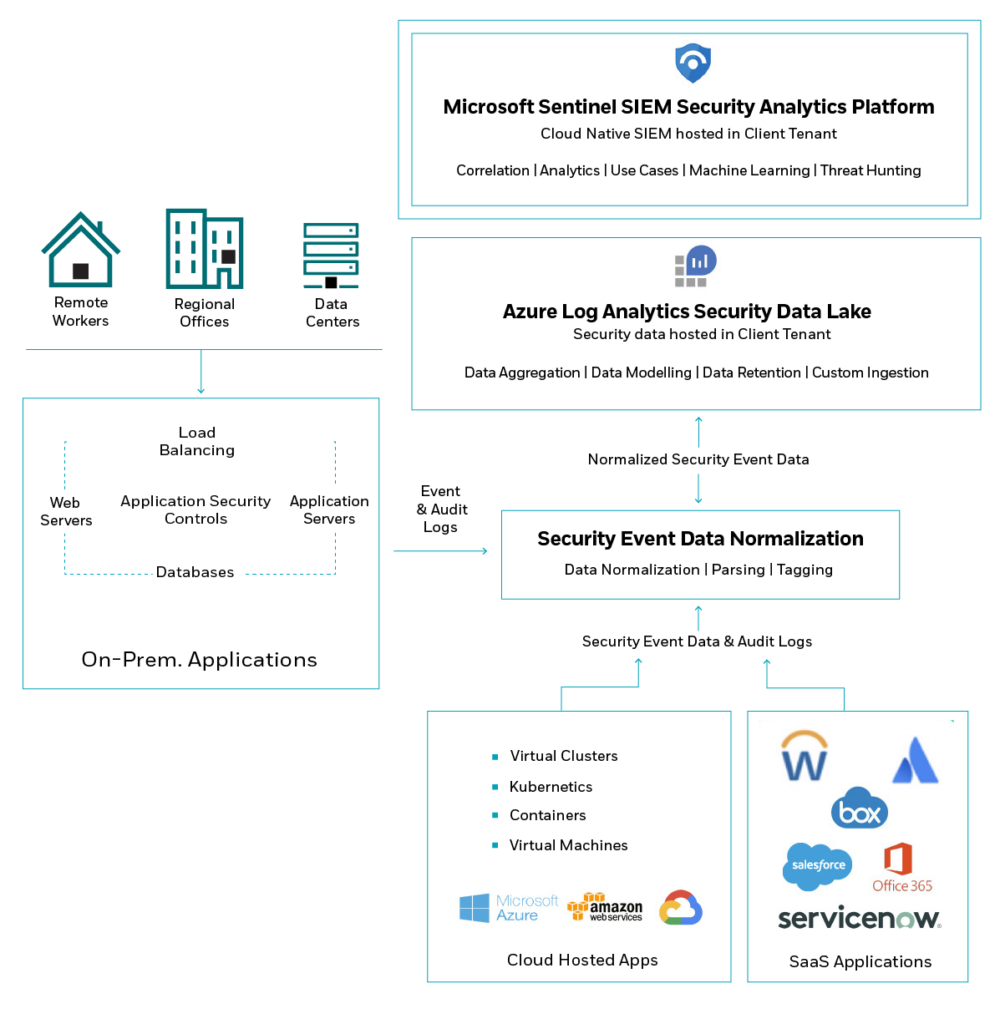
- Leveraging SIEM capabilities for security analysis – Conducting analytics using the SIEM which can identify anomalies using detection rules.
Using Microsoft Sentinel for Security Analysis
- Orchestration, automation, and collaboration – Adopting processes and technologies that maximize efficiency to provide faster incident resolution with greater efficiency.
SOC analysis, processes, monitoring, and software tools
Protecting enterprises from cyber threats involves the following steps:
- Anticipating – Preparing for potential attacks by developing a thorough understanding of internal and external threats and exposures, including going through a deep vulnerability discovery & prioritization process (internal) – and leveraging targeted threat intelligence (external).
- Detecting – Implementing log collection, onboarding security, and event logs that align to prioritized threat scenarios and business risks. This also includes conducting threat hunting, proactively detecting and isolating advanced threats and extending visibility using Endpoint Detection & Response (EDR).
- Reacting – Managing alerts to efficiently assess, contain, and eradicate critical incidents to recover quickly and minimize the business impact. In this step, digital forensics are used to establish the root cause of each incident and trace its attack path to understand its full impact by reconstructing events and analyzing the evidence.
- Improving – Leveraging the MITRE ATT&CK framework to develop and maintain updated detection rules and playbooks aligned with relevant use cases. This includes orchestration and automation to increase the speed of response and enrich alerts.
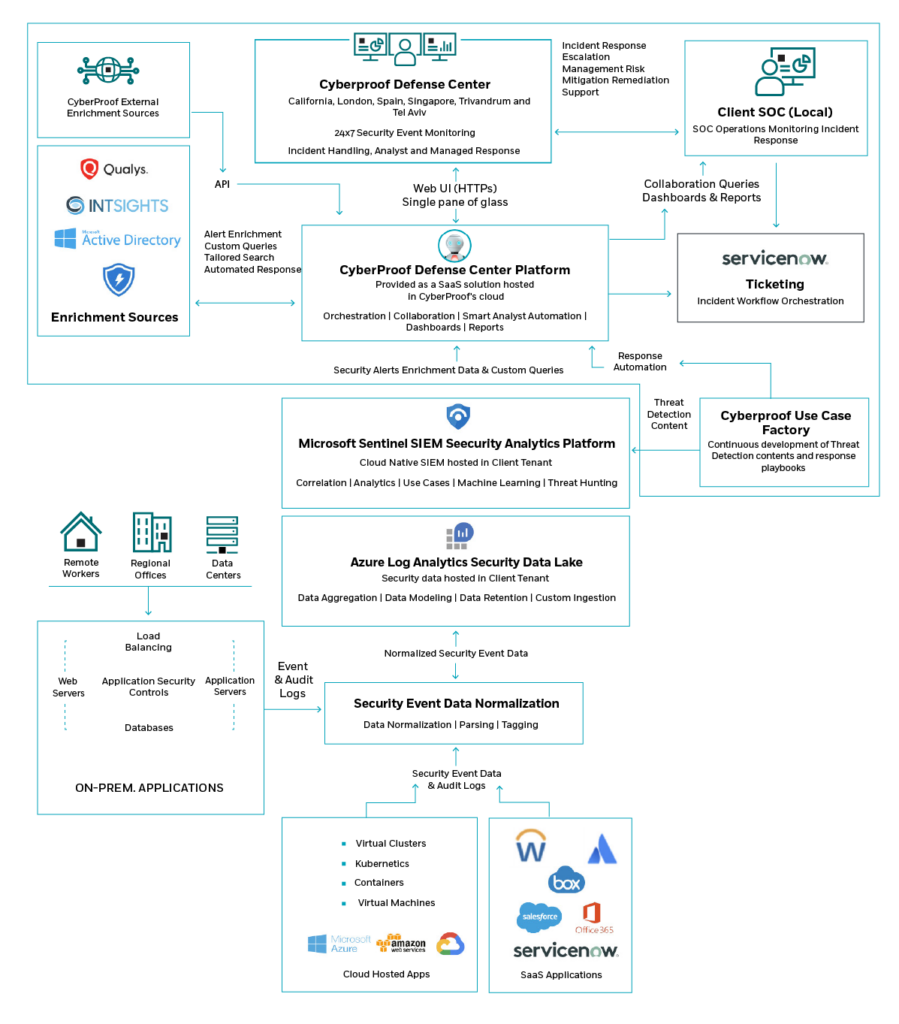
For example, at CyberProof, our CyberProof Defense Center (CDC) platform automates routine tasks including SOC analysis, alert triage, event enrichment, investigation, issue containment, and execution of response playbooks, to increase efficiency and effectiveness for SOC analysts.
Optimizing Orchestration, Automation & Collaboration with CyberProof’s Platform
Who needs a SOC?
As our technology landscape is rapidly changing, companies are experiencing an ever-increasing number of aggressive and sophisticated cyber-attacks.
To tackle the growing number of attacks, companies are bringing together their security teams, processes, and tech into one spot – a centralized SOC.
This not only updates their security operations but also helps them streamline cybersecurity efforts, cutting down on risks and costs.
Security operations staffing and organizational structure
Since security analysts are always on the front lines of cyber defense, they often face alert fatigue and burnout. Keeping a strong SOC team means investing time and effort to keep everyone motivated and satisfied.
Here are some of the strategies that are important to building a strong organizational structure, and successfully staffing and maintaining a strong SOC team:
- Training – Encourage SOC analysts to learn new skills, deepen their technical and professional knowledge, and get industry certifications.
- Remote Work – Support employees working from home by providing the right equipment, helping them set up ergonomic workspaces, and offering take-out meal options. Also, train managers to recognize mental health issues.
- Open Communication Channels – Create opportunities for informal chats, whether in the hallway, at the coffee counter, or via virtual tools like Zoom or Microsoft Teams. SOC analysts should feel that managers understand their challenges and are committed to supporting them.
- Buddy Program – Assign buddies to the more junior members of staff. The senior members of the SOC team can reach out and make sure that newcomers have an address for their questions.
- Onboarding – If possible, do the onboarding in person, in the office. If it needs to be done remotely, adopt a more in-depth onboarding program. The onboarding is an opportunity to share not just technical information but also to present the company’s values and integrity.
- Professional Growth – SOC managers can help each member of the team figure out a career path, a roadmap for the future. Help people develop goals that are SMART – specific, measurable, achievable, realistic, and timely. Doing this effectively requires putting aside time for 1-on-1 meetings on a regular basis, so that you can get to know your team better and understand what motivates them.
SOC best practices
For enterprise companies, measuring performance is key to ensuring the success of your SOC. Some of the essential metrics that should be checked can be categorized in the following areas to ensure your SOC is performing in line with best industry practices:
- Effectiveness and Accuracy – These measure how effective your SOC is in correctly identifying validated incidents and false positives. Example metrics include Number of Events, Alerts and Incidents, Percent of Alerts Resulting in an Incident, and Percent of Alerts Identified as False Positive.
- Speed and Efficiency – Triaging alerts and managing incidents in a timely manner. Example metrics include Average Time to Triage, Average Time to Identify an Incident, and Average Time to Respond/Close an Incident.
- Continuous Improvement – Improving the rate by which you’re able to reduce false positives and response times. Example metrics include Reduction in False Positives, Percent of Incidents Closed by Level 1, Time to Close Over Time, and Percent of Incident Managed Automatically.
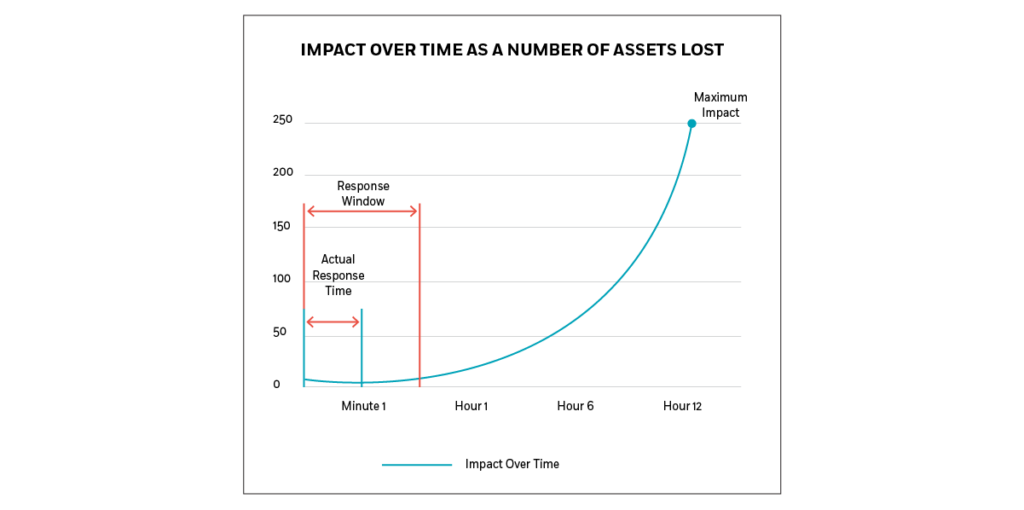
Impact of Cyber Attack Over Time as a Number of Assets Lost
SOC Security Services Challenges
Today, SOC leaders are facing a wide variety of challenges. These include:
- The cost of legacy SOC software and on-prem. security tools, which can be very expensive to maintain and operate.
- The sharp increase in data collection and storage requirements during a cybersecurity incident may be beyond the capabilities of an on-prem. SOC environment.
- Legacy security information and event management platforms are some of the more common SOC tools that are used, but these may be unable to cope with the explosion of data resulting from widespread migration to the cloud.
- Regarding the use of SIEM, SOC teams tend to view the SIEM as the core data source of their threat detection & response capabilities and as an essential component of all security operations.
- Convergence of Information Technology (IT) and Operational Technology (OT) is a trend that has many advantages but that also creates new vulnerabilities.
From a budget perspective, there are additional challenges to SOC cybersecurity practices. Some of the SOC definitions and questions that SOC leadership is required to provide to the board – and to which there aren’t always clear answers – include:
- How did our investment in technology reduce our business risk?
- How much were we able to successfully reduce risk?
- Did we focus on the areas that matter the most?
- Did we invest the right amount, not enough, or too much?
- How do we measure the success of our security operations?
- Are there indications that as an organization, our security capabilities are improving?
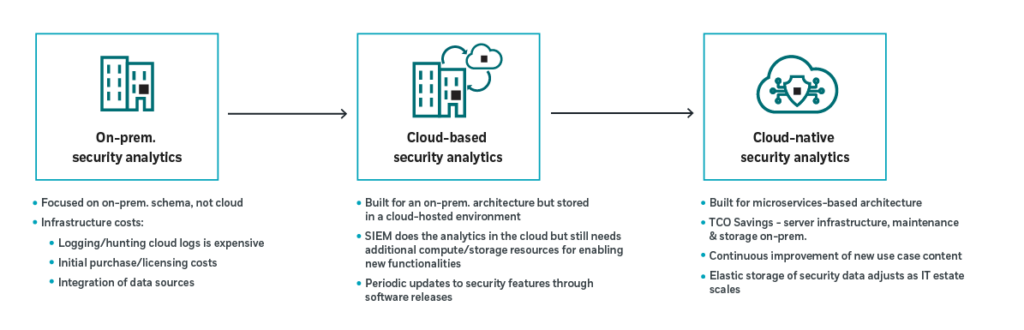
Migrating to the cloud – SOC modernization
Many organizations are currently undergoing digital transformation – migrating their on-premise business services, infrastructure, and applications to cloud-based environments. But doing so creates larger, and more complex attack surfaces to monitor, with multiple potential entry points for attackers.
To keep their enterprise safe, security teams must modernize the SOC too – by adapting security operations center roles and responsibilities and implementing processes that allow Detection & Response of threats within the cloud environment. Solutions such as Microsoft Sentinel and their Azure Security stack are designed to reduce the risk of cyber-attacks in cloud-native environments.
Security Operations Have Moved to the Cloud
Optimizing a security operational model
There are many advantages to working with an advanced Managed Security Services Provider (MSSP). Some companies decide to outsource all their security needs by using subscription-based SOC-as-a-service solutions, while others maintain an in-house SOC that operates during business hours, outsourcing the work at night and over the weekends.
Increasingly, organizations are opting to use a hybrid resourcing model that is partly in-house but also relies on the services of a third-party security services provider. An advanced MSSP provides you with on-call high-level SOC experts, instantly giving your organization access to top people in the field with extensive experience, while leaving you with the ability to pick and choose SOC services on demand. Services are delivered via a SaaS-based platform that is used both by the provider’s team and client’s team for full collaboration, communication, and reporting in real time to internal stakeholders.
For organizations that are part of a larger umbrella organization, you can reduce costs further with a third-party service provider by aggregating your security and IT operations into a single SOC and network operations center (NOC). This is much more cost effective than having each subsidiary or branch maintain its own teams.
Another advantage of the hybrid resourcing approach is that it makes it easier to maintain 24/7 support. By working with an MSSP, you do not need to retain a full SOC team where people are required to work through the night or on weekends.
Benefits of a Security Operations Center
Many aspects of SOC operations can be done better by computers than humans. However, the ability to think creatively and find innovative solutions remains a uniquely human capability.
Automated capabilities allow a SOC team to respond faster. For example, CyberProof’s research shows that 95-98% of alert triage can be automated. This reduces the human effort required to identify which alerts do need human support.
SOCs can automate tasks including enrichment of event data, external source querying, obtaining actionable information in response to specific requests, opening incidents based on context, and executing digitized playbook steps that are not intrusive.
Utilizing these SOC benefits and automated capabilities, such as CyberProof’s virtual analyst SeeMo, gives greater visibility into the threats that are most significant and provides faster response to emerging threats.
At CyberProof, we leverage artificial intelligence (AI) and machine learning (ML) – working with our virtual bot SeeMo to increase threat visibility and enrichment. Our CDC platform streamlines SOC operations, automating the more tedious, repetitive aspects of alert and incident handling so that SOC analysts can focus on mitigating the risk to the business.
To learn more about SOC operations, download our eBook: A buyer’s guide to
modernizing your
security operations
center

Frequently asked questions
What does SOC mean in security?
What is SIEM and SOC?
What are SOC services?
What is a SOC room?
How does a SOC work?
What is the SOC and its benefits?
Why is SOC needed?

Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.
SPEAK WITH AN EXPERT