How does threat hunting help enterprises maintain a more effective cyber security strategy and respond to threats more effectively? What is it about threat hunting activities that measurably reduce risk?
In the following sections, let’s explore how security leaders can leverage the capabilities of a dedicated threat hunting team to mitigate the business impact of potential cyber-attacks and improve Security Operations Center (SOC) processes for threat detection and response.
What is Threat Hunting?
Threat hunting involves proactively searching for malware or attackers hiding within a network. Typically, threat hunters operate under the assumption that an adversary has already infiltrated the network. The hunter’s daily task involves searching for evidence of infection.
But threat hunting is not limited to threat detection. Many security leaders are not aware that threat hunting professionals provide assistance in reducing the attack surface of the enterprise – improving the security posture of the network, over time.
Threat hunters operate under the assumption that an adversary has already infiltrated the network. The hunter’s task involves searching for evidence of infection.
As a starting point, threat hunters evaluate the network and develop several important baselines. Once that has been accomplished, threat hunters frequently are able to proactively pinpoint misconfigurations within the network as well as policy violations. Threat hunters may also be able to suggest solutions for addressing existing security gaps.
In recent years, the security industry has come to realize that threat actors have the upper hand during the infection process. That’s because defense systems frequently cannot block sophisticated breaches, and threat actors keep evolving – and they can stay dormant in the network for months. (Research on this topic is available here: 1, 2, 3)
Moreover, the response time for major incidents can involve hours of time – and during this time, the attacker is free to continue having a malicious impact on non-contained endpoints.

Threat Hunting Tools Augment a SOC’s Capabilities
Most cybersecurity professionals agree that a SOC requires the following capabilities: a team of well-trained security analysts to triage and handle alerts, an Incident Response team to handle the escalation of major incidents, ongoing intelligence updates (providing key information about new threats and trends), penetration testing routines, and vulnerability assessments.
Threat hunting adds another layer to these capabilities – providing a proactive approach that complements the SOC’s more reactive procedures. It compels organizations to change the way they act in response to threats.
Threat hunting provides a proactive approach that complements the SOC’s more reactive procedures.
Threat Hunting has two main goals:
- Strengthening the cybersecurity ecosystem by incorporating a more proactive and holistic approach
- Improving an enterprise’s security posture by reducing the attack surface
| Threat Hunting Tools | Description |
|---|---|
| Splunk | A comprehensive platform for searching, monitoring, and analyzing machine-generated data. |
| Elastic (ELK Stack) | A search engine and analytics platform that includes Elasticsearch, Logstash, and Kibana. |
| IBM QRadar | A security information and event management (SIEM) solution that provides real-time visibility and intelligence. |
| Microsoft Sentinel | A cloud-native SIEM and security orchestration automated response (SOAR) solution. |
| CrowdStrike Falcon | A cloud-based endpoint detection and response (EDR) platform. |
| Carbon Black | An endpoint protection platform providing advanced threat detection and response. |
| FireEye Helix | An advanced threat detection and response platform combining SIEM and SOAR capabilities. |
| Palo Alto Networks Cortex XDR | A detection and response platform integrating network, endpoint, and cloud data. |
| Darktrace | An AI-based cybersecurity platform that detects and responds to threats in real-time. |
| RSA NetWitness | An advanced threat detection and response platform with capabilities in SIEM, network traffic analysis, and endpoint detection. |
| Securonix | A next-gen SIEM platform leveraging machine learning for advanced threat detection. |
| AlienVault USM (Unified Security Management) | A security management platform that integrates asset discovery, vulnerability assessment, intrusion detection, and SIEM. |
| CylanceOPTICS | An EDR solution providing visibility and insight into threats using AI. |
| LogRhythm | A SIEM platform that integrates log management, network and endpoint monitoring, and advanced analytics. |
| Rapid7 InsightIDR | A cloud SIEM that combines SIEM, EDR, and UBA (User Behavior Analytics). |
| Cisco SecureX | An integrated security platform that combines threat detection, response, and orchestration. |
| Symantec Endpoint Detection and Response (EDR) | An EDR solution offering advanced threat detection and response capabilities. |
| Trend Micro Deep Discovery | A network-based advanced threat detection platform. |
| OpenDXL | An open-source communication fabric for integrating security products and enabling automated threat response. |
| ThreatConnect | A threat intelligence platform that combines SIEM and SOAR capabilities with advanced threat hunting features. |
Threat Hunting as a State of Mind
Threat hunting requires taking preemptive action – anticipating issues before they have a chance to develop into full-scale problems.
Here are some specific examples of how adopting a threat hunting approach to cybersecurity can have a radical impact on an enterprise’s security operations:
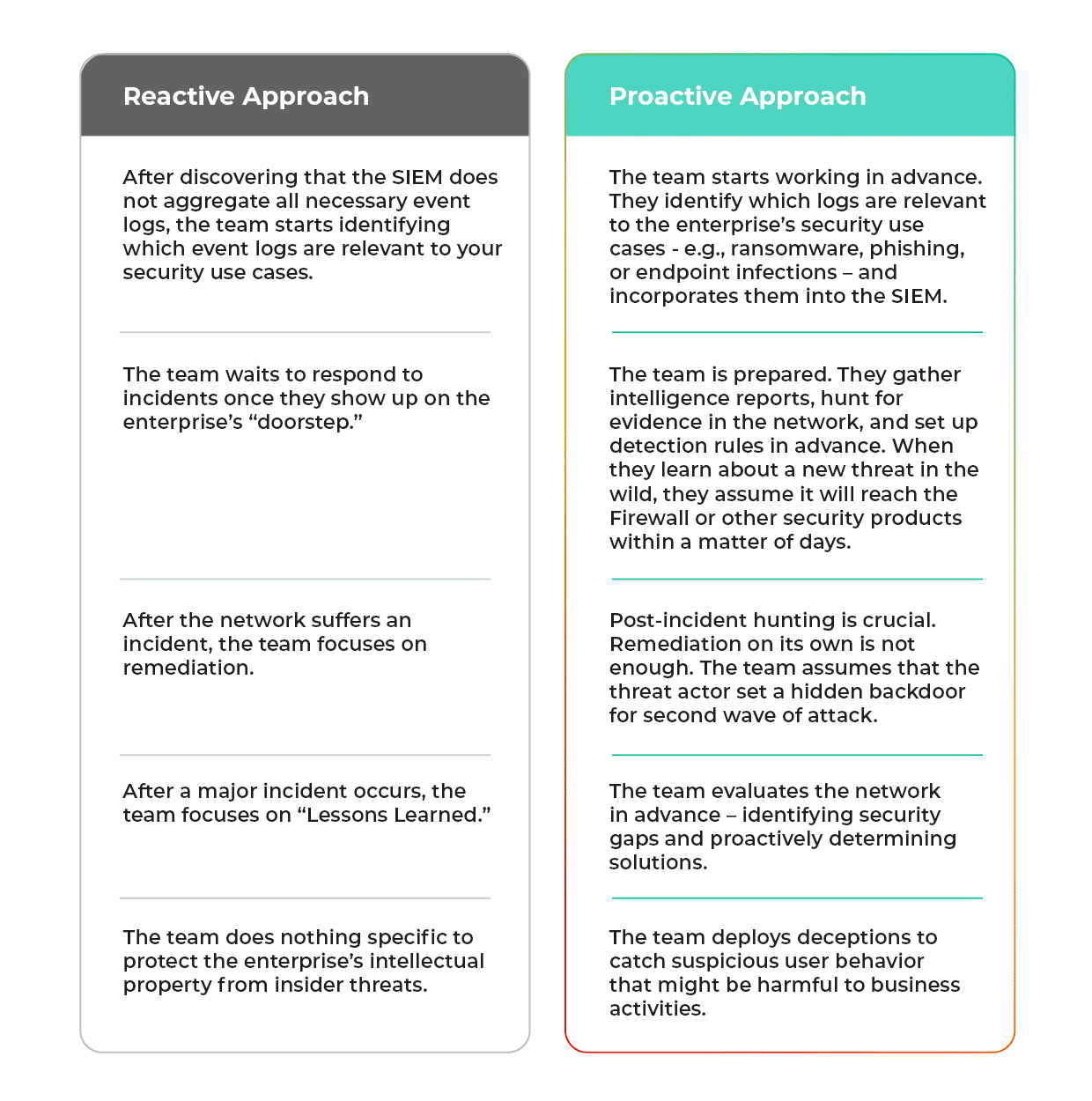
The Best Way of Conducting Threat Hunting
Threat Hunting teams work best when they work from several different angles, in parallel, to reduce the attack surface. For example, CyberProof’s Threat Hunting team maintains six distinct layers of activity:
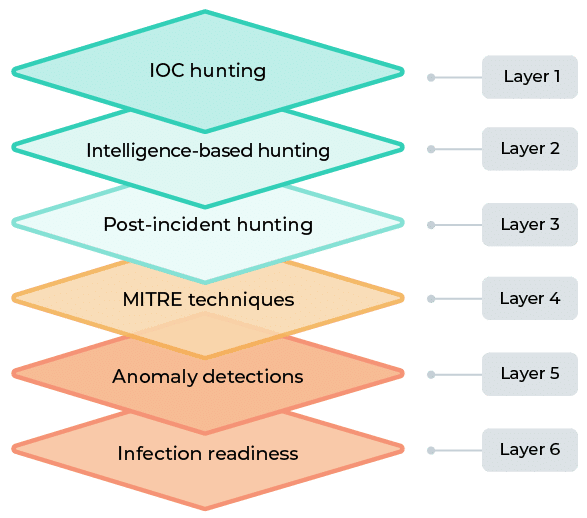
- Layer 1 – IOC hunting: A basic and common method of threat hunting involving Indicator of Compromise (IOC) retro-hunts. The hunter collects a mass of IOCs based on their relevance and queries for them in the SOC’s security products, including the Firewall, EDR, Proxy, SIEM, etc.
- Layer 2 – Intelligence-based hunting: The hunter accumulates intelligence reports about recent threats, new techniques, unpatched vulnerabilities, and new attacking tools, and searches for forensic evidence that confirms or disproves the existence of an Indicator of Attack (IOA) in the environment. (Note that intelligence is most effective when it is specific to a particular industry.)
- Layer 3 – Post-incident hunting: After a critical incident takes place in the network, the hunter leverages the incident report. The hunter creates workflows that search across the network for the malware or attacker and identify additional infected hosts or vindicate the rest of the network.
- Layer 4 – MITRE techniques: The hunter prioritizes blind spots in MITRE tactics and techniques, then identifies and hunts for forensic evidence that confirms or disproves the use of specific techniques. This approach is significant because it helps customize a dedicated, cyber Threat Hunting plan and adapt it for a specific environment – providing proactive solutions for specific security risks.
- Layer 5 – Anomaly detections: The hunter explores large amounts of data to detect anomalies based on a customized baseline and identifies security gaps. This mostly involves focusing on items that pop up based on the hunter’s knowledge of networking or protocols, for example: suspicious characteristics of HTTPS headers, malware beaconing or cryptomining activities, torrent or streaming, unauthorized data transfer, etc.
- Layer 6 – Infection readiness: Compromise is inevitable; no organization can avoid all possible threats. What’s possible and essential is preparing your network. The hunter sets up what’s necessary for effective detection in advance, hardens endpoints and servers, deploys deceptions on Active Directory, runs ransomware simulations, and conducts tabletop exercises.
The success of cyber threat hunting activities can be measured by looking at these layers, e.g., how many use cases were deployed? How many playbooks were developed? A common misconception is that a hunt can only be classified as successful if something malicious has been discovered. But this is not true. In fact, it may be more accurate to say that if every hunt uncovers malicious results, this does not signify the success of the hunt but rather is a sign that the organization has poor defenses.
Key Aspects of a Hunting Process
An effective approach to threat hunting involves putting the focus on:
- Infrastructure knowledge – One of the advantages that threat hunters have over threat actors is that hunters can have internal brainstorming sessions with the CISO about the network – creating baselines that facilitate an understanding of standard communications and behavior for users, endpoints, services, protocols, accesses, etc. These baselines assist the threat hunter in detecting outliers.
- Context for adversaries and attacks – It is important to know which technique threat actors are using, but that’s not enough. Threat hunters must understand a technique within the context of forensic evidence, and of identifying the correct indicator to hunt for. For example: What evidence does a technique leave on a compromised endpoint? What kind of Registry key is changing an infected server? What kind of file is modified during the attack? Moreover, working in collaboration with the Threat Intelligence team assists the hunter in two ways: by focusing on threats that target specific industries; and by providing proactive steps against specific threat actors.
- Data, data and more data – Networks, apps, hosts, and any other security systems should be centralized in a single SIEM platform with highly detailed logs and high retention time. Having more data assists the threat hunter in detecting long-term trends and gathering insights and statistics for the network.
Threat hunters must understand a technique within the context of forensic evidence.
If we look at things from the threat actor’s perspective: When an infection starts, the threat actor begins to explore the network to gain an understanding where they “landed” – which hosts are visible from each endpoint, where the threat actor could go from a particular location, which crown jewels are accessible in the network, and more. The threat actor must answer all these questions to maximize the impact of the infection. These actions leave their mark on the endpoint – and that’s where the threat hunter’s work begins. From the threat hunter’s perspective, it is the hunter’s task to hunt for evidence of all this threat actor activity – based on any outliers that deviate from the established baselines.
Life Cycle of a Threat Hunting Process
The threat hunting process includes several stages, including:

- Preparing baselines – First, make sure you understand your endpoint baseline. For example, are you familiar with which applications are installed on the endpoints? Do you check for policy violations, e.g., do users bypass your local admin restrictions? Then, do the same for your network baseline. For example, what kind of protocols are communicating in the network? Are there inbound communications to your network to or from suspicious ports?
- Developing a clear hypothesis – What exactly does the threat hunter search for? Having a clear hypothesis allows you to answer this question easily. If the hypothesis is not clear, you may end up wasting valuable time. (While there does exist the possibility of conducting a hypothesis-less hunt, mostly hunters will need to be focused on a specific hypothesis to identify evidence of infection.)
- Executing the hunt within a timeframe – Execute the hunt; and retrieve and analyze results using any relevant data (live or historic). Hunts shouldn’t take forever. Set a timeframe for each hunt and remember to quit the hunt if there is no evidence of infection. This might be challenging, but remember – you are looking for evidence based on a hypothesis that might not be true.
- Validation of results – Validate the identified events to determine and separate false positive detections from data that matches the hypothesis.
- Receiving feedback & repeating hunts – Enhance the efficiency of future hunts and improve hunting procedures. Some hunts can be transformed into detection rules; others cannot. It is important to repeat hunts periodically using either automated or manual processes, and by leveraging detection rules.
Building a Threat Hunting Capability for Your Enterprise
Most cyber hunting activities must be performed by skilled hunters who have the relevant expertise, as this is an approach that combines an in-depth understanding of security tools, analytics, and threat intelligence – with human analytical skills and strong technical instincts. (The exception is IOC hunting, which is the only type of threat hunting that does not require extensive technical knowledge.)
Threat hunters need extensive knowledge of baselining networking and operating system internals because they need to “deep dive” into many areas within the environment and investigate operating system (OS) artifacts. Hunters also need forensics skills – as they must understand attack flows and identify the relevant compromise footprints indicating infection.
Some security leaders settle for allocating cyber hunting activities to senior security analysts as a side activity – rather than having a dedicated threat hunting team. This severely impacts the quality of what threat hunting can provide. True threat hunting capabilities require a significant investment of time and effort in both threat hunting preparations and their execution.
Threat hunting services can be developed in-house – or an enterprise can work with a consultant who provides advanced Managed Detection & Response (MDR) security services and has broad expertise in threat hunting. The advantage of an in-house team is that they know your system well, while the advantage of consultants is that they bring to the table their experience and a broader perspective. Either way, what is key is having a dedicated threat hunting team. An advanced Managed Security Services Provider (MSSP) like CyberProof can help ensure you are set up appropriately and have the necessary threat hunting capabilities to keep your organization safe.
To learn more about how threat hunting can be leveraged to protect your enterprise, contact CyberProof’s dedicated threat hunting team at: hunters@cyberproof.com.









