Basic Authentication, as its name suggests, is the most basic authentication protocol – providing a User-Password form of authentication without any additional, more advanced type of identity validation support.
Basic Authentication poses a risk to your organization’s data. The number of threats that exploit Basic Authentication continues to increase – and, as a result, any organization relying on Basic Authentication is opening itself up to a potential cyber attack. This reality was brought to the forefront of CyberProof’s investigations recently. New information became available that highlighted just how dangerous Basic Authentication could be to the safety of an organization’s data, after a recent Microsoft report led CyberProof’s team to learn more about the nature of this threat.
Microsoft Reports a Large-Scale Business Email Compromise (BEC) Campaign
In June 2021, Microsoft released a report highlighting a large-scale business email compromise (BEC) campaign that they had uncovered and disrupted.
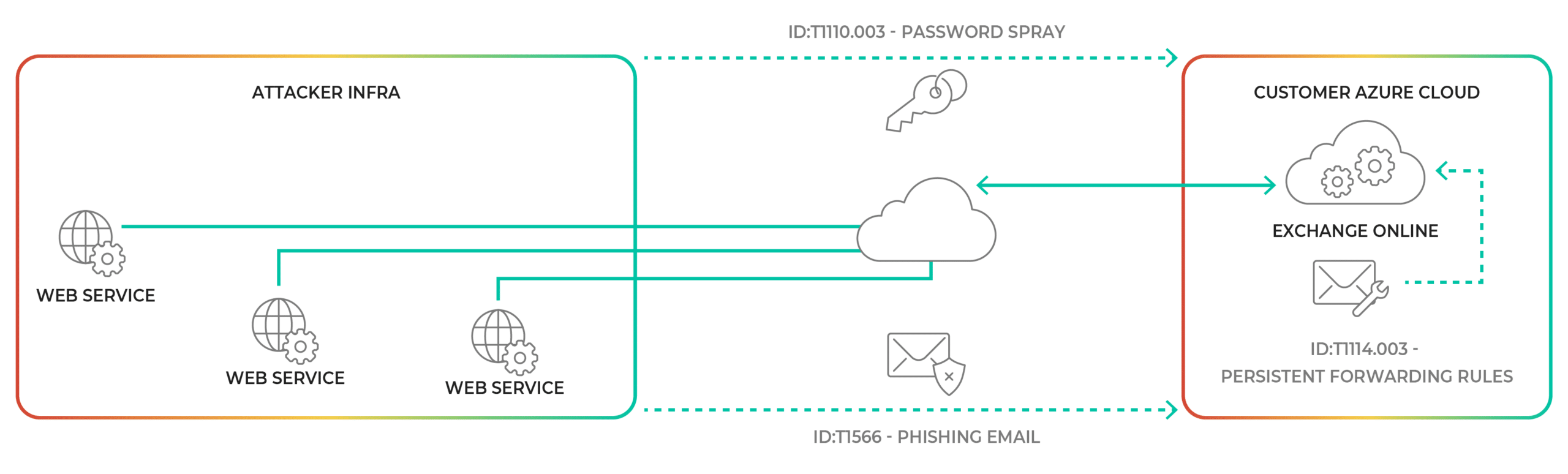
The infrastructure of the BEC campaign was hosted in multiple web services. Attackers used this cloud-based infrastructure to compromise mailboxes via phishing emails, and added forwarding rules to the compromised mailboxes – enabling the attackers to get access to emails about financial transactions.
The use of infrastructure hosted in multiple web services allowed attackers to operate stealthily, as is characteristic in BEC campaigns. The attackers performed discrete activities for different IPs and timeframes, making it harder for researchers to correlate seemingly disparate activities as a single operation.
Properties of the BAV2ROPC BEC campaign’s infrastructure
Basic Authentication – Abusing Legacy Email Protocols for “Account Check”
One of the findings in Microsoft’s report is related to the abuse of legacy email protocols for “account check.”
Account check is done in a pattern of spraying usernames and passwords from a predefined list. (These are usually dumps of organizational email IDs and easy-to-guess passwords.)
Legacy email protocols such as IMAP/POP3 – even with added support for modern authentication – still do not support Multi-Factor Authentication (MFA). (See Microsoft’s reference here.) When used against Exchange Online, they result in an ROPC OAuth flow – which allows an application to sign a user in by directly handling their password. This returns an “invalid_grant” in cases where Multi-Factor Authentication (MFA) is enabled, so no MFA notification is sent.
The number of threats that exploit Basic Authentication continues to increase – and, as a result, any organization relying on Basic Authentication is opening itself up to a potential cyber attack.
The number of threats that exploit Basic Authentication continues to increase – and, as a result, any organization relying on Basic Authentication is opening itself up to a potential cyber attack.
Microsoft’s researchers identified three Indicators of Compromise (IOCs):
- Credential checks with user-agent “BAV2ROPC” – which is likely a codebase using legacy protocols like IMAP/POP3 – against Exchange Online.
- Forwarding rule creations with Chrome version 79.
- Email exfiltration with a POP3/IMAP client for selected targets.
Microsoft Reports that Threat Actor DEV-0343 Also Uses Basic Authentication
On October 11, 2021, Microsoft published another report related to an Iranian threat actor named DEV-0343. The report stated:
“MSTIC has observed DEV-0343 conducting extensive password spraying against more than 250 Office 365 tenants, with a focus on US and Israeli defense technology companies, Persian Gulf ports of entry, and global maritime transportation companies with a business presence in the Middle East. Less than 20 of the targeted tenants were successfully compromised, but DEV-0343 continues to evolve their techniques to refine attacks.”
The interesting point here is that the threat actors used Exchange “active sync” endpoint for “account check” – which behaves the same way as IMAP, i.e., using basic authentication.
More than 97 percent of credential stuffing attacks use legacy authentication.
The report further stated:
“DEV-0343 operators typically target two Exchange endpoints – Autodiscover and ActiveSync – as a feature of the enumeration/password spray tool they use. This allows DEV-0343 to validate active accounts and passwords, and further refine their password spray activity.”
According to a different Microsoft report, analysis of Azure Active Directory (Azure AD), traffic revealed the following:
- More than 99 percent of password spray attacks use legacy authentication protocols.
- More than 97 percent of credential stuffing attacks use legacy authentication.
- Azure AD accounts in organizations that have disabled legacy authentication experience 67 percent fewer compromises than those where legacy authentication is enabled.
CyberProof’s Observations – Mass Password Spray
In several customer environments in different geolocations, the CyberProof security team observed multiple instances of mass failed login attempts for different users. This was usually a case of one or two attempts for each user, in a pattern associated with a password spray attack.
The user agent behind the login attempts observed by CyberProof was also BAV2ROPC, the same as mentioned by Microsoft. The user agent used IMAP protocol, which is used by email clients to sync the mailbox content from Exchange.
In the cases identified by CyberProof, blocking the source IP was not an option due to the nature of the attack, which was distributed from various proxy IPs. This was achieved either by using anonymous services or by using hijacked devices. Each request was coordinated to be sent from a different IP and geolocation, to avoid detection. A second factor was also not relevant, due to the use of basic authentication.

The Analyst’s View – Basic Authentication is Being Exploited as an Initial Access Gathering Method
These activities cannot be correlated to each other. However, we can point out that this method has become popular – and that it is being adopted as an initial access gathering method.
Moreover, there are a few services available with basic authentication, including PowerShell online and Autodiscover – and these can be utilized for discovery. These services have a long history of being abused for malicious purposes.
On several occasions, Microsoft has announced its intent to disable these protocols, but these changes have been postponed, time after time. This suggests the wide impact that disabling Basic Authentication has on legacy systems and the difficulty of replacing them with more modern kinds of authentication.
The last Microsoft update released on September 23 mentions a new due date for disabling Basic Authentication of October 1, 2022.
Microsoft announced its intent to disable these protocols, but these changes have been postponed, time after time. This suggests the wide impact that disabling Basic Authentication has on legacy systems.
Recommendations
To prevent attacks that exploit Basic Authentication, we highly recommend reviewing Microsoft’s recommendations – including:
- Disable the use of legacy protocols for all accounts – excluding service accounts that utilize these protocols to be compatible with legacy systems.
- Disabling Exchange Active Sync can impact some email clients, especially native iOS clients.
- Configure legacy applications with app passwords, a workaround for clients that do not support MFA.
- Monitor successful login attempts from the user agent BAV2ROPC. Exclude legitimate logins that usually come from service accounts used for legacy systems. (SIEM detection logic: Azure AD successful login event AND user agent is equal to BAV2ROPC.)
- Review this Microsoft advisory, regarding the end of the use of basic authentication.
Want to learn more about how to reduce the risk of cyber attacks and protect the safety of your organization’s data? Contact CyberProof’s experts today!
Note: This article was edited after original publication to include several corrections and clarifications.