Businesses have quickly adapted to utilizing new communication technologies, in this COVID-19 era. Zoom, one of the popular conferencing platforms before the outbreak, is now being used by individuals as well, for interacting with family and friends.
Cybercriminals, who always try to leverage global trends to launch campaigns for their own gain, are now taking advantage of Zoom users by dropping malware, gathering credentials and collecting personal or business information. In the past few weeks there has been a significant increase in domain registrations containing the word ‘zoom’. Another common theme has been “Zoom-bombing” attacks, where attackers join meetings and harass attendees.
Looking at hacking communities, we have seen discussions around Zoom, where threat actors show interest in specifically targeting Zoom by joining random meetings to interfere with Zoom sessions. Threat actors also published leaked meeting information along with tools created allowing other threat actors to find meetings on their own.
Most threat actors are Zoom bombing recreationally because they are bored during their self-quarantine at home. Others though, have made the attacks personal, claiming they want to troll teachers and classmates.
Discussions about hacking Zoom
Threat actors are asking for help on how to hack Zoom at an increasing rate. This could be because security researchers have recently found vulnerabilities both on Zoom’s Windows and MacOS clients that allow attackers to join meetings and, in some cases, even control users’ microphone and camera.
We have also witnessed other users who said they were asked to conduct a Denial-of-service (DDoS) attack on Zoom and some Telegram users asked for Zoom accounts in channels dedicated for sharing leaked data.
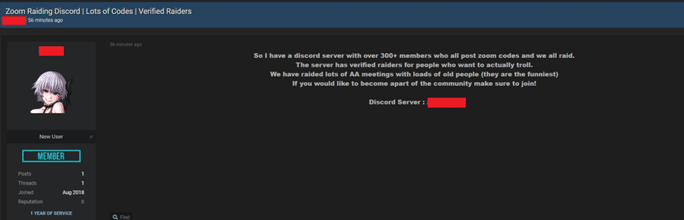
Threat actors have gone one step further, creating dedicated Discord servers to share Zoom hacking techniques and organize coordinated attacks to troll users. Discord, an instant messaging platform that is used widely in gaming communities, has become a very popular communication platform amongst cybercriminals in recent years.
Threat actors share tools to find Zoom meetings
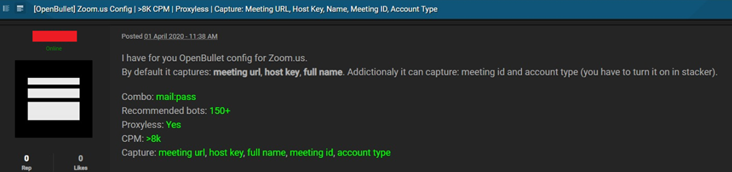
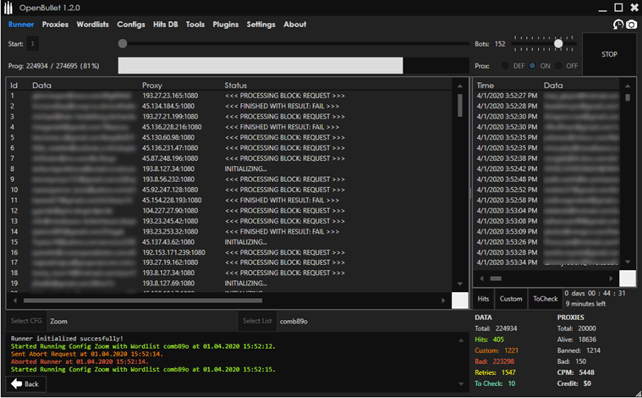
A few days after security researchers announced a new tool that bypasses the mechanism of Zoom to block automated scans to find meeting IDs, members of prominent hacking forums have started to share tools that can bypass the Zoom scan blocker as well. The threat actors have shared Zoom configuration files for a known tool called OpenBullet, used by threat actors to execute credential stuffing attacks on web applications.
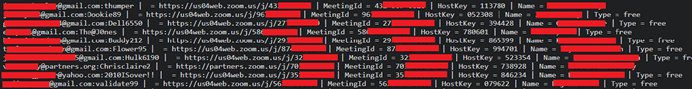
One of the threat actors claims that their configuration file allows users to perform 8,000 checks per minute (CPM) – collecting Meeting URL addresses, Host Keys, Host Names, Meeting IDs and Account Types when a valid meeting is found. The researchers’ tool though, can find more information about the meetings including their date and time, the name of the meeting organizer, and any information supplied by the meeting organizer about the topic of the meeting.
Another user on the same hacking forum published a configuration file performing about 500-600 CPM, without details about the final output. Both forum posts received responses with positive feedback, saying the configuration files worked and they were able to find Zoom meetings.
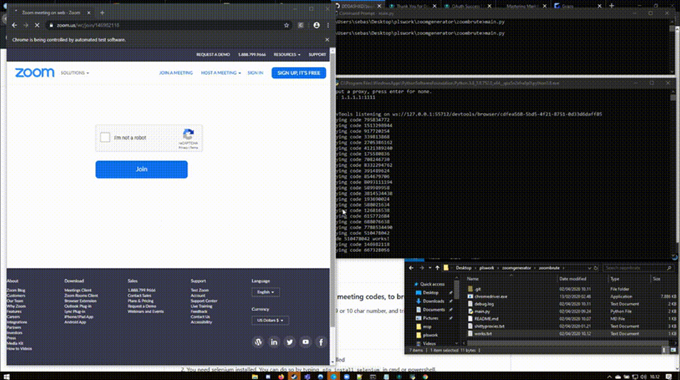
One forum member shared a script that generates random Zoom meeting codes to find and conduct brute force attacks on meetings. The script generates a random 9 or 10 character code written in python and it outputs all the valid URLs found.
Leaked Zoom meetings information
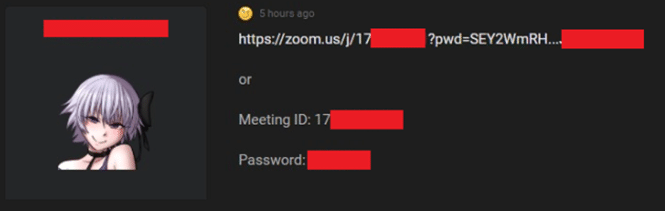
Using these tools and methods, members in hacking communities also share leaked information such as Meeting IDs, join links, host names, Hostkeys, and even user credentials.
Zoom has taken action by setting automatic password requirements for meeting, even in the lowest tiers of the platform.. “We’re always striving to deliver our users a secure virtual meeting environment,” Zoom said in a statement to The Verge. “Effective April 5, we are enabling passwords and virtual waiting rooms by default for our Free Basic and Single Pro users. We strongly encourage all users to implement passwords for all of their meetings.”
CyberProof’s Threat Intelligence team will continue to monitor the hacking communities to learn about new developments. If you have any questions about steps you can take for your organization, please reach out.