
Case Study - Construction
OT/IoT monitoring improves threat coverage across multiple networks & endpoints
Download the PDFAbout the client
A global real estate group required assistance in developing a next-generation Security Operations Center (SOC) for Building Management Systems (BMS) that would secure their IT, OT and IoT systems and environments.
The client's challenge
The client was interested in developing a scalable cyber security monitoring & detection solution that would provide an overview of their threat landscape as well as provide timely notification when IT, OT, and IoT systems became vulnerable or turned into potential cyber security threats. They sought a partner to provide systematic and rigorous evaluations of cyber risks posed by the adoption of OT and IoT systems and their integration with IT and cloud systems. It was also important to the client to have the capability to rapidly isolate these environments & systems in cases involving a potential threat.
Other areas in which the client wanted support included:
- Securing critical BMS systems using Deep Packet Inspection for ICS/SCADA Protocols including HVAC, electrical systems, elevators, water, parking lot systems, temperature control systems and developing documents and processes for overall architecture and design.
- Protecting high voltage power supply systems (securing the IEC 61850 protocol) and monitoring various HazMat sensors.
- Ensuring real-time visibility, monitoring and detection of threats in the organization’s cloud infrastructure – which interacts with OT and IoT systems and sites.
Benefits
- Single view & control point for both IT and OT environments
- Integrated IT and OT SOC operations
- Shorter time to detect and respond to security incidents
- Fewer false positives and reduced incident dwell time
- Real-time visibility with custom views and dashboards
- Aligned with industry standards and compliance requirements including IEC/ISO and NIST

Our solution
CyberProof worked closely with the client and third-party vendors to perform IT and OT security assessments – analyzing the client’s assets, documentation, processes, and the existing controls. Initial assessments during the onboarding phase provided a detailed network design architecture for all assets and associated ports, connections, protocols, and vulnerabilities – including gaps in people, processes and technologies required for maintaining their cyber security posture.
CyberProof partnered with ICS/SCADA technology vendors for the development and implementation of new hardware and software solutions per the approved architecture. We installed and configured the necessary hardware sensors, intrusion detection system (IDS), and agents to collect logs in real time from BMS systems (i.e., both IT and OT systems) and sent data to the Cyberproof Defense Center (CDC) platform.
Our solution for this client included the following:
- The CyberProof Defense Center (CDC) platform provided SOC orchestration, automation, and response capabilities. The CDC integrates with the SIEM to ingest security alerts and connects with various other technologies such as vulnerability management tools, incident workflow management tools, and more to orchestrate and automate operational activities.
- The CDC Platform provided the single pane of glass view for IT, OT, and IoT environments that the organization needed (including cloud and SaaS environments).
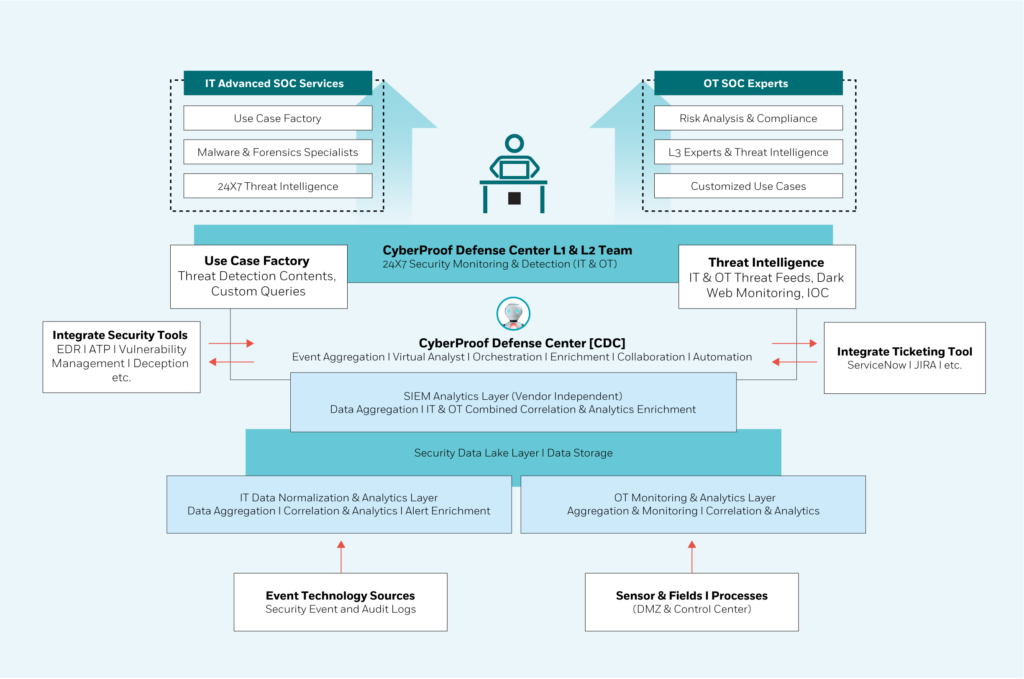
Architecture diagram
Further Information
- CyberProof’s customized engagement model directly addressed the client’s primary needs. The CDC platform imported logs from the client’s SIEM and provide alert enrichment and orchestration using CyberProof’s virtual bot, SeeMo.
- The CDC platform integrates CyberProof Threat Intelligence feeds and digitized playbooks to provide rapid incident detection and response. It also integrates Open Source and Closed Source tools such as VirusTotal, Skybox, and AbuseIPDB to enrich the response. This provided the client with optimized performance, continuous event enrichment, and a single pane of glass view – enabling the operations team to act faster and make data-driven decisions.
- The CDC platform is equipped with IT and OT playbooks and use cases that drive automation. This helped the client decrease Mean Time to Detect & Respond.
- CyberProof conducted test cases pertaining to possible cyber attacks on the BMS environment to ensure that all systems are hardened and under continuous monitoring.
- The client’s products & services were designed to be in compliance with IEC/ISO and NIST policy for IT and OT assets.

Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.
SPEAK WITH AN EXPERT






