Executive Summary
The Akira ransomware group is one of the most sophisticated and active ransomware groups we’ve observed and continues to be one of the top prolific groups, estimated to have targeted over 300 organizations globally. The group has undergone significant changes over the last 2 years moving from early adoption and usage of Rust programmed encryptors to targeting multiple vulnerabilities in an environment.
Recent reports from Bleeping Computer on the group documents the use of an unsecured webcam to launch encryption attacks. Other public research shows that from November 13 to 14 2024, the Akira ransomware group posted over 30 new victims on their data leak site, marking their highest single-day total since they began operations in March 2023. In 2024, the group was later identified as targeting vulnerabilities in SonicWall (CVE-2024-40766), Juniper, and Veeam.
The ransomware gang was first cited in early 2023 because they were targeting Windows users but in the past year has also become known to target VMware ESXi virtual machines (CVE-2024-37085). In mid 2023, researchers uncovered that the group was targeting Cisco VPNs without MFA and that Akira’s cryptocurrency transactions linked former Conti operatives to their group.
Technical Details
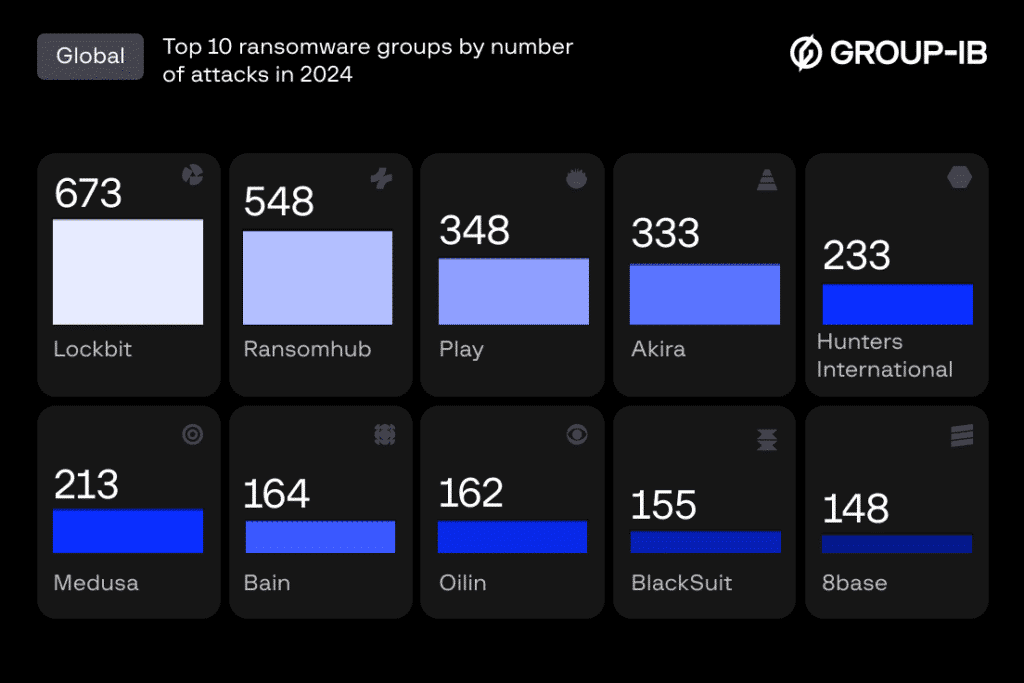
Group IB lists Akira in top 10 ransomware groups in 2024
BitDefender recently reported that as of April 2024, it was estimated that the Akira ransomware group had collected over 42 million USD in ransom payments. A CISA advisory from April 2024, shared details about Akira threat actors leveraging tools such as FileZilla, WinRAR, WinSCP, and RClone to exfiltrate data. To establish command and control channels, these threat actors also leverage readily available tools like AnyDesk, MobaXterm, RustDesk, Ngrok, and Cloudflare Tunnel, enabling exfiltration through various protocols such as File Transfer Protocol (FTP), Secure File Transfer Protocol (SFTP), and cloud storage services like Mega to connect to exfiltration servers. This wide range of off-the-shelf tools used by Akira operators poses serious concern as they try to stay under the radar and quickly navigate through victim networks until they gain a maximum foothold.
Akira encryptors are programmed to encrypt files on Windows and Linux platforms. Below are some of the command line arguments taken by Akira encryptors giving attackers different choices for execution:
| Command Line Parameters | Activity |
| -p – – encryption_path | Encrypts the files in the given path |
| -s – -share_file | Encrypts the share files |
| -n – -encryption_percent | Encrypts the given percentage of the files |
| – -remote | Remote host |
| -localonly | Only target local files. |
| -e, –exclude | Files to exclude from encryption. |
| -l | Display log file. |
Akira encryptors is programmed to perform partial encryption for faster encryption leaving users’ data corrupted.
Akira uses ChaCha20 stream cipher for file encryption and it generates 32-bit random bytes for the ChaCha20 key and another 8 bytes for ChaCha20 nonce.
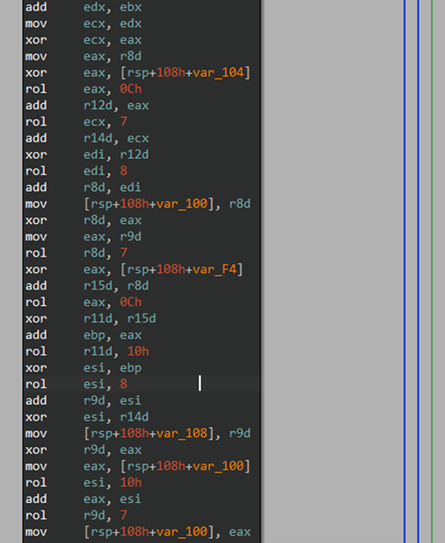
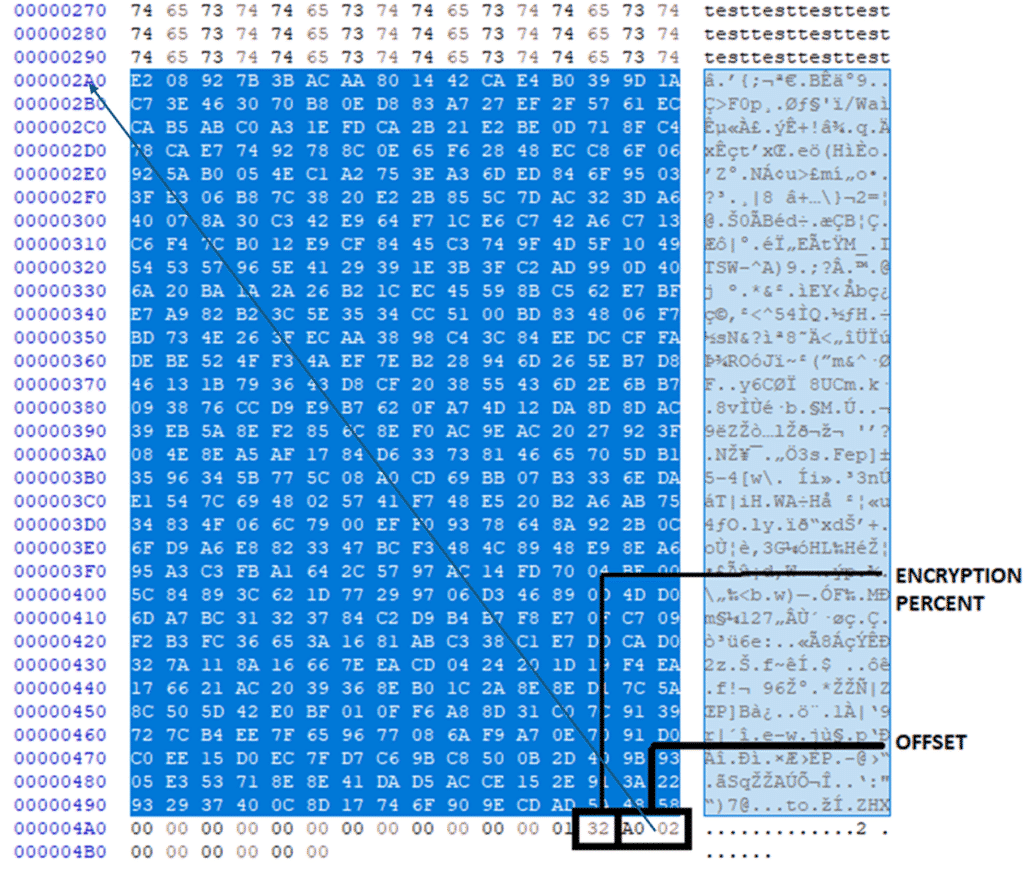
The Akira encryptor reviewed was seen encrypting 50% (see below: 32 in hex) based on file type and size and adds .akira extension. The encrypted key (highlighted in blue) is appended to all the encrypted files. Post encryption, we can see the starting of the encryptor stores value of encryption percent and the start of the key location as shown below.
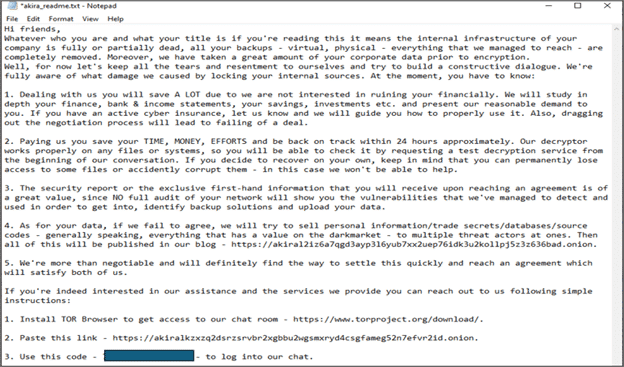
Below is a copy of an Akira ransom note detailing how they can be contacted by victims:
The image below shows Akira’s Data leak site used by the group to post details on targeted organizations:
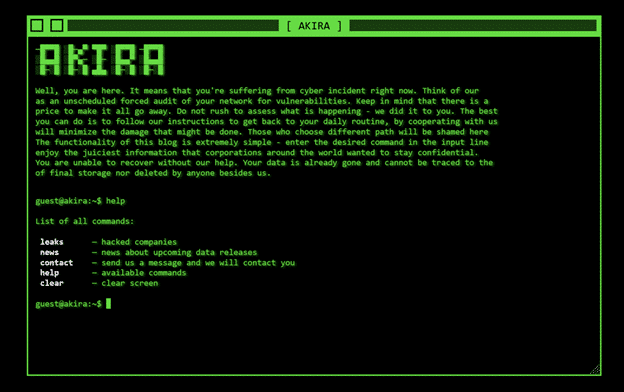
Akira Data Leak Site
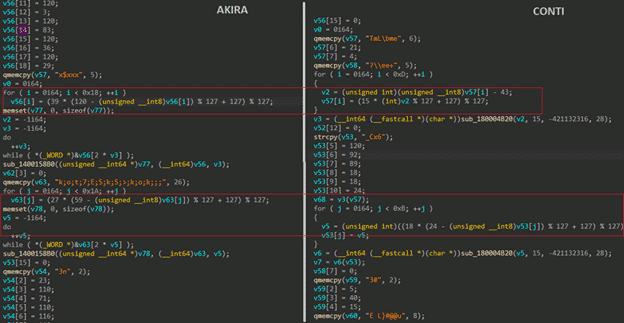
Akira and Conti Share Code Relation
Multiple reports highlight that Akira may have been born from Conti leaked source code. Below the code snippets from Conti and Akira shows some level of similarity in their string obfuscation functions:
Indicators of Compromise
- 235a90ec7f23f0836a58b509ca9dae98
- 0544137574179494761d395005175510
- 2ddb664a99000837bb9975fb8aa5796b
- d50cac4d6287863144292c6e0bd01ad6
- 3a739db5d5b9d5710aae379a2e0437dc
- aaf295f600b8d6b211880e458dac8350
- 9a5ff344263aa79121b60730ebbc201d
- 604ea52ac70d5189504788be828d1589
- 68729b85aa01cd8c9f4ccd137ddde137
- 2918b9ddaf12a57f6710c07515b27a8b
- 834f137f9039041bccb4b414154a596c
- c0a5f20bf77fda622bc93df6caccc626
- ab6a985dbef013596ac79ca5117ef77c
- 696a86a4c569590b0522664924db7c90
- 6b03b31c8cbd4a0a5829b63d16936ed3
- 510b7b359363eadc7910d721f04d80a8
- 3065f86823e429728a9adb21863414a2
- 2d81b463c7c84ac3bc0a1cf9b1105798
- 71b80a24a2b62b34494bdefce5723624
- 7d827558e7841cc2887fc99537c1c97e
- eefcd1ab5b3638c870730e459d3545ed
- cb9c73b52474adb4a24a2a17daa2b95a
- 7ca94d84f4a02fb1f608818c1c3ab62d
- b6162bebd1daab783d85c498721c60ff
- 71ab9950464359366b9d96c9f576a468
- b3e63badb7006dfe9602ce6fb876cb90
- d25890a2e967a17ff3dad8a70bfdd832
- b666ea987c7dff545e984ad88ce80a9b
- 34ad4ab24152c2bca2a4aa23f847c4d1
- 503f112e243519a1b9e0344499561908
- 0c30fdc297c54753166d572ed04d1d6b
- 302f76897e4e5c8c98a52a38c4c98443
- a0f2727dd11b0f5ced13eadc3d5bba73
- d68a565f1a5962ea081a212b2e7c36e2
- 43351ce424c9a72fcb47de7da7b368c3
- 825620363d5ff8e4d820a402bfcb425d
- 8ef468f21842ee03e1c5a41a6fef6bba
- 913ad33912e8d074a44010b9f6380969
- 2acf0461cb310ad4109cce68e4c07afe
- bd3350d018170b7f45ea7ec5375f534e
- ed46a267d7725e0e1ed956a5e441da8a
Conclusion
Akira proved to be just another sophisticated ransomware group that has constantly challenged organizations for financial gains by targeting multiple vulnerabilities and abusing multiple legitimate applications during different stages of kill chain.
A joint security advisory published Feb. 19 2025 by the FBI and the Cybersecurity and Infrastructure Security Agency, AA25-050A, has warned organizations around the world of a dangerous ransomware group known as Ghost, which is carrying out ongoing attacks targeting multiple industry sectors across more than 70 countries. The advisory has some techniques that overlap with different threat groups. Hence to strengthen their overall security posture and reduce the risk of a data breach, we strongly recommend organizations invest in employee training and threat hunting to allow security teams to proactively identify and address threats that might evade standard security measures. We predict ransomware groups to continue to evolve posing risks to organization business in 2025.
Recommendations
- Ensure implementing Multi-Factor Authentication (MFA) for all accounts and applications (ie VPNs, etc)
- Implement regularly scheduled backups and recovery processes.
- Review and ensure regular patch management.
- Leverage cyber threat intelligence to stay ahead of threat actors targeting your organizations directly or through indirect business partners (mergers and acquisitions).
- Ensure regular scans using updated EDR solutions.
- Limit exposure of services by disabling unused ports.
- Segment networks to restrict lateral movement from initial infected devices and other devices in the same organization.
How CyberProof Can Help
CyberProof researchers will continue to track different human-operated ransomware groups and shall update if we find anything new or interesting in the coming weeks.
As cyber threats continue to evolve, so too must the strategies and technologies used to combat them. Threat detection is a critical component of any organization’s cybersecurity strategy. Learn how CyberProof can help your organization effectively detect and respond to cyber threats.