Tor browser is defined as a “free and open-source software browser for enabling anonymous communication.” Initially released in September 2002, Tor’s intended use is to protect the personal privacy of its users, as well as to respect their freedom and ability to conduct confidential communication, by keeping their Internet activities unmonitored.
But as with many open-source tools, the unintended consequences are the cyber security risks involved in utilizing the Tor browser inside a business network. While it has a number of benefits – especially when it comes to providing anonymity – the potential dangers raise more risks than it solves.
Let’s have a look at the main cyber security risks associated with using Tor, which include bypassing network security, connecting to criminal sites on the Dark Web, exposing the corporate network to malware infections, and associating an organization with criminal activities under investigation.
What is Tor Browser?
The word Tor is derived from the acronym for the original software project name, “The Onion Router” (TOR). Developed by the U.S. Naval Research Laboratory for military purposes to anonymize emails, today it is the most popular software available for browsing the Internet anonymously. It is free, effective, and does not require very much technical knowledge to set up.
Tor is built as a modified version of the Firefox browser. It uses Onion routing, which is a scheme based on layered encryption, to hide TCP traffic. By default, it enables continuous private browsing mode.
Tor hides information such as the user’s activity and location from entities conducting network surveillance or doing traffic analysis.
Tor’s anonymity traits make it popular among journalists, whistleblowers and political dissidents and make it attractive to malicious actors, as well. In fact, Tor has become one of the keys to accessing the Dark Web.
Tor’s anonymity traits make it popular among journalists, whistleblowers and political dissidents and make it attractive to malicious actors, as well.
Tor Hides the Source and Destination of Any Communication
Not only does Tor encrypt communication – a mechanism provided by other applications – but it also hides the source and destination of the communication by encrypting and moving traffic across different nodes located around the globe.
A node can be any computer connected to the Tor network; and any Tor user can relay traffic via any node. Each data package that leaves a user’s computer travels on a pathway through several random servers or nodes.
All Tor traffic goes through a minimum of three nodes – the Entry node, the Middle Node and the Exit node. The destination server only has knowledge of the last node, which is the only link that is unencrypted.
Due to the layers of encryption and randomization of the traffic, it is practically impossible to identify the complete path that a data packet has taken.
Be Aware of the Cyber Security Risks of Using Tor on a Business Network
When it comes to using different technologies in an organization, cyber security risk assessment and management should play a key role in the decision-making process.
While the main benefit that Tor provides is anonymity on the Internet, it comes with a long list of risks that could highly impact an organization.
As with any new tool, when it comes to using Tor, an organization should ask itself if the tool provides benefits that are worth the associated risk. What impact could it have on the business?
Bypassing Security Controls
One of the main cyber risks associated with Tor is that monitoring traffic is almost impossible – because all communication over Tor is encrypted. Therefore, an employee can use Tor to bypass all security mechanisms, policies, and controls of the organization, with very little effort.
Tor enables any corporate user to access censored content, illegal Dark Web websites, and underground marketplaces – and can even facilitate the exfiltration of proprietary data without any sort of restriction.
Perhaps Tor represents the greatest risk with regard to what’s known as “cyber insider threats” employees who exfiltrate confidential information and sell it to third parties. These third parties use it for business intelligence purposes or insider trading.
Tor is so effective for exfiltrating confidential data that in certain Dark Web forums dedicated to insider trading, new users are required to share secret information with other forum members in order to become a member. Access to the forums is provided only after the information has been successfully validated.
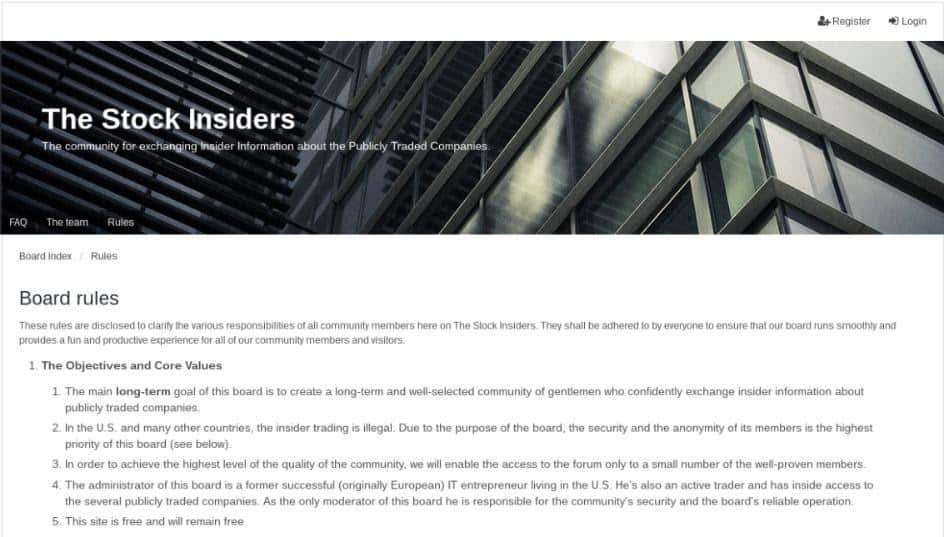
“The Stock Insiders” Dark Web Forum
Malicious Exit Nodes
Another risk relates to Tor’s use of exit nodes. All Tor traffic goes through three nodes – an Entry node, Middle node and Exit node – and users sitting on exit nodes can add malware, inject content into unencrypted HTTP traffic, or modify unencrypted binary downloads.
Bottom line: Users that download files through Tor may expose the organization’s corporate network to malware infections.
An Example: OnionDuke
One of the most prominent examples of malware distributed via a Tor exit node is OnionDuke, a new piece of malware found to have ties with Russian APT, that is distributed by threat actors through a malicious exit node.
The exit node wraps legitimate executables with malware, and this increases the attacker’s chances of bypassing security mechanisms.
Man-in-the-Middle Attack (MiTM) Attacks Can Be Used for Information Theft
Another risk is related to the fact that operators of Tor exit nodes have the ability to sniff traffic, i.e., to monitor and capture all traffic passing through their devices.
As a result, if data transiting is unencrypted – for example, the data is transiting via HTTP, FTP, or SMTP without Transport Layer Security (TLS) – operators can capture the data by means of a Man-in-the-Middle (MiTM) attack. This means credentials for personal or corporate services are constantly at risk of being stolen.
DDoS Attacks
Another cyber security risk is that once an employee starts using Tor, the organization’s servers start relaying Tor traffic. This could result in extremely high consummation of the corporate bandwidth.
If a device is relaying large amounts of Tor traffic, potentially it could overwhelm an organization’s servers. Thus, this permanently exposes the organization to a distributed denial-of-service (DDoS) attack, i.e., an attack in which an online service is made unavailable by overwhelming it with traffic from multiple sources.
Reputational Damage
Another problem of Tor use is that if a suspicious exit node’s IP address belongs to your organization, the organization may be held responsible for crimes that it did not commit – serious criminal activities such as DDoS attacks, hacks, and illegal trades.
This is because when the authorities investigate the digital tracks of a cyber criminal’s activity, they turn to the owner of any IP address they find. Many times, this IP address is an exit node of the Tor network. While the exit node may not necessarily be directly connected to the illegal activity under investigation, nonetheless, it is likely to be the first digital fingerprint the authorities come across.
Moreover, if an IP address is found to actually be connected to illicit activities, it could be annexed to a blacklist and blocked by other organizations looking to protect themselves. See, for example, https://www.dan.me.uk/tornodes.
How to protect your organization
While Tor has the benefit of providing anonymity, it opens your organization to increased risk. But detecting and completely blocking Tor in a corporate network is not an easy task.
Cyber experts can assist you in detecting and preventing the use of Tor within the corporate network using a variety of techniques. For example, various tools are available that can provide alerts to the SOC team regarding the presence of Tor traffic on the network.
Cyber experts can assist you in detecting and preventing the use of Tor within the corporate network using a variety of techniques.
It is best to implement more than one solution, to ensure your organization is protected. Here is some of what you can do:
- Microsoft Cloud App Security (MCAS) is able to provide alerts about “Activity from a Tor IP address,” which helps detect Tor traffic – but only on the Azure cloud environment.
- There are Tor IP and node lists that are publicly available, and that can be used for monitoring by various applications and network protocols including firewalls, IDS/IPS, NetFlow, and more.
- Application control systems can be used to detect and alert for Tor traffic based on process properties and behavior.
- In EDR solutions, whitelisting Tor indicators such as filename, path, or hash can help provide detection regarding the presence of the Tor browser.
If you are concerned about the robustness of your organization and its ability to protect itself from cyber attack or would like to speak with one of our experts, contact us today. We are here to help!