Research Contributors: Amit Gini, Golan Agi, Tom Saar
Executive Summary
On November 19, 2024, a meticulously crafted phishing campaign targeted an employee within a corporate environment. The attacker leveraged social engineering tactics via Microsoft Teams, masquerading as an IT technician to manipulate the victim into accessing malicious links. These links led to a compromised SharePoint folder containing a legitimate remote management tool installer (AnyDesk) and a malicious password-protected ZIP archive. Although the files were downloaded and unarchived, none were executed, thanks to swift SOC intervention and effective isolation protocols.
During Q4 2024, CyberProof responded to a cyber-attack conducted by a threat actor that CyberProof Threat Research teams have attributed with high confidence to an intrusion set referred to as Black Basta. Amongst technical indications, the incident observed by CyberProof also contained characteristics of recent campaigns attributed to BlackBasta by other researchers. This article dissects the incident’s infection chain, and the attacker’s tactics, techniques, and procedures (TTPs) while offering actionable recommendations for fortifying defenses against similar threats.
Technical Details
Threat Actor Overview: Black Basta
Black Basta is a financially motivated ransomware group, known for its dual-extortion tactics and sophisticated attack methodologies. Since its emergence, the group has targeted over 500 organizations globally, spanning critical industries such as finance, manufacturing, and professional services.
- Primary Motivations: Financial extortion through data theft and encryption.
- Targeting Trends: Recent campaigns demonstrate a growing focus on the financial sector, exploiting its critical reliance on data integrity and operational continuity.
- Operational Scope: Utilizes phishing, legitimate tools (e.g., AnyDesk), and advanced malware for stealth and persistence.
Infection Chain Analysis: Initial Access
The phishing campaign unfolded in a carefully orchestrated sequence:
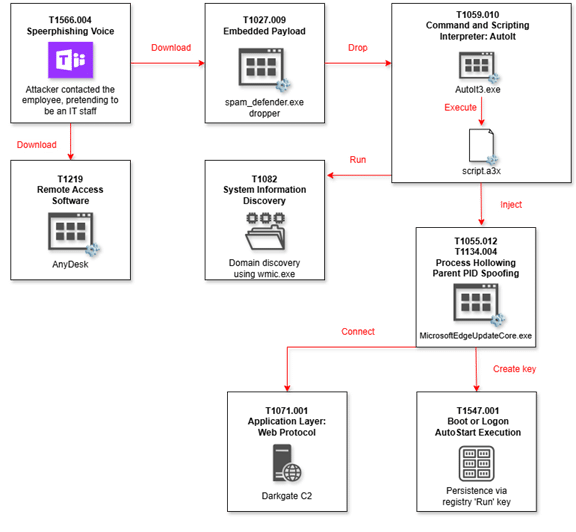
- The attack began with the threat actor, under the disguise of “Brian Hall,“ contacting the victim through Teams. Presenting himself as a member of the IT department, the attacker convinced the employee to follow links to a compromised SharePoint folder.
- The first link provided access to the AnyDesk installer, which was a legitimate file.
- Shortly after, the attacker shared a second link leading to a ZIP archive, password-protected to bypass antivirus scans. This archive contained a malicious executable,
spam_defender.exe, carefully obfuscated to appear as a legitimate AVG tool. - While the victim downloaded and extracted the ZIP, forensic evidence confirmed that none of the files were executed, effectively neutralizing the attack.
MFT analysis revealed the precise timeline of file creation and modification:
Interestingly, metadata within the MFT indicated that the ZIP file had been archived by the attacker a day prior to the phishing attempt, underscoring the premeditated nature of the attack.
Malware Characteristics
Dynamic analysis of the spam_defender.exe uncovered a malicious dropper, designed to deploy and execute an AutoIt3.exe binary alongside an encrypted .a3x script. Within the dropper, we have identified an additional PE section ($cm) embedding both an AutoIt3.exe binary and an encrypted .a3x AutoIt script.
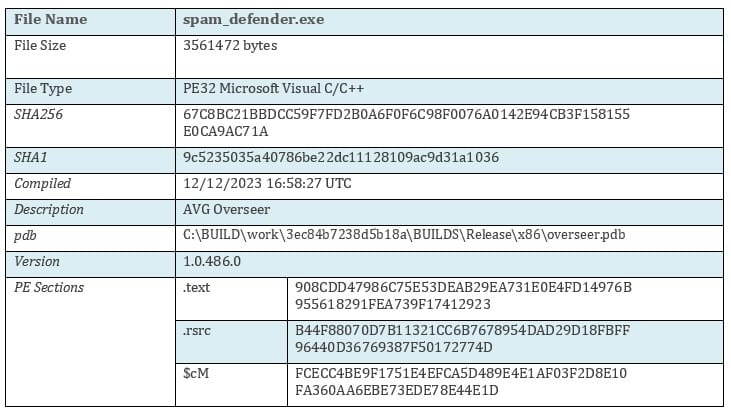
During runtime, the dropper creates a temporary directory at C:\temp\test, where it extracts and writes the AutoIt3.exe binary and .a3x script from the additional PE section.
Finally, the dropper launches AutoIt3.exe and executes the dropped .a3x script using: “C:\temp\test\Autoit3.exe C:\temp\test\script.a3x”.
Darkgate A3X Script
Once executed, the .a3x decrypts in memory. It then creates another directory with a randomized name under %ProgramData% – copies the Autoit3.exe and script .a3x, presumably for backup and redundancy purposes.
You can also find .log files that house encrypted key logs and some other encrypted files used by the malware. Initial discovery steps involve querying basic system information via WMIC, specifically invoking the command ‘cmd.exe /c wmic ComputerSystem get domain > C:\ProgramData\<RANDOM_FOLDER>\<RANDOM_FILE> ‘ to capture the domain information. The script further enumerates installed security tools by scanning system directories for EDR and AV indicators.
The .a3x script injects into a remote process. Notably, we observed the malware targeting a legitimate Microsoft binary, MicrosoftEdgeUpdateCore.exe, located in C:\Program Files )x86)\Microsoft\EdgeUpdate\XXXMicrosoftEdgeUpdateCore.exe, using it for code injection.
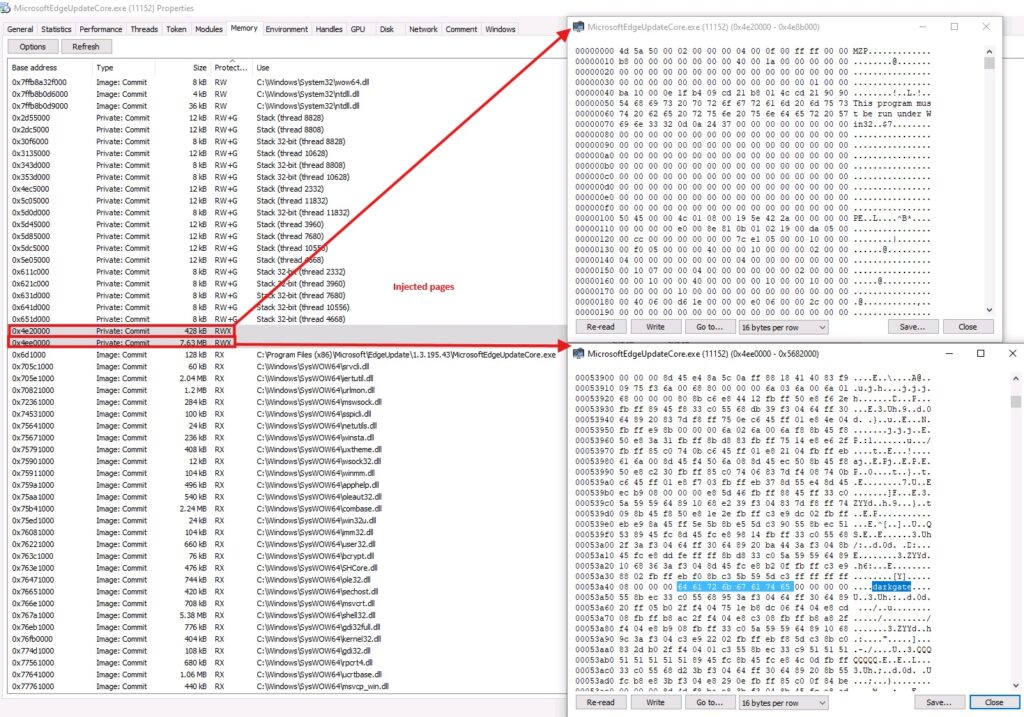
As a fallback, we noticed that in cases where the “MicrosoftEdgeUpdateCore.exe” is missing, the script searches for three more paths in order to find a suitable injection victim:
“C:\Program Files (x86)\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe”“C:\Windows\Microsoft.NET\Framework\XXX\MSBuild.exe”“C:\Program Files (x86)\Google\Update\”
Once there is a hit, and the malware chooses a victim process – the Autoit3.exe launches the victim process from disk and, as part of the defense evasion, the malware uses PPID Spoofing technique to randomize the parent process of the injected process.
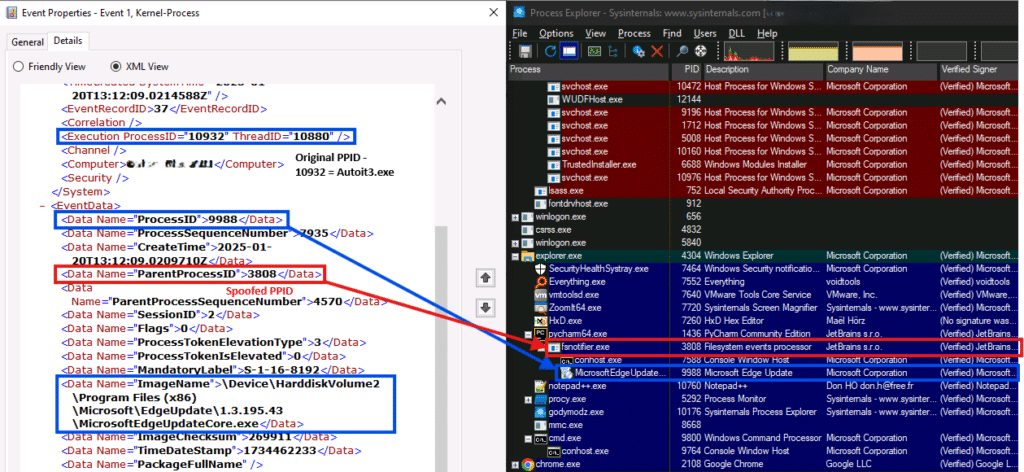
During the runtime of the malware, we regularly noticed that every 20 seconds a TCP-SYN request is sent to the C&C server. Persistence is achieved by creating a randomly named registry key under “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run/hddbhaa”, pointing to the AutoIt3.exe binary and its accompanying script “C:\temp\test\Autoit3.exe C:\temp\test\script.a3x”.
MITRE ATT&CK Mapping
The tactics employed in this phishing campaign align closely with the following entries from the MITRE ATT&CK framework:
| Tactic | Technique | Procedure | Observations | Alignment |
| Initial Access | T1566.002 (Spear Phishing Link) | Adversaries used Microsoft Teams to deliver phishing links, impersonating IT support to share malicious SharePoint URLs. | Black Basta affiliates have been reported to use phishing links delivered through various communication platforms, including Microsoft Teams, to gain initial access. | High: Both scenarios involve the use of phishing links via communication platforms, impersonating trusted entities to gain initial access. |
| T1193 (Spear Phishing Attachment) | A password-protected ZIP file containing spam_defender.exe was delivered via a phishing link. | Black Basta has utilized password-protected ZIP files to deliver malicious executables, aiming to bypass security measures. | High: Both cases demonstrate the use of obfuscated attachments to evade detection mechanisms. | |
| Execution | T1204.002 (User Execution: Malicious File) | User interaction was required to execute spam_defender.exe after extraction from the ZIP file. | Black Basta relies on social engineering to prompt users to execute malicious files, leading to system compromise. | High: Dependence on user execution is a shared characteristic in both instances. |
| T1059.003 (Command and Scripting Interpreter) | WMIC commands were employed for system discovery and domain enumeration post-compromise. | Black Basta has been observed using WMIC and other scripting interpreters for reconnaissance and execution purposes. | High: Both utilize scripting interpreters for system discovery and command execution. | |
| Persistence | T1547.001 (Registry Run Keys/Startup Folder) | A registry key was created under HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run to maintain persistence. | Black Basta commonly employs registry modifications to ensure persistence across system reboots. | High: Both involve registry-based persistence mechanisms. |
| Defense Evasion | T1070.004 (File Deletion) | Temporary files were deleted post-execution to hinder forensic analysis. | Black Basta is known to delete logs and temporary files to reduce their forensic footprint. | High: Both demonstrate efforts to impede forensic investigations through file deletion. |
| T1562.001 (Impair Defenses) | The use of encrypted payloads and obfuscated droppers allowed the bypassing of antivirus and endpoint detection systems. | Black Basta employs encryption and obfuscation techniques to evade security defenses. | High: Both utilize methods to impair and bypass security defenses. | |
| Discovery | T1082 (System Information Discovery) | WMIC was used to gather system information, including hostname and domain details. | Black Basta conducts system information discovery to tailor their attacks to the victim’s environment. | High: Both perform system information discovery to facilitate further actions. |
| T1518.001 (Software Discovery: Security Tools) | The malware enumerated installed antivirus and endpoint detection tools to adapt its behavior accordingly. | Black Basta identifies installed security software to disable or evade them during attacks. | High: Both involve discovery of security tools to adjust tactics for evasion. | |
| Lateral Movement | T1021.001 (Remote Desktop Protocol) | AnyDesk was used as part of the attack delivery vector, posing as a legitimate IT tool. | Black Basta has utilized RDP for lateral movement within compromised networks. | High: Clear evidence of alignment in the use of legitimate remote access software for stealthy lateral movement. |
| Command and Control | T1071.001 (Web Protocols) | Outbound TCP-SYN traffic to a command and control server was observed, indicating potential use of web protocols for communication. | Black Basta uses web-based protocols for command and control communications to blend with normal traffic. | High: Both employ web protocols for command and control to maintain stealth. |
| T1573.001 (Encrypted Channel) | Command and control communications were likely encrypted to prevent detection and analysis. | Black Basta encrypts C2 traffic to secure communications and evade interception. | High: Both utilize encrypted channels to protect command and control communications |
Indicators of Compromise
| IOC | Name |
| 67c8bc21bbdcc59f7fd2b0a6f0f6c98f0076a0142e94cb3f158155e0ca9ac71a | spam_defender.exe |
| ebbe6a9e1188e2ee1651b5c68b6b508fb52b9e8896dbbeb0f4e126961ba94982 | spam_defender.zip |
| BrianHall@pereirabrito.com.br | Malicious teams contact |
| https[://]binusianorg-my[.]sharepoint.com/personal/radja_hizbullah_binus_ac_id/XXXXXX | Taken SharePoint server |
| 179.60.149.194 | C&C server |
| 4760eb1d03464ce037df0180776e80bffea5904fe3a832b258acfa4a565a1f32 | script.a3x |
Recommendations
We recommend the following to safeguard against these threats:
- Phishing Awareness Training: Regularly educate employees about social engineering tactics, including the dangers of unsolicited requests in collaboration tools like Teams.
- Access Controls: Implement strict policies for external communications, allowing only verified accounts and organizations to interact with employees on platforms like MS Teams.
- Restrict remote monitoring and management tools: It is crucial for organizations to block known RMM software that is not approved for use within their environment. In this instance the attack was successful because of the ability to download AnyDesk.exe to the desktop.
This incident illustrates the ingenuity of modern phishing campaigns and the importance of a multi-faceted defense strategy. Through a swift SOC response, in-depth forensic analysis, and proactive measures, an organization can successfully neutralize the threat before it is escalated. By adopting the recommendations outlined above, businesses can build resilience against similar attacks, safeguarding their digital ecosystems against evolving threats.
How CyberProof Can Help
As cyber threats continue to evolve, so too must the strategies and technologies used to combat them. Threat detection is a critical component of any organization’s cybersecurity strategy. Learn how CyberProof can help your organization effectively detect and respond to cyber threats.