We read in the news that “insiders” are behind many of the largest-scale data breaches. For example, in the Waymo vs. Uber case – which finally got settled last August – Anthony Levandowski, former Google engineer, was indicted for allegedly secretly downloading and passing along confidential files with trade secrets to Uber.
In a much lower-profile case – one that illustrates some of the complexity of dealing with cyber insider threats – Jason Needham, co-owner of a small firm called HNA Engineering, was sentenced to jail for unauthorized access of a former employee’s network. Needham left a former employer, the Allen & Hoshall engineering firm, in 2013. Three years later, a prospective customer received a proposal from his firm that was way too similar to that of Allen & Hoshall. The FBI traced the suspicious behavior back to Needham.
Yet, with all of the reports about breaches that are related to insider threats in cyber security – most of us are not sufficiently aware of what’s involved.
Insider Threat Defined
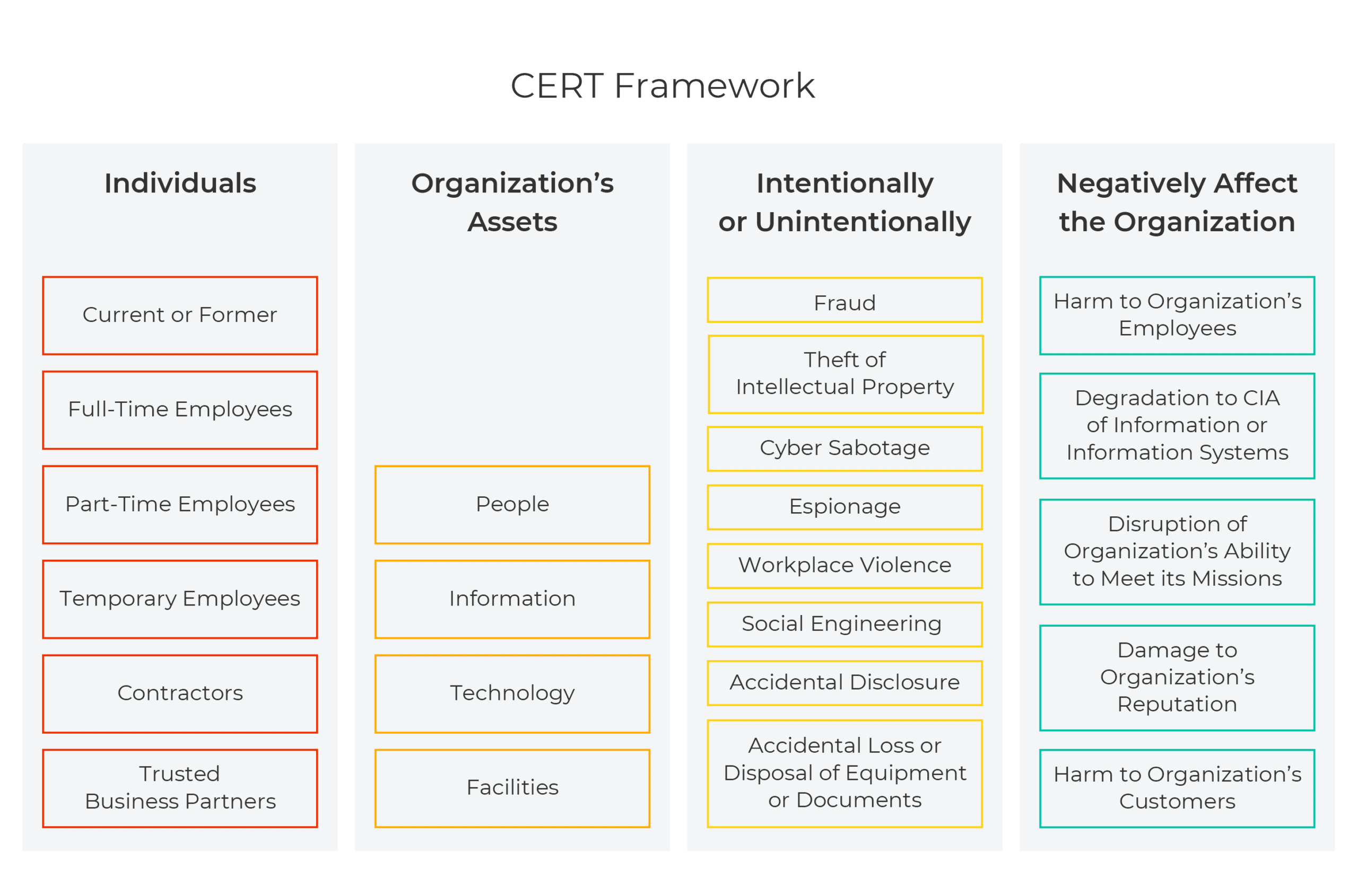
Insider threat actors can include people who are currently employees and those who used to be employees – as well as “outsiders” with access to an organization’s internal environment, such as contractors, vendors, and suppliers.
Generally, an attack by an insider falls into one of the following categories:
- Negligence – Someone who compromises data by mistake, generally due to bad cyber hygiene
- Malicious Intent – Someone who compromises data purposely
- Infiltration – A compromised account or system, i.e., someone whose account was taken over by a bad actor and misused, or a system that was compromised
We Trust the People We Work With
Most organizational success is built on a foundation of trust. And yet, cyber insider threats are incredibly dangerous – and surprisingly common.
A study from the Ponemon Institute places the average cost of cyber insider threats globally at $8.76 million – a cost that generally increased the longer an insider threat took to resolve.
Have a look at some of these disturbing facts from the Verizon Insider Threat Report:
- 57% of database breaches involved insider threats within an organization
- 20% of cyber security incidents and 15% of data breaches are due to misuse of privileges
- 61% of internal actors are not in positions with a high level of access or stature
What Damage Can Insiders Cause?
Cyber insider threats can cause the same types of damage to an organization that other bad actors (criminals or malicious hackers) cause, but they are harder to catch because their activity is disguised – cloaked under the guise of normal employee activity inside the perimeter.
Insiders have the potential to cause tremendous financial loss to an organization through:
- Sabotage – Using IT to cause harm to the organization – for example, by destroying data, equipment, or harming the organization’s reputation
- Privilege Abuse – Abusing access privileges, utilizing confidential information for financial advantage – such as knowing when to buy and sell company shares by looking at financial data
- Data Leakage – Stealing sensitive data – exfiltration of anything from intellectual property to customer details for profit or malicious intent
- Fraud – Modifying data, or the stealing of information for later use – for example, identity theft to authorize transfer of funds under false pretenses
The following diagram summarizes the dangers of a cyber insider threat:
Using Cyber Security Strategy to Identify Potential Threats
Identifying when something’s gone wrong within an organization involves collecting information about employee behavior and organizational function that could be indicative of potential risk.
By tracking people, processes, and technologies using automation & orchestration technologies in a SOC, it becomes possible to identify atypical or malicious behaviors.
In other words, correlating Potential Risk Indicators (PRIs) drives real-time threat detection and allows the rapid identification of emerging insider threats. PRIs can include:
- Network activity
- Compliance cases
- Time and expense
- Personnel management
- External data
- Physical security
- Access attributes & behaviors
- Data exfiltration
Develop a Program Framework for Cyber Insider Threat Identification
In creating your organization’s cyber readiness and protection, it’s important to consider use cases that relate specifically to the insider threat.
The steps to handling a cyber attack by an insider include:
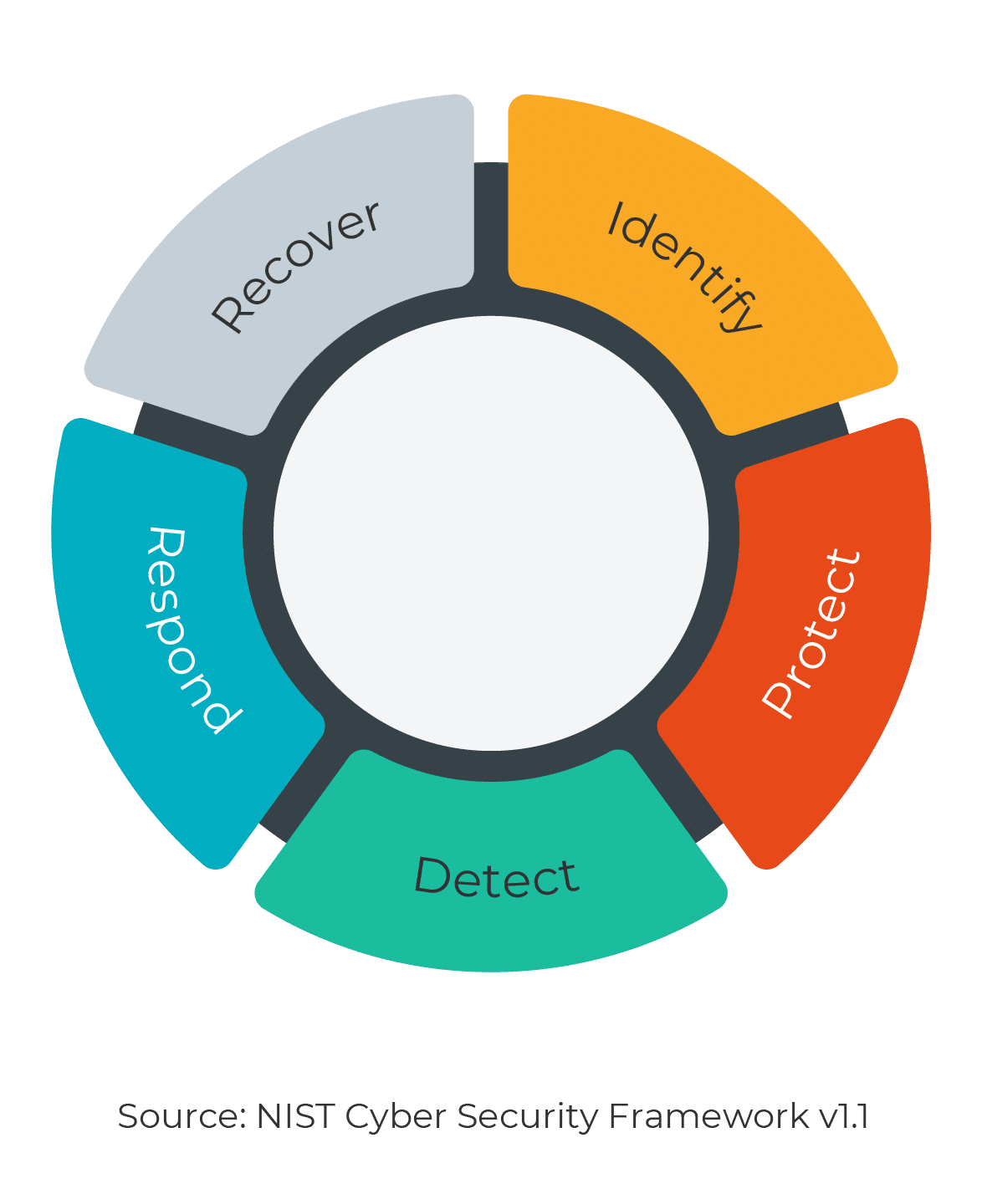
- Protect – Methods of protecting an organization include identity management and access control, staff training, effective data security processes, up-to-date information protection processes and procedures, maintenance, and implementing protective technologies. Some cyber threat intelligence tools an organization can use include log collection – meaning the tools in place to monitor logs and identify suspicious behavior – and User Behavior Analytics (UBA), which actively monitors events, identifies abnormal behavior, conducts risk scoring and prioritization, and allows an organization to take appropriate action when necessary.
- Detect – Rapid detection of anomalies and events requires continuous security monitoring and detection processes by means of a security operation center that implements proactive threat intelligence, 24/7 monitoring, a SOAR platform allows an organization to collect data from multiple sources and responds to low-level events by leveraging automation, etc.
- Respond – Real-time response requires investing ahead of time in a cyber security strategy that includes response planning, by establishing of communications processes, undergoing real-time analysis and mitigation, and initiating a cycle of ongoing improvement.
- Recover – Rapid recovery is the result of investing in recovery planning, maintaining an ongoing cycle of continued improvement, and effective communications.
Making Sense of the Data
Being prepared for the future involves forecasting advances in technology and the regulatory burdens that may impact them. This is a difficult task – and those enterprises that are most prepared will utilize the best cyber security strategies and technologies available to leverage the power of Big Data analytics.
Because an organization’s risk will never be zero, the key is to find the most efficient and effective way to manage residual risk.
The Importance of Detection & Response
While 24/7 monitoring, threat intelligence & threat hunting are key aspects in identifying and responding quickly to cyber insider threats – an equally crucial piece of the puzzle is detection & response, which allows fast handling of an insider’s attack in a way that mitigates the damage to the organization as quickly as possible.
Here at CyberProof, we utilize artificial intelligence (AI) and machine learning (ML) in a fully integrated, holistic approach to managed detection and response that allows organizations to act on alerts in near real time and minimize the risk to a business.
By working strategically to reduce response time, organizations are able to minimize the magnitude of loss caused by an attack and reduce its impact. In other words, speed and agility are crucial aspects of mitigating the cost of a cyber attack to a business.
As explained by industry thought leader Michael G. Gelles, Psy. D., in Insider Threat: Prevention, Detection, Mitigation, and Deterrence, what is necessary is “a complete roadmap for developing an insider threat program to protect an organization’s critical assets from espionage, embezzlement, sabotage, and identity theft with helpful mitigation strategies and tactics for interrupting maliciously motivated insiders intending to do harm to a company or its employees.”
The Insider Threat is a Major Use Case
Building an insider threat program that handles all cases of insider threat attack – including infiltrators, malicious actors, and negligent behavior – is key to maintaining an organization’s cyber readiness. But because of the existence of multiple credentials for each user, and the expanding scope of the IT landscape, it is an increasing security challenge to completely protect organizations against these kinds of threats.
Because it’s so difficult to detect the malicious behavior of insiders, the reality is that three-quarters of insider attacks go unnoticed. However, by putting in place a system that considers the dangers of insider threats through detection & response, it becomes possible to identify and respond to insider threats quickly – in a way that minimizes risk and mitigates damage to the business.
Want to learn more about how enhanced security operations monitoring and response services can protect your organization from insider threats? Contact CyberProof’s experts today!












