Threat actor activity in 2020 was been largely shaped by the COVID-19 pandemic – with cyber criminals exploiting the fear and uncertainty created by the pandemic for their own profit. Threat actors have been most focused on:
- Attacking the infrastructure for remote workers
- Phishing and scamming using pandemic-related themes
- Conducting ransomware attacks that target critical infrastructure
- Attacking the healthcare industry
Let’s have a closer look at each of these cyber security trends and the threats that have been most common.
Trend 1: Attacking Infrastructure for Remote Workers
VPN Attacks
As the number of virtual workers increased, the use of corporate VPNs has become increasingly risky. That’s because while VPNs give network access to remote workers – allowing them to obtain company data and applications – they can also open a door to unwanted visitors.
With the start of the pandemic, many organizations deployed new networks – including VPNs and related IT infrastructure – to cater to the large shift toward remote working. Malicious cyber actors took advantage of this mass move by exploiting publicly known vulnerabilities in VPNs and other remote-working tools and software.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert in March due to this increase in cyber security threats – with recommendations about how to make VPN connections more secure. Much of the concern about VPNs reflects the fact that VPN vulnerability exploitation is widely thought to be the initial point of compromise for a range of attacker profiles – from nation-state actors to ransomware gangs and fraudsters.
Remote Desktop Protocol (RDP) Attacks
With so many workers logging in from home, RDP has become a very common means of accessing the machines and resources at the office. And while RDP can be viewed as an easy fix to such problems, if it’s deployed insecurely, it can also become a major weakness.
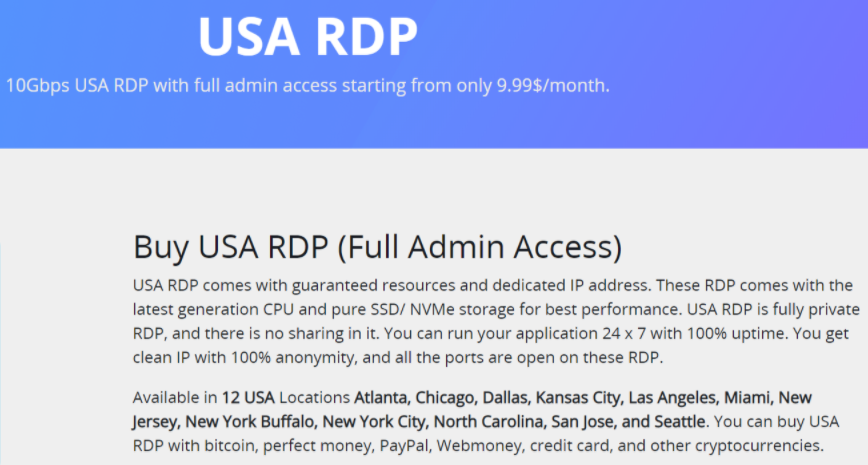
An increase was registered in the volume of RDP credentials being sold on underground markets. The following is an example of a highly reputed RDP black market:
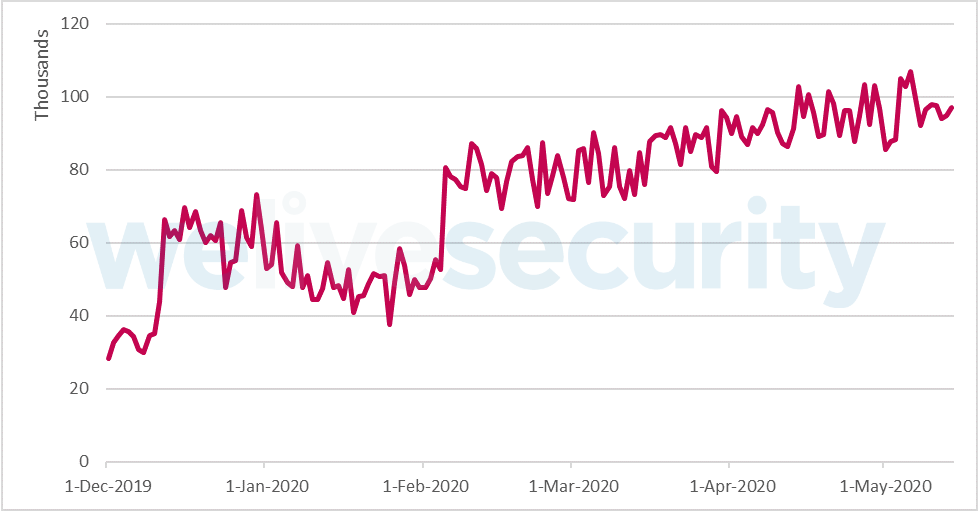
Moreover, this graph from WeLiveSecurity illustrates the increase in RDP attacks (January to June):
Despite the growing significance of RDP, organizations often neglect to improve RDP-related security configurations. Employees may use easy-to-guess passwords, with no additional layers of authentication or protection – so there is little that can stop a cyber criminal. In some cases, users may be unaware of the fact that the RDP is open – even though sometimes, simply disabling it is all that is necessary to prevent disastrous consequences.
The most common attack on RDP is brute force, which can provide a cyber criminal with valid credentials with which to access a target’s computer on the network.
Vulnerabilities in Zoom Apps
The popularity of Zoom created a huge new “attack surface” – with hackers coming at it any way they could. There have been tens of thousands of registered, Zoom-related fake domains, and large numbers of Zoom-themed malware developed and shared on the dark web.
Because of the high level of scrutiny, many vulnerabilities were found on Zoom this year – from Zoom bombing, i.e., breaking into private Zoom meetings, to arbitrary code execution. To combat these vulnerabilities, since February Zoom has released around 20 version updates.
Other teleconferencing software, like WebEx, has been the target of similar attacks as Zoom, though to a lesser degree.
Trend 2: Phishing & Scamming
As the world struggled to cope with the pandemic, cyber criminals managed to thrive – adapting their cyber security threats and exploiting the fears, financial distress, and overwhelming need for information exhibited by the general population.
Phishing
COVID-19-related spam has been the hallmark of the period surrounding the pandemic, and the fear surrounding the virus continues to fuel malware and spam.
According to BitDefender’s Mid-Year Threat Landscape Report, between January and June, four out of every ten COVID-19 themed emails were tagged as spam.
Similarly, in the same time period more than 51,000 COVID-19-related website domains were registered globally, according to Check Point.
Google detected that each day, 18 million malware and phishing emails are sent through Gmail – along with more than 240 million spam messages – all of which are related to COVID-19.
Cyber criminals designed phishing campaigns to target remote workers – luring them into mishandling their credentials – while more “classic” phishing emails, such as bank impersonations, used COVID-19 to add an extra layer of credibility to their activities. Here is one example (see Kaspersky):
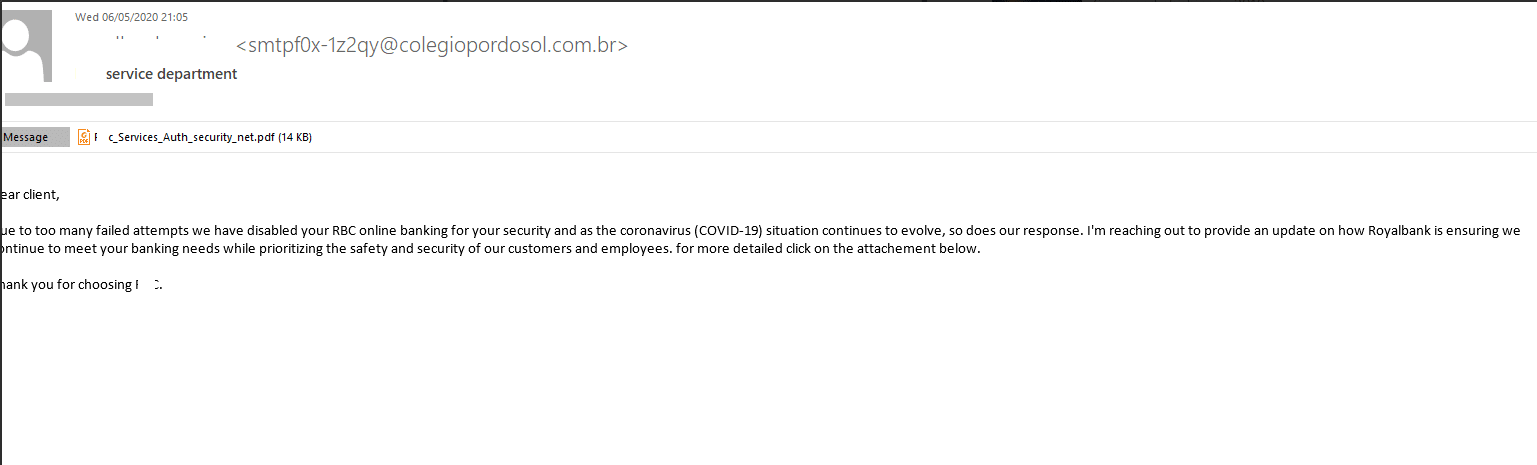
In addition to bank impersonations, a variety of other phishing email themes added COVID-19 to their repertoire, including taxes and tax refunds, human resources, newsletter subscriptions, and delivery services.
Scams
This year, a large percentage of the scams aimed at stealing personal data and money related to COVID-19.
Most scams start with emails, advertisements, text messages, or social media sites, and pretend to be governmental or financial organizations. These bring victims to fake websites that encourage them to hand over personal information. In some cases, victims’ devices are infected with malware. The following is an example of a threat actor selling fraud methods and other illegal goods on a dark web forum:
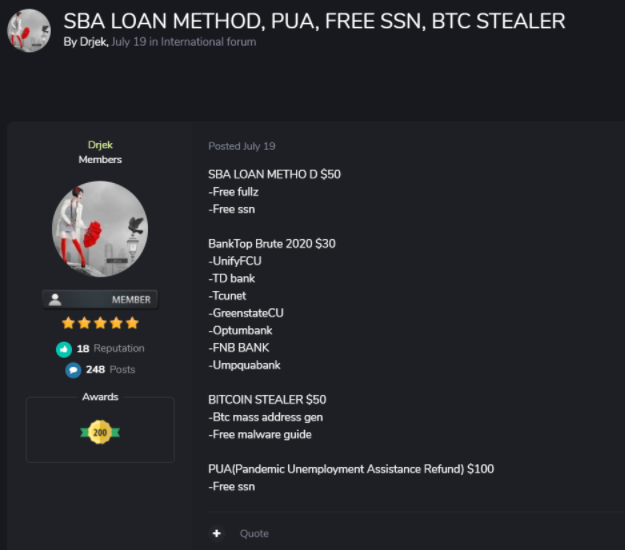
Scammers are offering fake products that, they claim, treat or prevent COVID-19. Warnings have been published against fake coronavirus test kits and hand sanitizers.
In some cases, bogus emails and texts claim to be from TV licensing authorities, and promise six months for free – as a gesture of good will. In other cases, victims are told about a problem with their direct debit accounts and asked to click on a link, which takes them to a fake website that steals their personal and financial information.
In the U.S., scammers have taken interest in stimulus checks and unemployment relief as a target for their fraudulent activities. As described in an investigation by the CyberProof CTI team, fraudsters steal citizens’ identity and divert the financial aid into their own pockets. According to the Federal Trade Commission (FTC), over 130 million dollars have been reported as fraud loss by almost 200,000 victims. (See this post by Social Catfish.)
Trend 3: The Proliferation of Ransomware
Ransomware is having its best year yet.
The following graph illustrates this point by showing the percentage of organizations that reported ransomware attacks this year (per country):
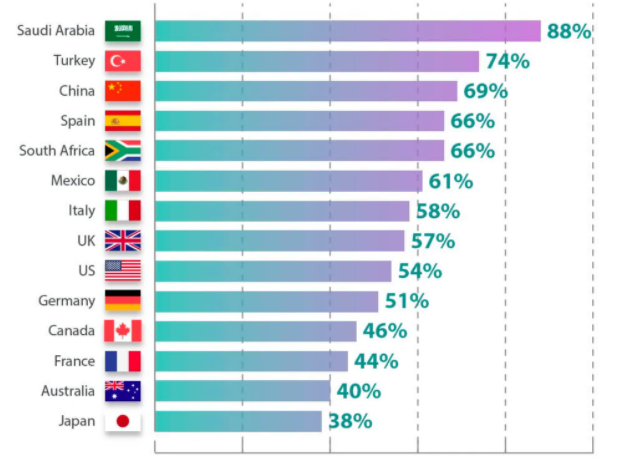
Threat actors are tweaking their techniques to ensure attacks are as destructive as possible, victims are paying what the attackers demand, and ransoms are higher than ever.
The following graph shows the increase in average ransom payment (by quarter):
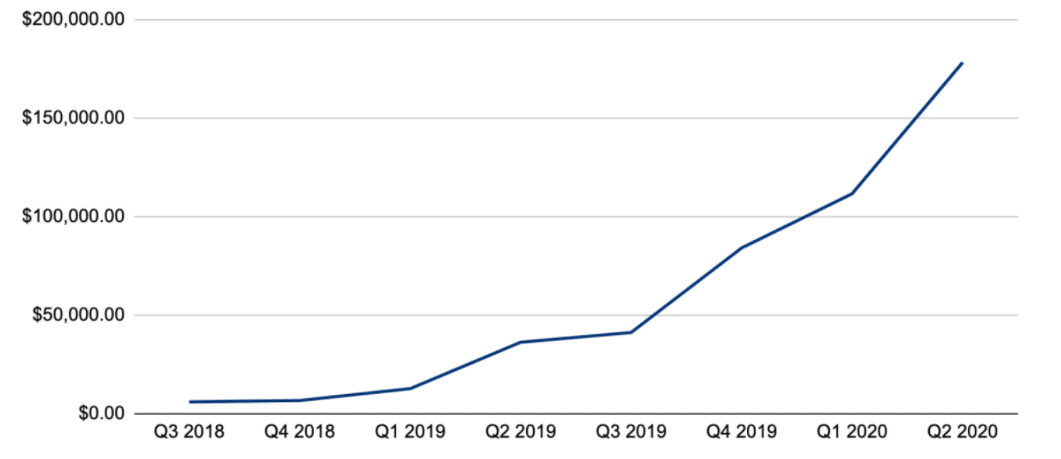
According to CoveWare, the average ransomware payment for the second quarter of 2020 was $178,254, a 60% increase from the first quarter.
There has also been a significant shift in strategy: The mainstream moved away from “spray-and-pray” to “big game hunting,” meaning instead of attacking individuals and small businesses, they focused on attacking critical infrastructure, governments, and major corporations.
Data exfiltration has become a big part of ransomware attacks. The CyberProof CTI team has been monitoring this approach, first made popular by the Maze ransomware gang in November 2019. Other groups quickly adopted it including Netwakler, Sodinokibi (REvil), Nefilim and DarkSide. In the second quarter of 2020, 30% of ransomware cases included a threat to release exfiltrated data and 22% of cases actually had exfiltrated data – an increase of 8.7% from the first quarter. Threat actors steal this data to use as leverage in negotiating the ransom.
This year, even historically modest Ransomware-as-a-Service (RaaS) operations are seeking higher ransoms. For instance, according to Sophos News, the second quarter marked the first series of six-figure ransom payments to the Dharma group, an affiliate ransomware platform that for years has kept pricing in the mid-to-low five figures and lower.
Ransomware is now available to lower-skilled cyber criminals – thanks to the popularization of RaaS. This is a ransomware infrastructure rented from hackers on deep and dark web forums. Ransomware operators provide the actual malware and technical support, while affiliates are in charge of delivery, deployment, and negotiating ransom terms with the victims. Affiliates are expected to pay operators between 30% and 40% of the loot.
Trend 4: Healthcare Under Attack
Universal Health Services, a major hospital chain, was hit on September 28th by what appears to be one of the largest medical cyber attacks that the United States has experienced.
This may be the largest but it’s certainly not the first – with this year seeing a notable increase in cyber attacks on institutions that are currently offering COVID-19 relief, including the World Health Organization (WHO), hospitals, research centers, and medical facilities. Cyber criminals are taking advantage of the global dependency on these organizations.
As a result, in April, INTERPOL released an alert advising healthcare organizations at the forefront of the COVID-19 response to be aware of an increase in the number of attempted ransomware attacks against them.
The following graph illustrates the increase in ransomware attacks against hospitals:
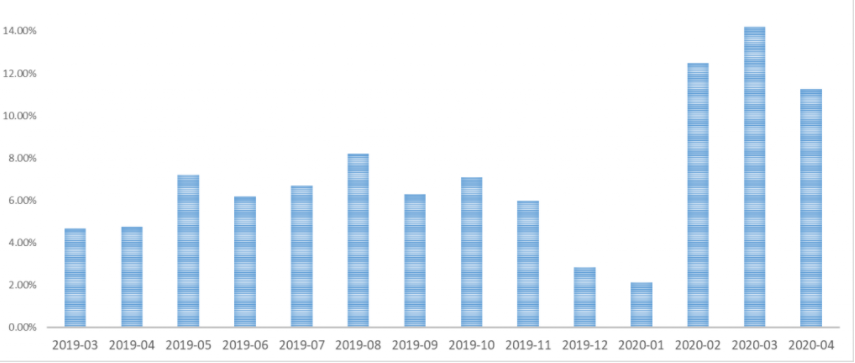
Healthcare was targeted even prior to the COVID-19 outbreak.
Organizations in healthcare store proprietary information that can be abused for committing fraud and identity theft. Healthcare workers also transfer data to third-party institutions, providing opportunities to find vulnerable links.
More than 93% of healthcare organizations have had a data breach since 2016, and 57% have reported five or more during this time frame. (See this post by Black Book Market Research.)
Because people’s lives depend on healthcare and it’s viewed as critical infrastructure, organizations in this sector are more likely to follow attackers’ instructions and pay the ransom.
This year, organizations involved in developing a vaccine for COVID-19 have been particularly at risk. Groups attacked pharmaceutical and research organizations developing a vaccine, and nation-state actors have been involved. For example, APT 29, a threat group sponsored by the Russian government targeted organizations in the U.K., the U.S., and Canada in attempts to steal COVID-19 research – with the aim of accelerating Russia’s efforts to develop a vaccine first.
Telehealth – remote medical treatment – has grown rapidly, as staying at home became normative. According to the U.S. Department of Health and Human Services, in April, almost half of primary care visits in this time period were via Telehealth. The quick move to telehealth expanded the attack surface, so the risk of breaches – for both healthcare employees and patient data – has grown.
Bottom Line: Take Precautions to Keep Your Organization Safe from Cyber Security Threats
While threat actors are exploiting the fears surrounding the pandemic to meet their own aims, organizations can work with their staff to reduce the risk of attack. Some examples of steps that you can take include conducting periodic employee awareness campaigns for suspicious emails and attachments, and educating users on how to spot and avoid phishing and malspam.
Be diligent; observe the fundamentals of cyber security hygiene. For instance, check that all applications and operating systems are running at currently released patch levels. Develop an authorization system that restricts access to the least possible number of users, and implement 2-factor authentication.
Stay informed about the latest threats and attack trends. By following “best practices” for cyber security, you can reduce the level of risk to your organization.
Learn more about how to combat the increasing cyber threats using automation in our webinar. To learn more, contact us.