CyberProof’s intelligence team uncovered a new threat actor – a user named eurobet.it.DDos, who was previously unknown. The team made this discovery after encountering multiple attempted DDoS attacks against several organizations.
An investigation of the attacker’s IP addresses revealed that the attack was related to Eurobet Italia – an Italian gambling site compromised two weeks ago. More recent reports added that Eurobet Italia’s public networks have been used for carrying out other cyber attacks, as well.
Ransom: $80,000 on Twitter and $200,000 on Instagram
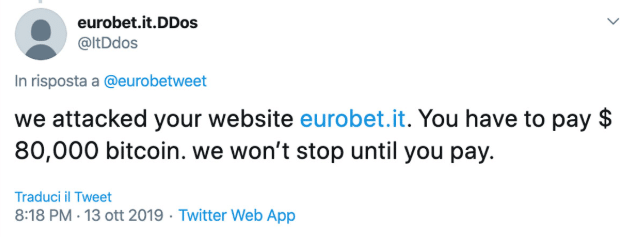
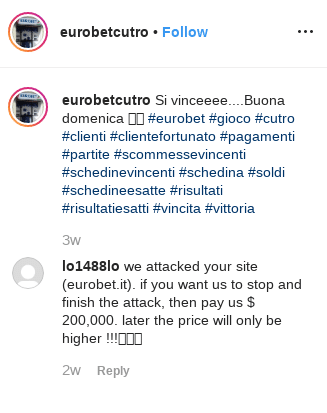
As part of our efforts to learn more about this cyber security threat, a Twitter account was identified that was created specifically for the attack on Eurobet Italia. The user, eurobet.it.DDos (@ItDdos), reacted to Eurobet’s official announcement about the attack, and demanded $80,000 to stop the attack.
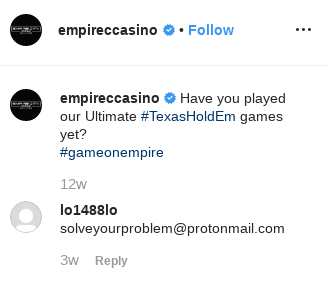
Later tweets included the attacker’s email address as a contact – Eurobet.it.ddos@protonmail.com. This email address led our team to identify an identical comment on a Eurobet Instagram page published by a user named lo1488lo, which demanded $200,000 USD.
There has been no activity (so far) on the attacker’s personal page. However, the user did add a comment on Instagram: “solveyourproblem@protonmail.com.” But we didn’t see any further mentions online or from our intelligence sources.
Misused IPs of Italian Cloud Computing Services Company SeeWeb
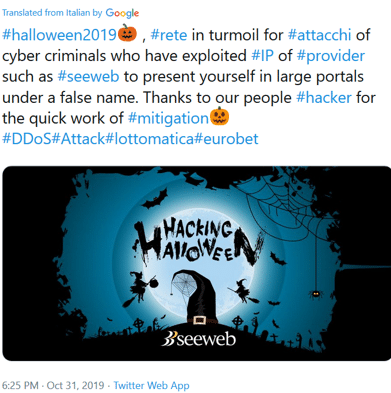
A few hours after the first attempted DDoS attack was detected, an Italian cloud computing services company named SeeWeb tweeted that cybercriminals misused their IPs for impersonation and conducted DDoS attacks. In the tweet, they included the hashtag of Eurobet.
Misused IPs of Italian gambling site Lotto Matica
A few days later, the same pattern of attack was detected – but being leveraged by IP addresses that do not belong to Eurobet Italia. An analysis of these IP addresses by our team uncovered that they are related to the Italian gambling site Lotto Matica, which was recently compromised (see this Italian source).
Currently, Lotto Matica IP addresses are being used to carry out cyber attacks on other companies using public IP addresses throughout Italy.
The attacker uses backscatter, which is specifically set up to do maximum harm on spoofed source IP addresses, in particular:
- 185.40.12.0/24
- 185.40.13.0/24
- 185.40.14.0/24
- 185.40.15.0/24
- 93.101.0.0/20
- 194.187.172.0/23
- 194.187.174.0/24
- 194.187.175.0/24
Bottom Line: Legitimate IP Addresses are Being Abused to Conduct DDoS Attacks
In conclusion, CyberProof’s research team believes that threat actors are abusing the legitimate IP addresses of several companies to conduct DDoS attacks targeting different organizations. The main purpose of the attacks is to harm the companies’ IP addresses’ reputation and put more pressure on them to pay money in order to stop the attacks.
Security Service providers like CyberProof have several unique advantages when it comes to uncovering such attacks. We have a greater ability to pool knowledge, resources, and expertise for cyber security risk assessment and spread the findings across all our customers.
Interested in learning more? Speak to one of our cyber experts today.