Deepfake attacks are becoming more common, and cybercriminals are finding them to be a powerful way to manipulate employees into sharing sensitive information or performing unauthorized actions. Using deepfake technology, attackers can impersonate senior managers convincingly, tricking employees into believing they’re interacting with trusted leaders. This trend is concerning, as the technology is getting more accessible every day, and attackers are taking full advantage of popular messaging apps like WhatsApp and Telegram to reach employees directly, and are using highly realistic voice or video impersonations to make their schemes more believable.
As a CTI analyst working closely with CyberProof clients, we come across threats like these very often. Attackers continuously refine their tactics, making it critical to stay ahead of these evolving threats.
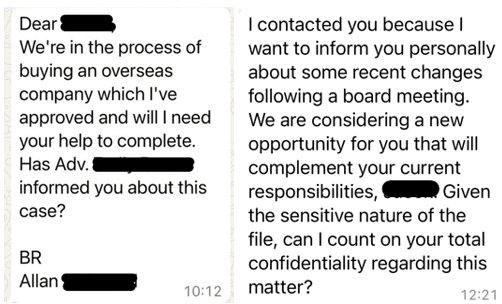
These attacks rely heavily on social engineering—essentially manipulating people’s trust to bypass security defenses. The pattern is often the same: an attacker reaches out to an employee on WhatsApp or Telegram, using a realistic deepfake of an executive like a CEO or CFO. Sometimes, the attack might start with an email and then move to messaging apps. To make their impersonations even more convincing, attackers often add profile pictures taken from LinkedIn and create Telegram channels with company names. They also use look-alike domains and fake email signatures that mimic real company details. Once the attacker builds enough trust, they request sensitive information, such as financial data or login credentials, relying on the employee’s natural trust in authority figures within the company.
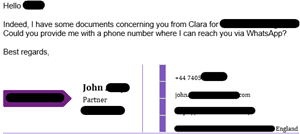
What’s enabling these attacks even more is the availability of eSIMs, which can be bought easily and anonymously. These allow attackers to quickly register new phone numbers, helping them appear credible as they impersonate executives. Telegram, in particular, is popular among these attackers because it allows users to sign in without a phone number and provides encrypted messaging, making it harder to trace the attacker’s identity. This combination of technology and anonymity has made Telegram a go-to platform for attackers using deepfakes.
The departments most targeted by these attacks are often HR and Finance, where employees have access to a wealth of sensitive data. Unfortunately, these departments may also lack the technical expertise to recognize social engineering tricks, making them especially vulnerable. It’s crucial for companies to prioritize security training for these employees, helping them learn how to spot unusual or suspicious requests, even if they seem to come from trusted managers.
It’s crucial for companies to prioritize security training for employees, helping them learn how to spot unusual or suspicious requests, even if they seem to come from trusted managers.
To minimize the risk, organizations should discourage using apps like WhatsApp and Telegram for work-related communications. Limiting conversations to secure, company-approved channels can significantly reduce exposure to deepfake attacks. Training employees to stay vigilant and to report suspicious interactions is equally important, as this helps create a culture of awareness that can greatly reduce the risk posed by deepfake technology and anonymous communication platforms.