“To a great mind, nothing is little” remarked Sherlock Holmes, describing the process of one of his investigations. Reading through Holmes’ quotes, one can easily identify a connection between detective work and the work of a Cyber Threat Intelligence (CTI) analyst. For example, consider the following quote: “A good detective knows that every task, every interaction, no matter how seemingly banal, has the potential to contain multitudes.” This is exactly what I believe in.
I want to share with you how this can be applied in a real scenario I was recently involved in, when I was investigating a ransomware attack. But first, let’s define what skills are required.
The Importance of Adopting a Problem-Solving Mindset
Though the field of Cyber Threat Intelligence (CTI) includes a wide range of technical skills and levels of expertise, the one thing that is common to all those who are engaged in intelligence work is a unique mindset and specific approach.
Intelligence work requires believing that the answers can be found between the smallest cracks – investigating them, being right at the point where others might not care enough to look.
Though the field of Cyber Threat Intelligence (CTI) includes a wide range of technical skills and levels of expertise, the one thing that is common to all those who are engaged in intelligence work is a unique mind set.
Intelligence work requires believing that the answers can be found between the smallest cracks – investigating them, being right at the point where others might not care enough to look.
Books on criminal investigation support this claim. A criminal investigation requires a set of emotional skills just as much as it requires technical skills. You need a strong problem-solving approach – the ability to ask questions and translate these into an effective investigation plan.
A criminal investigation requires a set of emotional skills just as much as it requires technical skills. You need a strong problem-solving approach – the ability to ask questions and translate these into an effective investigation plan.
The goal of a criminal investigator is similar to that of a threat intelligence analyst: namely, establishing an evidence-based pattern in order to prove something –usually, to prove the guilt of the accused party. The investigator (or the analyst) is a link in the chain, responsible for providing the missing piece of information.
The investigator (or the analyst) is a link in the chain, responsible for providing the missing piece of information.
What Skills Are Important to CTI Analysts
Looking at CTI analysts, the requirements for success are generally divided into four categories:
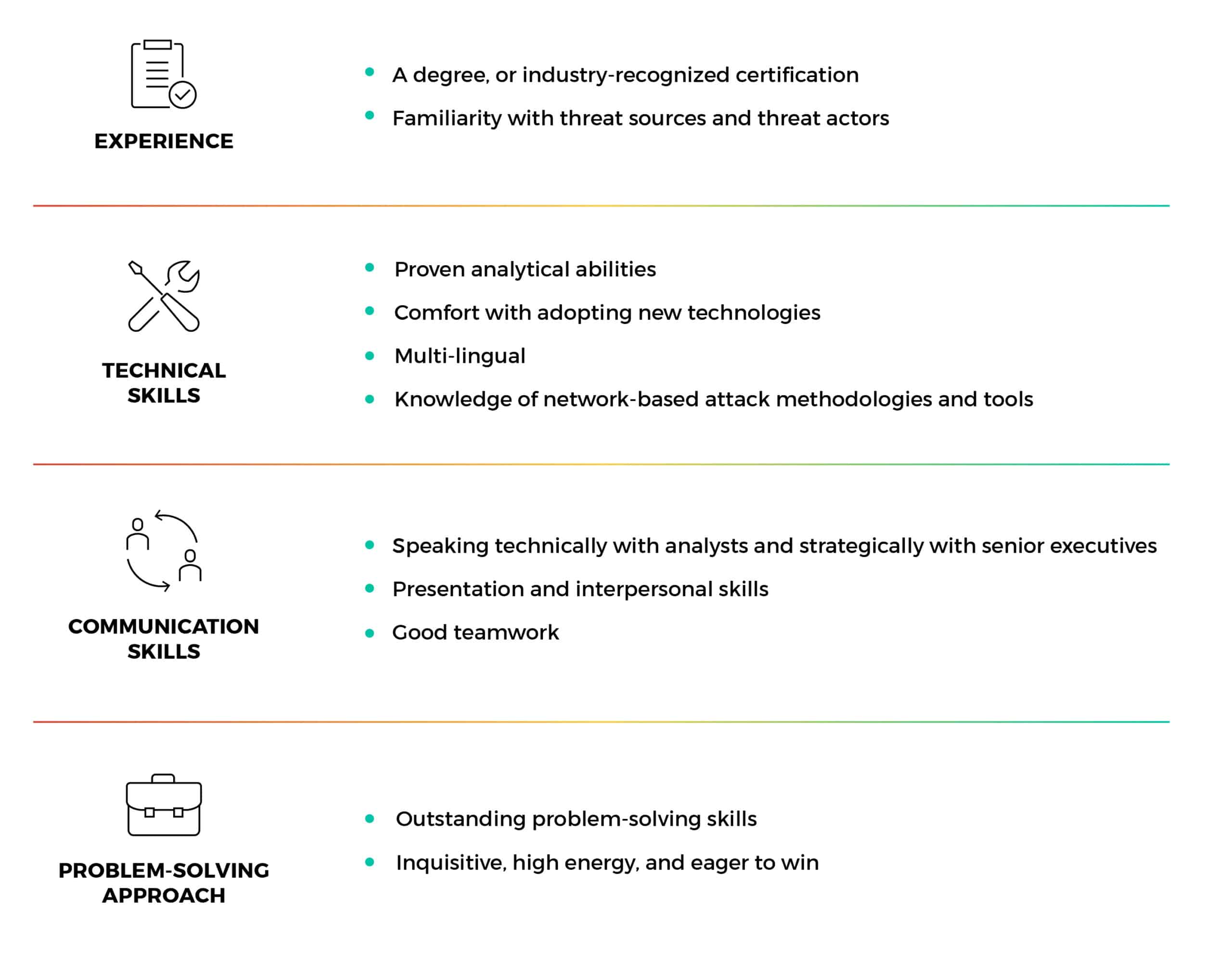
Like an investigator working on a crime scene, a CTI analyst works with “leads” – information that may help resolve your investigation. You develop a hypothesis – i.e., an estimation of what might have happened. The leads are collected, analyzed, and evaluated, and eventually they are shared with relevant teams with recommended steps for mitigation.
This requires experience, technical skills, and communication skills – but what orchestrates it is the analyst’s overall problem-solving approach. I like to call it the “treasure hunt” approach. Those who use this approach believe that the question is not “if” I can solve the puzzle, but rather “how” I can solve it.
Case Study: Tracking Down the Details of a Ransomware Attack
When an attack occurs, one of the most prevalent questions is: How did the attacker manage to get in?
Multiple departments are involved in answering this question, and search within the organization for “breadcrumbs” the attacker may have left behind on the network. But you also need to operate outside the normal corridors of the organization by wandering in the dark waters of underground communities.
So, where does the CTI team come in? Our story begins with a new client.
Step 1: Initial Engagement
A client approaches us after experiencing a ransomware attack. The incident is already under investigation, and the CTI team is asked to monitor the dark web for any potential data leakage.
Note that it is a relatively small task that we had been asked to do. But the fact that we had been asked to do just this one task, does not limit our work. It is always possible to do more! So, I decided to see how else we could possibly help this client.
Step 2: Arrive at the “Scene of the Crime” and Find a “Lead”
Once I had put into place the monitoring process that the client requested, I was ready to get started on the “real” intelligence work.
For me, when I am not asked to do something very specific for a client, I feel free to go ahead and conduct whatever intelligence work I like. In this case, I started playing around and trying to understand what else I could do for them.
Quietly, I looked at the information that was already uncovered in the investigation. The only known information was the ransomware group responsible for the attack.
I realized that this specific threat actor is known for using the Remote Desktop Protocol (RDP) – a protocol, or technical standard, for using a desktop computer remotely – as an initial access vector. RDP, I thought… That’s a good lead!
Step 3: Starting My Investigation – Using Technical Skills to Identify an Exposed RDP Server
I used Censys, an online banner scanner, to look for exposed servers with RDP services that were likely to belong to the client. Only one server was detected that matched the relevant keywords. The server was a Microsoft server, and the additional information I gained included the server’s geolocation.
Using Google maps, I could verify that the client had several data centers in the same geolocation.
Step 4: Leveraging the MITRE ATT&CK Framework to Identify the Attacker’s Technique
I knew that the attacker’s initial access vector was via RDP. I also knew that the MITRE ATT&CK framework suggests 3 techniques that are connected to RDP:
- Technique 1: Exploit public facing applications – Attackers could exploit software vulnerabilities in external services.
- Technique 2: External remote services – Attackers could use services such as RDP, Virtual Private Network (VPN), and CITRIX to gain access to the internal network. The access to external remote services could be obtained via brute force – in which case the CTI team does not have much to add; or, it could be obtained via valid accounts, which is more interesting and relevant to the CTI team’s work.
- Technique 3: Valid accounts – Attackers could use the valid account of an employee, or other authorized personnel within the organization. This kind of access should not raise any red flags. If this was the technique the threat actor used, then I know this will be helpful to the investigation.
According to reports describing the known Tactics, Techniques and Procedures (TTPs) of the attacker, the last two techniques described by MITRE seem to match the experience of CyberProof’s client:
Step 5: Continuing My Investigation by Thinking Like the Enemy
RDP credentials can be easily purchased on underground communities via access brokers or RDP marketplaces. The usage of access brokers and RDP marketplaces has become a major trend recently, notably among ransomware operators.
I used this information as the basis for my investigation plan. Assuming that RDP was the access vector, I searched for the full IP address of the server I had identified using a variety of different sources. But I did not learn any relevant information.
This is where another key concept in intelligence work comes in: “Think like the enemy. Talk like the enemy.”
At this point, I needed to leverage my understanding of how content might show up in different sources – i.e., how the actual forum users or marketplace owners would be likely to communicate.
This is where another key concept in intelligence work comes in: “Think like the enemy. Talk like the enemy.”
Step 6: Identifying RDP Access Offered for Sale
With my knowledge of how underground marketplaces usually present their content, I changed my mode of operation: Instead of searching the full four octets of the IP address, I searched only for the first two.
Here’s why: Most of the time, underground marketplaces do not reveal the full contents of what they are offering for sale. They expose a few details – enough to keep you engaged, but not enough to satisfy you. You are still dependent on them and will purchase the goods they offer.
The idea that the server I identified might belong to our client was a little far-fetched, because the IP address belongs to Microsoft, and I did not have visibility into the range of addresses that Microsoft assigned to our client. Nonetheless, I thought it was worth trying my luck to see what I could find out.
Adopting this approach worked: When I searched for the first two octets of the IP address, I found what I was looking for! There was only one result for the two octets, at a well-known RDP marketplace. This result also matched the geolocation that I had identified at the beginning of my investigation.
Essentially, finding the first two octets of the IP address on an RDP marketplace possibly could mean that someone had managed to access this server, offered it for sale – and thus allowed any user to purchase access to it. From that point on – the sky is the limit.
The RDP shop where I found the partial IP address was the UAS RDP marketplace, which recently made headlines. A threat intelligence agency called Advanced Intel managed to access the UAS RDP marketplace’s database – with the compromised credentials. It also was reported that many RDP servers in the marketplace’s database belong to organizations known to have suffered ransomware attacks over the past two years.
Step 7: Connecting the Dots
In this case study, the initial lead that I received was the name of the ransomware operation that attacked CyberProof’s client. By searching through Open-Source intelligence (OSINT) information, I was able to find multiple research reports describing the known techniques used by this attacker, as well as the MITRE ATT&CK mapping. By embracing this theory regarding the initial access to the network – and attempting to pivot from that point – I ended up identifying a potentially vulnerable server that could have been offered for sale on an underground marketplace.
Operating on the external perimeter, as I had done, meant that I had found a new lead or potential explanation, but I could not confirm all the details. I could not prove that the credentials to the server I had identified had been purchased. Nor could I ensure that the specific server compromised belonged to the client. But I could propose a theory and provide a new lead. I connected the dots and could now pass on the resulting hypothesis for further investigation.
And all this had happened without the client’s requesting it. Remember, the CTI team had been asked to do only one task – something that perhaps is the most obvious thing to ask the CTI team to do: monitor for data leakage. However, by taking a proactive approach, it became possible to reach beyond the task at hand and provide a potential answer to one of the most important questions in the investigation.
Interested in joining CyberProof’s team of experts? Apply today!














