Advanced persistent threats (APTs) are a category of threats that are continuously evolving and introducing new capabilities that reshape the threat landscape. These capabilities translate into a diverse range of tactics and techniques, both innovative and well known, that attackers use to infiltrate networks, breach defenses, and exfiltrate sensitive information that can be exploited by threat actors for their nefarious purposes.
Understanding these APT tactics and techniques is crucial to effectively preventing, detecting and responding to today’s cyber threats. The MITRE ATT&CK framework serves as an invaluable resource in this endeavor, offering deep insights into adversary behaviors.
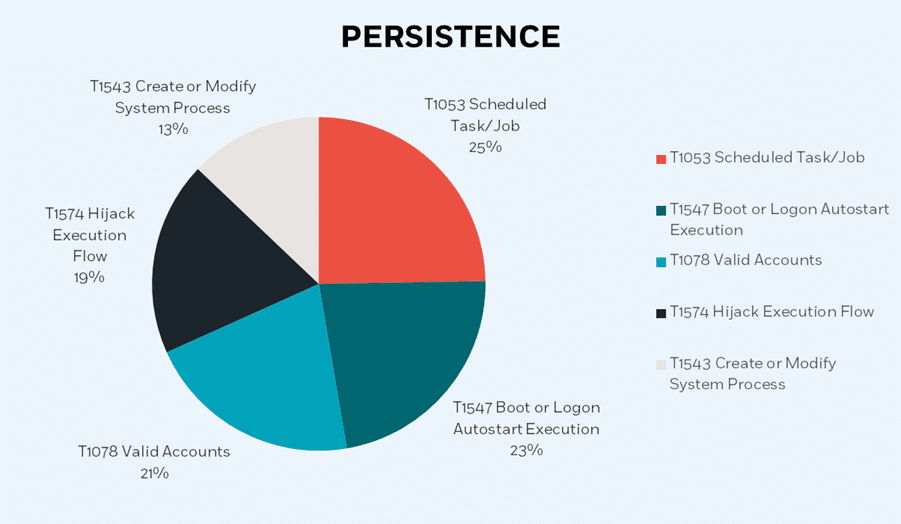
One particularly critical MITRE tactic leveraged by APTs is persistence, which serves as a linchpin for APT operations. Persistence allows adversaries to maintain an enduring presence within compromised systems, establishing a foothold that enables on-command control, data exfiltration, and stealthy maneuvering. Within the broader scope of the persistence tactic, two techniques – ‘Scheduled Task’ and ‘Boot or Logon AutoStart Execution’ – have gained significant traction among APTs due to their exceptional effectiveness and cunning nature.
One particularly critical MITRE tactic leveraged by APTs is persistence, which serves as a linchpin for APT operations. Persistence allows adversaries to maintain an enduring presence within compromised systems, establishing a foothold that enables on-command control, data exfiltration, and stealthy maneuvering.
In this blog post, we delve into two MITRE techniques used by APTs: ‘Scheduled Task’ and ‘Boot or Logon AutoStart Execution’. By presenting compelling statistics and real-world examples, we shed light on how APT actors exploit these techniques to maintain a lasting presence within compromised systems. Additionally, we provide actionable insights and measures that organizations can adopt to proactively detect and mitigate the risks posed by these techniques.
Technique 1: T1053 Scheduled Task/Job
Scheduled tasks are a built-in feature in operating systems that allow users to schedule programs or scripts to run automatically at specified times or events. They are commonly used for system maintenance, updates, backups, and other administrative tasks.
However, scheduled tasks have also become a popular target for APTs to execute malicious code or perform malicious actions. By creating these tasks, adversaries can establish persistence on a compromised system, maintaining access and control, even after the initial breach.
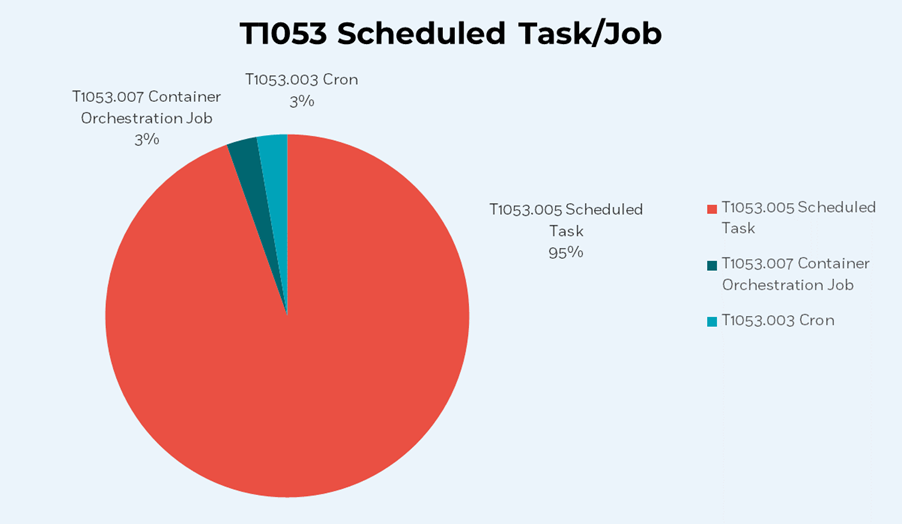
By taking a deeper dive into ‘T1053 Scheduled Task/Job’ sub-techniques, we identified that ‘T1053.005 Scheduled Task’ is the sub-technique most utilized by APTs in the past year, by a huge margin of 95% of observed cases.
T1053.005 Scheduled Task
Under the Scheduled Task/Job technique, there are several sub-techniques, which all have the capacity to schedule tasks. Yet, it has been observed that the ‘T1053.005 Scheduled Task’ sub-technique has gained significant prevalence in the APTs campaigns that we examined, whereas the other sub-techniques were either scarcely encountered or absent entirely.
These figures immediately raise the questions:
What factors contribute to the conspicuous predominance of the T1053.005 Scheduled Task sub-technique?
- Popularity and availability – As Windows is the most widely used operating system, ‘Windows Task Scheduler’ is more popular and well-known when compared to other utilities. Moreover, Scheduled Task is pre-installed on most Windows systems, making it easily accessible to attackers.
- System-level access – Windows Task Scheduler is executed with system-level privileges, providing attackers with full access to the system and the ability to perform a wide range of malicious activities. In contrast, in Unix/Linux systems, these utilities are typically used by advanced users or system administrators who have elevated privileges.
- Integration – Windows Task Scheduler is integrated with other Windows utilities, such as PowerShell and WMI, which provide additional functionality and ease of use. The other utilities may require additional software or tools to achieve the same level of integration.
- Flexibility and Features – Windows Task Scheduler provides a wide range of features, such as triggering tasks based on system events, user logins, or specific times. The other utilities have more limited functionality and are typically used for specific tasks, such as scheduling jobs or tasks in Unix or Linux environments. This versatility makes Windows Task Scheduler an attractive target for attackers.
How can an illegitimate use of the T1053.005 Scheduled Task sub-technique be identified?
To identify illegitimate use of the T1053.005 Scheduled Task sub-technique, look for the following scenarios:
- A scheduled task that is created on a targeted host to communicate with the attacker’s remote server:
DeviceProcessEvent
| where InitiatingProcessParentFileName has_any (“svchost.exe”)
- A scheduled task created by a command line that is executed to create a task, utilizing PowerShell to execute a base64 encoded payload that has been stored in the Windows Registry:
DeviceProcessEvents
| where FileName has “schtasks.exe”
| where ProcessCommandLine has_any (
“/SC”,
“/Create”
)
| where ProcessCommandLine has_all (
“powershell”,
“FromBase64String”,
“Get-ItemProperty”,
“HKCU:”
)
| project Timestamp, DeviceName, ActionType, AccountName, AccountDomain, FileName, FolderPath, ProcessId, ProcessCommandLine, InitiatingProcessFileName, InitiatingProcessCommandLine, InitiatingProcessFolderPath, InitiatingProcessId, InitiatingProcessParentFileName, InitiatingProcessParentId, InitiatingProcessAccountDomain, InitiatingProcessAccountName, ProcessVersionInfoCompanyName, ProcessVersionInfoProductName, ProcessVersionInfoProductVersion, ProcessVersionInfoInternalFileName, ProcessVersionInfoOriginalFileName, ProcessVersionInfoFileDescription, FileSize, SHA256, DeviceId, ReportId
| order by Timestamp
Technique 2: T1547 Boot or Logon Autostart Execution
Boot or Logon Autostart Execution is a technique used by APTs to launch malware automatically when a user logs in to a compromised system.
This technique involves creating a registry key or modifying an existing one, enabling the malware to start automatically during the boot or login process. This ensures that the malware runs every time the system is restarted or a user logs in.
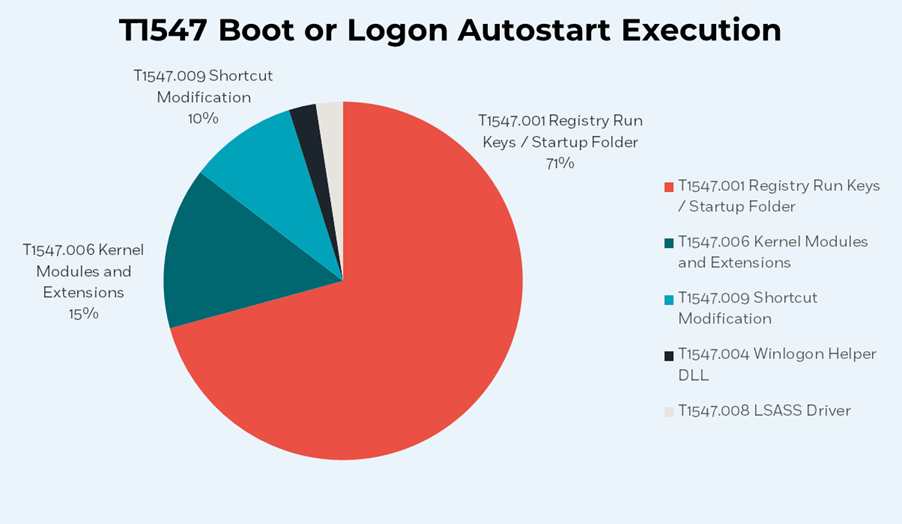
By taking a deeper dive into Boot or Logon Autostart Execution sub-techniques, we identified that ‘T1547.001 Registry Run Keys/Startup Folder’ is the sub-technique most utilized by APTs in the past year, by a clear majority.
T1547.001 Registry Run Keys/Startup Folder
This sub-technique refers to the process of executing malicious code or programs during system startup, specifically by adding entries to the Windows Registry or Startup folder.
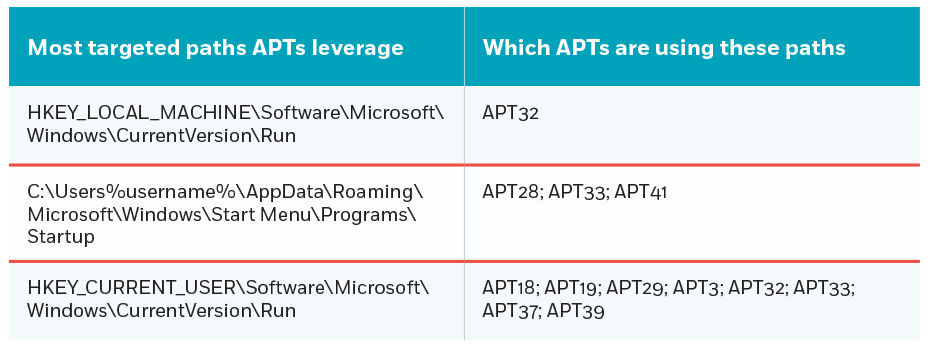
Most targeted paths APTs leverage to execute malicious payloads
The following table illustrated the most targeted paths APTs leverage to execute malicious payloads, and which APTs are using them.
The following map illustrates the APTs mentioned above, by their countries of origin:
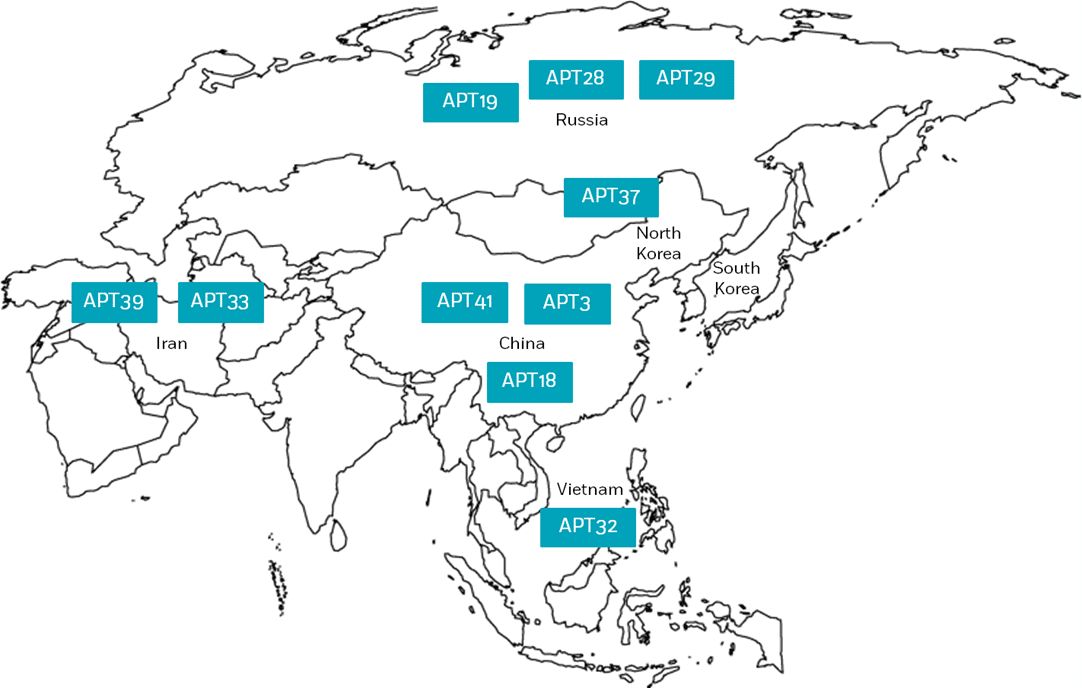
The APTs mentioned above, by their countries of origin
How to identify an illegitimate use of the T1547.001 Registry Run Keys/Startup Folder sub-technique
To identify an illegitimate use of the T1547.001 Registry Run Keys/Startup Folder technique, hunt for the following scenario:
- A registry key that is created on one of the above-mentioned locations in order to persist the attacker payload during system startupuser login:
DeviceRegistryEvents
| where Timestamp > ago(30d)
| where RegistryKey has_any (
“HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun”,
“C:Users%username%AppDataRoamingMicrosoftWindowsStartMenuProgramsStartup”,
“HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun”
)
| where not(InitiatingProcessFolderPath has_any (
“Microsoft Visual StudioInstaller”, “ClickToRunOfficeClickToRun.exe”, “softwareMicrosoftWindows NTCurrentVersionWinlogonShell”,
“MicrosoftOneDrive” Windowssystem32SearchIndexer.exe
))
| project Timestamp, DeviceName, InitiatingProcessAccountName, ActionType, RegistryKey, RegistryValueName, RegistryValueData, PreviousRegistryValueName, InitiatingProcessParentFileName, InitiatingProcessFileName, InitiatingProcessId, InitiatingProcessParentId | order by Timestamp
Understanding APT tactics and techniques can help mitigate the risk of attack
CyberProof’s latest report illustrates how effectively detecting and responding to APTs requires having an understanding of the tactics and techniques that they most commonly use.
CyberProof’s latest report illustrates how effectively detecting and responding to APTs requires having an understanding of the tactics and techniques that they most commonly use.
The report explores:
- How analyzing the TTPs used by attackers helps you identify potential vulnerabilities in your system and develop effective mitigation strategies
- How developing MITRE ATT&CK-based use cases that are tailored to your assets allows you to identify and respond to potential threats more proactively
Applying actionable insights and proactive measures can help your organization work to fortify its defenses against relentless APT campaigns.
To learn more about the MITRE tactics and techniques commonly used by APTs, download our report.