As our world grows ever more interconnected, vulnerabilities that appear in the software that runs much of our daily lives are at an all-time high. For enterprise organizations, that means that there are numerous potential entry points that can put sensitive data and critical assets at risk.
Managing these vulnerabilities strategically, in line with business needs and priorities, is a critical aspect of ensuring that your organization’s safety is regularly maintained. A framework that utilizes security strategy to enable business success is a main component of effective security transformation. When vulnerability management isn’t aligned with business requirements, however, its efficacy diminishes, creating a disconnect between cybersecurity measures and core business processes. When vulnerabilities are managed and threat potential decreases, your organization can focus on what it does best.
When vulnerabilities are managed and threat potential decreases, your organization can focus on its core business processes.
Our latest eBook, A guide to vulnerability management – mitigating the risk of AI-powered attacks, which was written in collaboration with Qualys, explores our recommendations for maintaining proper vulnerability hygiene. Here are some of the highlights that the eBook explores:
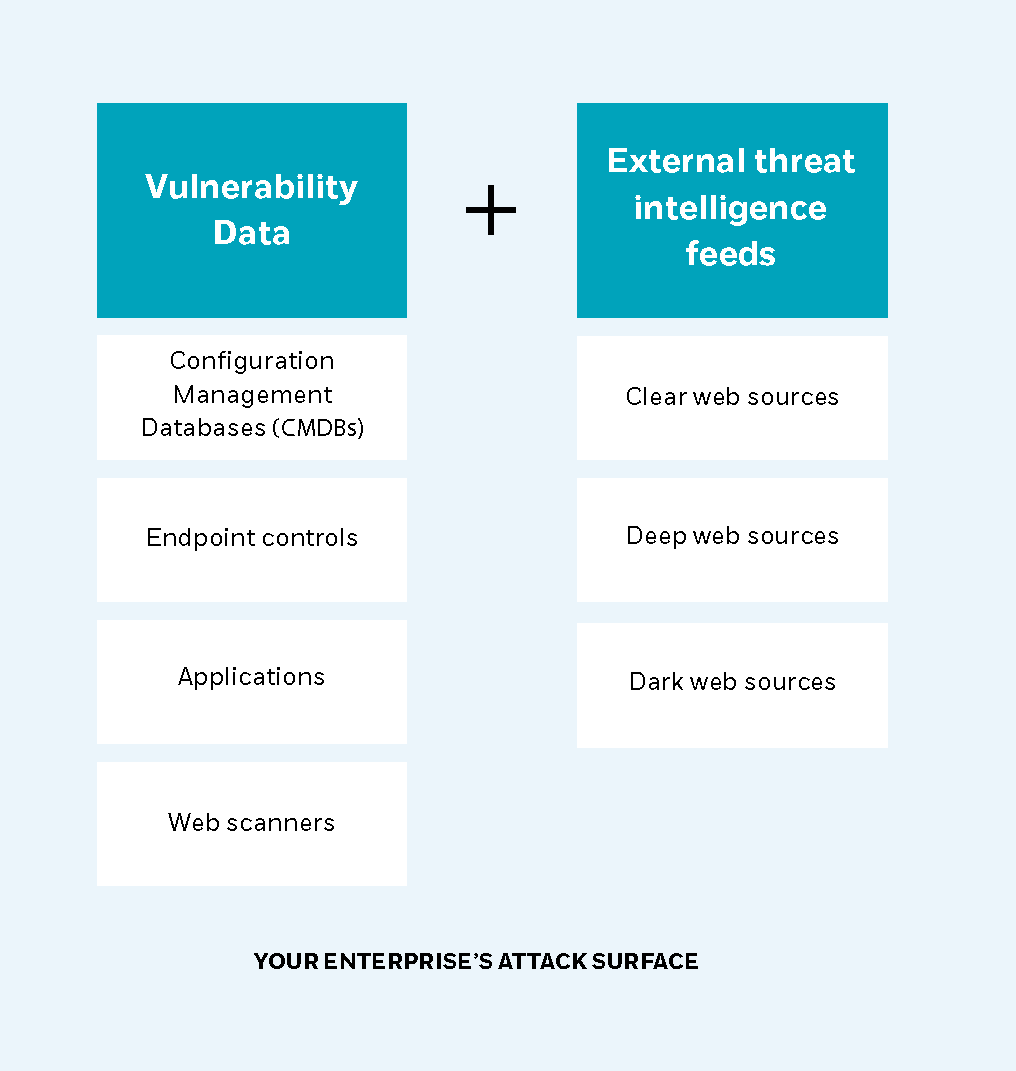
Integrate external cyber threat intelligence
External cyber threat intelligence provides an analysis of the attack surface surrounding your environment, enriching publicly accessible knowledge with relevant information for your attack surface – allowing you to prioritize what is critical to your organization.
Although many vulnerabilities are listed in public forums such as the Common Vulnerabilities & Exposure (CVE) database and the Common Vulnerabilities Scoring System (CVSS), they lack the enhanced data to identify which vulnerabilities pose the greatest risk to your business.
Maximize AI capabilities
AI tools play a powerful role in managing vulnerabilities, allowing defense mechanisms to match the pace of threat actors that utilize AI-powered attack techniques. These tools can aggregate intelligence, utilize use cases from past incidents, identify anomalies, and detail critical assets, among other capabilities.
AI and machine learning technologies are making threat intelligence capabilities more robust than ever before, maximizing impact on vulnerability management through continuous monitoring of cyber threat landscapes. By analyzing data from various sources and identifying patterns, these tools support prioritization of threat management according to business priorities.
Aim for real-time posture management
If your organization operates within a cloud-based infrastructure, scanning for vulnerabilities should take place on a real-time, constant basis. In multi-cloud environments, that can ensure that your organization stays up-to-date across clouds – which is critical to maintaining asset security. This comprehensive approach enables enterprises to mitigate risks effectively, minimizing the potential impact of vulnerabilities on their security posture by shortening remediation times.
Monitor the external attack surface
Attack surface management (ASM) solutions work to continuously monitor the external-facing components of a network. By taking an attacker’s perspective on entry points to an environment, ASM can locate exposed assets and analyze for any exploitable vulnerabilities or emerging threats, bringing to light vulnerabilities that you may not know exist. To bolster these solutions, identifying critical assets and focusing scanners on them can help your organization successfully prioritize the greatest risks to the business.
Develop tailored remediation plans
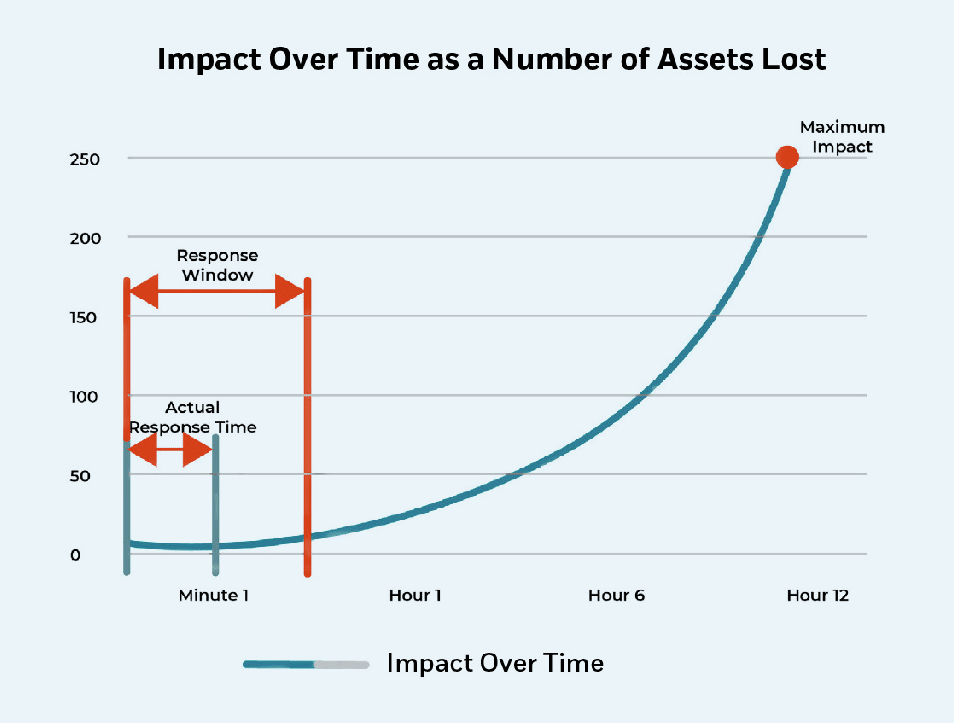
Swift remediation of vulnerabilities is not just crucial for security, but also has a direct impact on the financial health of your organization. The sooner a vulnerability is detected, the quicker it can be remediated, thereby reducing the impact curve of potential financial losses.
Remediation plans must be built in line with business goals, ensuring that critical operations are least disrupted while addressing vulnerabilities. In developing these plans, be sure to involve key stakeholders that understand strategic priorities to best allow vulnerability management to complement business goals.
Strong vulnerability management helps enterprises mitigate the risk of AI-powered attacks
As innovators and engineers craft software-driven solutions to address challenges across business, science, and finance, our world grows ever more interconnected. To best maintain the overall health and security of your organization, cybersecurity must be an enabler of success, rather than a barrier.
Vulnerability management can ensure that your organization proactively addresses threats, allowing business operations to continue on a normal basis. A Vulnerability Management service can integrate business goals with security mechanisms, paving the way for proactive risk mitigation that operates within the parameters of your organization’s needs.
To learn more about CyberProof’s Vulnerability Management Service, download our latest eBook.