Executive Summary
The ongoing conflicts in the Middle East have significantly shaped the cyber threat landscape, with prominent state-sponsored threat actors, hacktivist groups, and proxy cyber organizations leveraging the instability to advance their strategic goals. Prominent groups such as MuddyWater, APT33, CyberAv3ngers, APT34, and Fox Kitten, are actively involved in cyber operations targeting critical infrastructure, government agencies, and various industries.
CyberProof Threat Research Teams have observed and documented how these APT groups employ sophisticated techniques, including spear-phishing, custom malware, and AI tools, to exfiltrate sensitive data, disrupt operations, and gain unauthorized access to targeted systems.
APT MuddyWater
MuddyWater, a state-sponsored Advanced Persistent Threat (APT) group linked to Iran, continues to actively target Middle Eastern entities, leveraging the region’s geopolitical instability to advance its espionage and disruption goals. The group has notably focused on government agencies, critical infrastructure, and industries like telecommunications, energy, airlines, travel agencies, and media. Its operations often utilize sophisticated phishing campaigns, malware-laden documents, and custom backdoors designed to exfiltrate sensitive data and disrupt operations.
Recent campaigns have employed a custom malware known as “BugSleep,” which is distributed via spearphishing emails and hosted on the legitimate file-sharing platform Egnyte. BugSleep includes a custom loader capable of injecting malicious code into processes such as Microsoft Edge, Google Chrome, PowerShell, and AnyDesk. Additionally, MuddyWater has abused the Atera remote monitoring and management (RMM) tool to gain unauthorized access to targeted systems, enabling data theft, malware deployment, and operational disruption. Key targets in Israel, Turkey, Saudi Arabia, and Azerbaijan illustrate the group’s broad regional reach and strategic intent.
APT33
APT33, also known as Elfin, is a sophisticated cyber espionage group with roots in Iran, actively engaged in cyber operations since 2013. The group’s main targets include sectors that are vital to global infrastructure such as aerospace, defense, energy, and petrochemicals, with the intent to gather critical industrial intelligence. APT33’s activities are particularly troubling given their emphasis on infiltrating critical systems in regions like the Middle East, Europe, and North America. The group is also known for its collaboration with other Iranian cyber groups including APT34 (OilRig), APT35 (Charming Kitten), and MuddyWater, collectively showcasing a multi-faceted approach to cyber warfare that encompasses espionage, disruption, and the spread of disinformation.
In their cyber campaigns, APT33 has utilized destructive tools such as StoneDrill, drawing parallels to the infamous Shamoon malware, to execute high-impact attacks, with a notable focus on entities in Saudi Arabia and Europe. The group’s methodology typically involves spear-phishing and password spraying for initial intrusion, followed by credential theft to target high-value assets and the use of specialized tools aimed at industrial control systems (ICS). The explicit targeting of ICS by APT33 raises alarms over possible sabotage actions against essential services, including electricity generation and oil refining facilities. In their latest campaign, the threat actor deploys a new custom multi-stage backdoor named Tickler. Tickler has been used in attacks against targets in the satellite, communications equipment, oil and gas, as well as federal and state government sectors in the United States and the United Arab Emirates. The threat actors leveraged Microsoft Azure infrastructure for command-and-control (C2), using fraudulent, attacker-controlled Azure subscriptions that the company has since disrupted.
APT CyberAv3ngers
The CyberAv3ngers, a suspected Iranian Government-affiliated APT group linked to the Islamic Revolutionary Guard Corps (IRGC), have been active since at least 2020. They are known for targeting Israeli-made Unitronics Vision Series programmable logic controllers (PLCs), widely used in the Water and Wastewater Systems (WWS) Sector, as well as industries like energy, food and beverage manufacturing, and healthcare. Recent activities demonstrate a growing focus on industrial control systems (ICS) and Internet of Things (IoT) devices, with attacks aimed at disrupting operations and enabling unauthorized access to critical infrastructure.
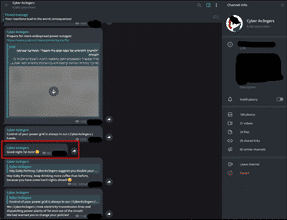
CyberAv3ngers announcement of cyberattack targeting Tel Aviv’s electricity transmission lines that knocked power plants offline.
Leveraging AI tools like ChatGPT, CyberAv3ngers conducted reconnaissance, coding, and vulnerability research to enhance their attack capabilities. These tools helped identify default passwords for industrial devices, analyze industrial routers in regions such as Jordan, and refine network exploitation scripts. The group is believed to be behind attacks targeting U.S. and Israeli IoT devices and SCADA systems through the deployment of IOCONTROL malware. This modular malware compromises devices, including IP cameras, routers, PLCs, HMIs, and firewalls, from manufacturers like D-Link, Hikvision, Phoenix Contact, and Unitronics, installing persistent backdoors for further exploitation. In response, the U.S. Department of State’s Rewards for Justice program has announced a reward of up to $10 million for information leading to the identification or disruption of these threat actors.

CyberAveng3rs threatens to reveal facts of lawlessness and corruption by Telegram.
APT34
APT34, also known as Earth Simnavaz and OilRig, is an Iranian state-sponsored advanced persistent threat (APT) group primarily focused on targeting organizations in the Middle East, particularly within the oil and gas industries. In their latest campaigns, APT34 leveraged a newly developed backdoor named Stealthhook to exfiltrate sensitive credentials, such as accounts and passwords, by exploiting on-premises Microsoft Exchange servers. The group uses this access to send stolen data as email attachments to attacker-controlled servers, enabling covert exfiltration. Notably, they have exploited the Windows CVE-2024-30088 vulnerability to escalate privileges on compromised systems, deploying malicious DLLs to further entrench their foothold.
APT34 continues to employ a range of sophisticated tools and techniques, including Remote Access Trojans (RATs) like NJRAT, spear-phishing campaigns, and zero-day vulnerabilities to compromise high-value targets. The group has also been observed using custom backdoors MINIBIKE and MINIBUS, which offer flexible code execution and advanced reconnaissance capabilities. Additionally, UNC1549, a sub-operation associated with APT34, triggers evasion mechanisms through multiple social engineering campaigns, ensuring the successful deployment of their malware. These operations highlight APT34’s ability to leverage both supply chain attacks and advanced cyber-espionage tools to maintain persistent access and gather intelligence across targeted networks.
APT Fox Kitten
Fox Kitten, an Iranian state-sponsored threat group, is actively assisting ransomware affiliates in targeting organizations across the U.S. and other countries. The group has collaborated with ransomware operators such as NoEscape, RansomHouse, and ALPHV (BlackCat), providing initial access to compromised networks in exchange for a share of the ransom payments.
Fox Kitten has been exploiting CVE-2024-24919, a now-patched zero-day vulnerability in Check Point VPNs, to gain unauthorized access to victim networks. Additionally, it has been observed targeting CVE-2024-3400 (a zero-day flaw in Palo Alto Networks’ PAN-OS), CVE-2019-19781 and CVE-2023-3519 (affecting Citrix Netscaler), and CVE-2022-1388 (impacting BIG-IP F5 devices). Active since at least 2017, Fox Kitten has targeted entities across the Middle East, North Africa, Europe, Australia, and North America, focusing on key industries such as oil and gas, technology, government, defense, healthcare, manufacturing, and engineering.
Conclusion
The use of AI tools in hacking is a critical evolution in cyber warfare, as threat actors exploit artificial intelligence to accelerate reconnaissance, vulnerability research, and cyberattack preparation. These AI-assisted campaigns enable adversaries to probe ICS and programmable logic controllers (PLCs) at unprecedented speed and scale, making traditional defensive measures increasingly ineffective. Security professionals in critical sectors like water, energy, and manufacturing must now contend with AI’s dual role – as both an offensive tool for attackers and a strategic advantage for defenders. As AI models advance, the sophistication of AI-driven attacks will only grow, further amplifying the risks to critical infrastructure. Proactive defensive strategies, such as securing devices with strong passwords, eliminating default credentials, patching known vulnerabilities, and implementing continuous ICS network monitoring, are essential to mitigating this emerging threat landscape.
Learn more about the 2024 threat landscape, predictions for 2025, and recommendations for strengthening your cybersecurity strategy in the CyberProof annual report 2025 Global Threat Intelligence: Mapping Threats and Trends.