Tony Velleca, CyberProof CEO, sees that security operations are moving to modern cloud-native architectures at an accelerated pace. In this interview, he addresses the growing number of cyberattacks and changing technology landscape – as well as the widespread digital transformation of enterprise IT environments.
What are the essential components of building a cloud-focused, future-proof SOC?
As I see it, a modern Security Operations Center (SOC) must include the following key components, on top of a cloud-native architecture:
1. Cloud-native SIEM – Traditional SIEMs are expensive to deploy, own and operate, incurring high costs for infrastructure maintenance and data ingestion. A cloud-native SIEM has no up-front costs. It helps collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
2. Endpoint Detection & Response – EDR combines real-time continuous monitoring & collection of endpoint data with rule-based, automated analysis and response. Integrating EDR with your SOC supports a Zero Trust approach – providing a centralized platform for monitoring endpoints and responding to incidents, often via automated response.
3. Data lake – The data lake is a centralized repository where structured, semi-structured, and unstructured data can be stored, processed, and secured. It has the advantage of being able to store unlimited quantities of data from multiple sources.
Where should organizations focus resources to optimize security when shifting to the cloud?
Legacy solutions used in a SOC, in my experience, can fall short in numerous places, including:
-
Endpoint security: Most current security solutions were designed for on-premises or local data centers, which poses a major challenge. As applications move to the cloud, endpoint security becomes more important.
-
Response time: More emphasis must be placed on incident response and in reducing Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). Artificial intelligence (with tools native to the cloud) is required to enhance the speed of detection and response.
-
OT/IT convergence: Endpoints are expanding to include Internet of Things (IoT) and Operational Technology (OT) connected devices. These are on a path to converge, from a holistic security perspective. Industrial control systems and processes (and other specialized applications) are becoming more standardized and, therefore, are easier to attack. This presents new vulnerabilities with higher associated risk levels.
-
Applications: Custom or open-source applications are a growing target for hackers and are increasingly hard to secure. This is especially true where public cloud providers manage infrastructure security.
How can security architecture be best optimized for the transition from on-premises infrastructure to the public cloud?
If your enterprise handles critical client data or payment details or is undergoing digital transformation, you should absolutely consider cloud-native security operations.
But modernization is not always simple for large, regulated enterprises. Organizations moving infrastructure from data centers to the public cloud need to rethink their security portfolio – starting with the security solutions and methods for detection, response, and recovery.
Organizations moving infrastructure from data centers to the public cloud need to rethink their security portfolio – starting with the security solutions and methods for detection, response, and recovery.
In many cases, organizations must show parity between their old and new infrastructures.
When you shift fundamental IT architecture from the data center – servers, hardware, firewalls, etc. – into the public cloud, it’s the right time to redesign your security architecture to a cloud-native architecture.
How can implementing Zero-Trust models ensure that organizations are able to secure endpoints across the public cloud?
Much of what we have been buying in recent years, in terms of product, is natively available in the cloud – including all Artificial Intelligence tools or algorithms. The algorithms themselves are not new – but until now, we haven’t had the quantity and quality of data necessary to train them effectively. Microsoft, for example, deploys advanced algorithmic capabilities within Defender and other suites.
Note that the endpoint is becoming more complicated – it’s not just a computer and a mobile but also OT and IoT devices: smart meters, elevators, and even self-driving cars. These endpoints generally connect to applications that run in a public cloud. At the endpoint, we are moving to Zero Trust models that require reliable identity verification and controlled or limited access.
The industry has coined a new term: eXtended Detection and Response (XDR), a security platform that can aggregate security information from multiple sources including the endpoint, cloud, and identify management systems – to help teams isolate and respond to threats faster.
A Managed Detection & Response service leveraging the Microsoft XDR platform, for example, helps companies identify attacks – from email and endpoints to identities and applications – enabling a timely response to reduce the impact of the attack.
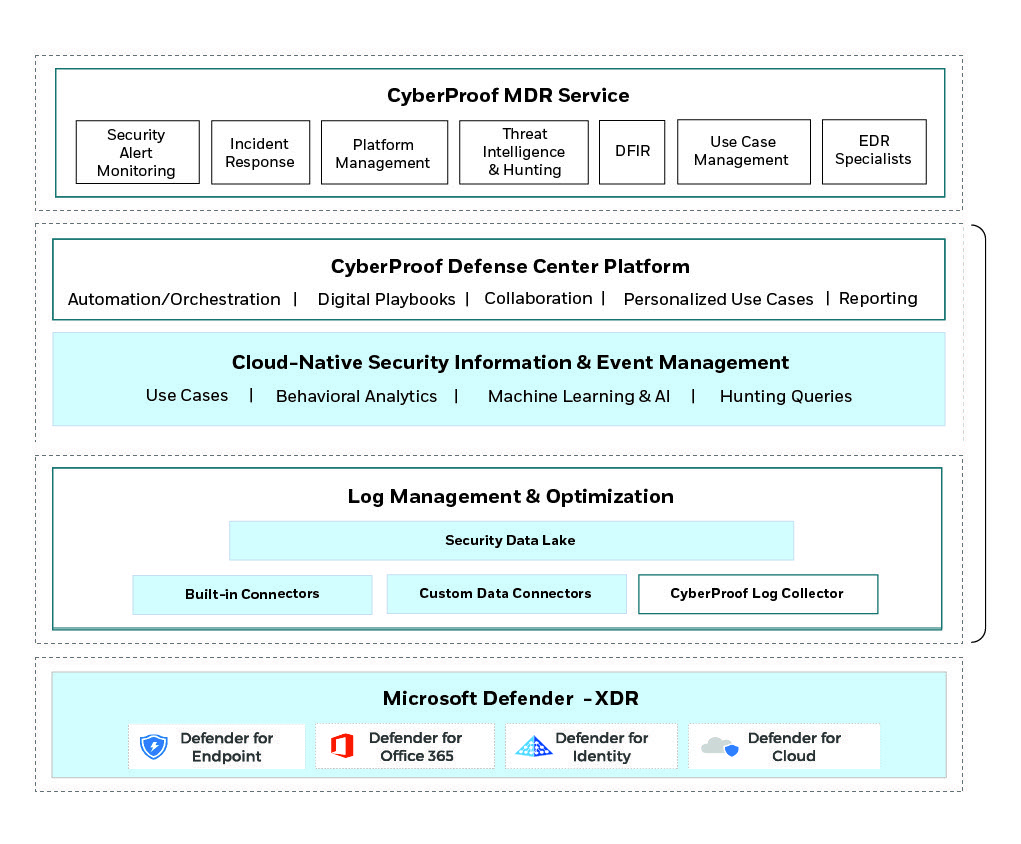
How can a Managed Detection & Response (MDR) provider utilize cloud-native infrastructures to offer an organization advanced SOC services?
With cloud-native components in place, there are many services that an MDR provider can provide. The three I’d like to highlight are:
1. Orchestration & Automation – This enables a bird’s-eye view across the enterprise, alleviating the stresses of increasingly sophisticated attacks, increasing volumes of alerts, and long-resolution time frames. Orchestration & automation involves leveraging solutions that allow organizations to streamline threat and vulnerability management, incident response, and security operations automation.
2. Tailored Threat Intelligence – Threat intelligence is evidence-based knowledge about existing or emerging threats that can be used to inform decisions. There are 3 types: Strategic looks at changes in the broader threat landscape and is primarily aimed at executives. Operational seeks to understand how an organization could be attacked by outlining Tactics, Techniques & Procedures (TTPs). Tactical covers the details of an attack with the shortest lifespan – such as Indicators of Compromise (IOCs) that are fed into the SIEM or firewalls.
3. Advanced Threat Hunting – Threat hunters evaluate the network and develop security baselines, proactively pinpointing policy violations within the network. Threat hunting strengthens the cybersecurity ecosystem by incorporating a more proactive approach while improving the security posture by reducing the attack surface.
What can automated SOC operations do to help an organization “see the big picture” and respond faster to threats?
The deployment of cloud-native XDR supports the automation of many tier 1 and tier 2 processes that are typically labor-intensive. Some examples of types of work that analysts do repetitively include:
-
Patching and testing enterprise systems
-
Deploying improvements to the infrastructure
-
Addressing support tickets from employees
-
Generating reports for senior management about the organization’s security posture
These tasks prevent SOC teams from maintaining the “Big Picture” vision so necessary to protect the enterprise. By minimizing tier 1 and 2 activities in an analyst’s workload, it becomes possible to invest more time analyzing potential threats. Automation thus leads to greater insight – allowing teams to react more quickly.
A modern cloud-native SIEM leverages algorithms to connect and master data streams, and to ingest and verify alerts by acting as a single security analytics platform that covers multiple cloud environments. Cloud-native XDR supports SOC teams by running playbooks, hunting queries, and deploying infrastructure as code.
A modern cloud-native SIEM leverages algorithms to connect and master data streams, and to ingest and verify alerts by acting as a single security analytics platform that covers multiple cloud environments.
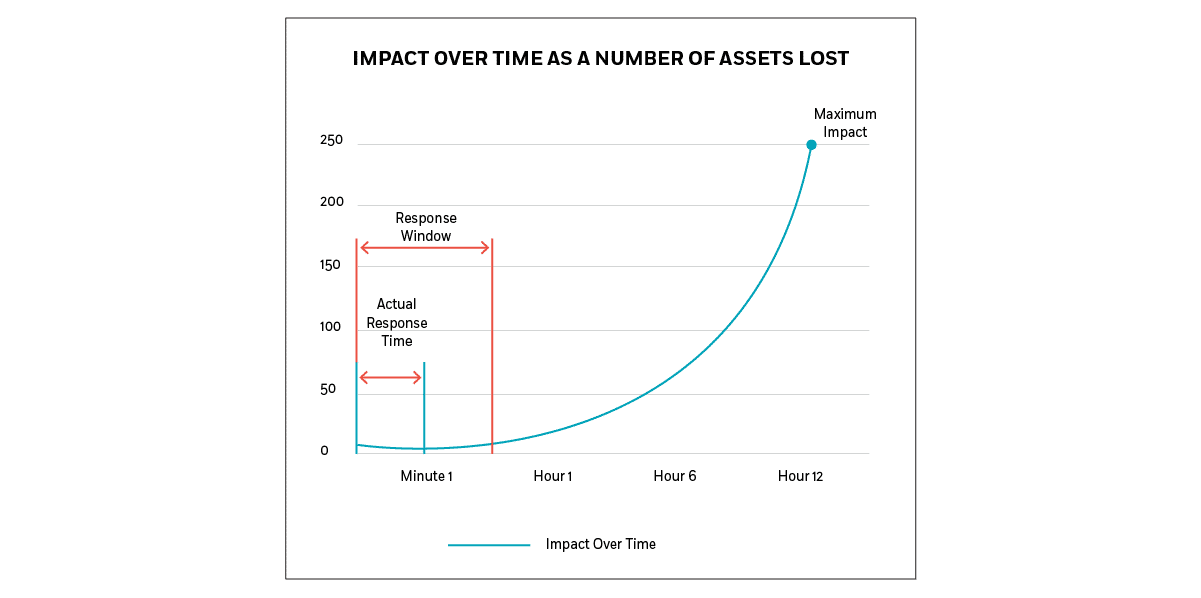
Impact over Time as a Number of Assets Lost
For every attack scenario, there’s an impact curve that defines the amount of loss over time. By defining the “response window” – the minimum period, after which an attack’s impact becomes exponentially greater – you lessen the risk associated with the attack. Because the magnitude of loss is associated with the time required for detection and response, speed and agility are crucial.
Working with an advanced MDR provider can give you access to experts with the skills that can power your organization’s cloud migration, managing exposure to unnecessary risk while supporting business needs and goals. An advanced MDR provider like CyberProof can provide the kind of security monitoring and transformation support that can decrease your organization’s level of cyber risk while undergoing cloud migration.
If you’d like further insight into building your own modern, cloud-native SOC, contact us!