The reality created by the COVID-19 pandemic has provided troubling opportunities for cyber criminals, who have been capitalizing on and abusing the global confusion. During the last six months, cyber threat intelligence (CTI) researchers have registered an uptick in many types of cyber attacks – including phishing campaigns, data-stealing malware, ransomware, and the abuse of remote-worker infrastructures.
Now, another cyber security threat has surfaced, one that targets the new funding that the U.S. government provides to individuals who are struggling financially due to the pandemic recession.
Scammers Target SBA and Unemployment Relief Funds in the U.S.
The unemployment rate in the U.S. has been rising as a result of COVID-19, and the pressure on the federal administration to provide economic relief has continued to increase.
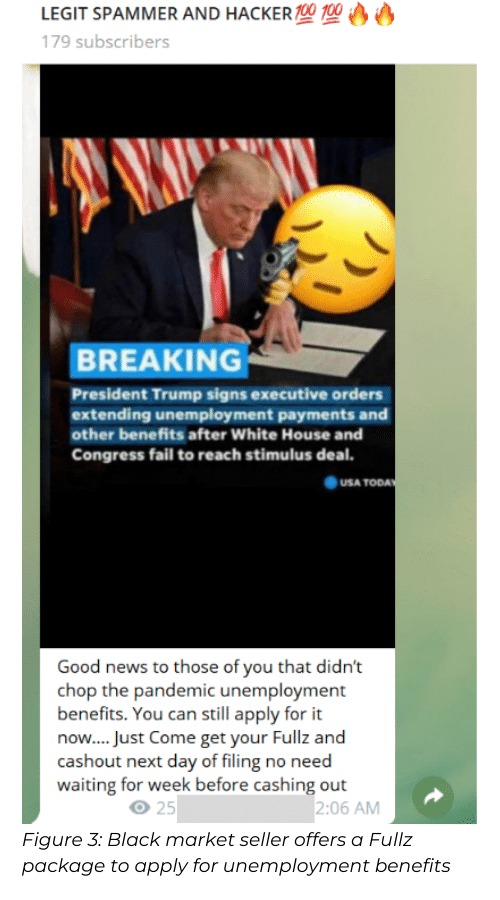
As a result, President Trump signed a series of executive orders aimed at boosting the U.S. economy, including a Presidential Memorandum regarding assistance to the unemployed.
As part of the new benefits package, U.S. citizens whose employment was interrupted due to the pandemic will receive between $400 to $600 per week. News of the unemployment package quickly made its way throughout the cyber crime underground.
In several communities frequented by carders, spammers, and fraudsters, discussion about the unemployment relief started almost instantly – along with discussion of other relief packages such as the SBA (Small Business Administration) loan and EIDL (Economic Injury Disaster Loan).
Enticed by the possibility of “free” money, members of groups on hacking forums and platforms such as Telegram and Discord, started to share different methods to siphon off the money.
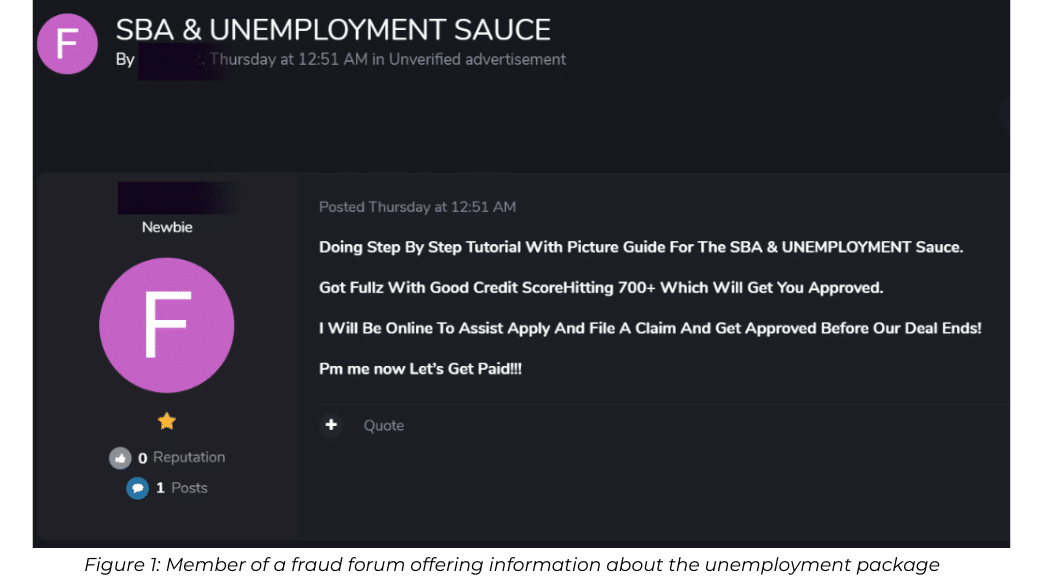
How It Works
The methods being shared online reflect a deep understanding of how the bureaucratic process works. Fraudsters know exactly what the requirements are for obtaining unemployment relief funds and which personal details are requested – name, date of birth, address, social security number, and a U.S. phone number (should authentication codes be provided by phone).
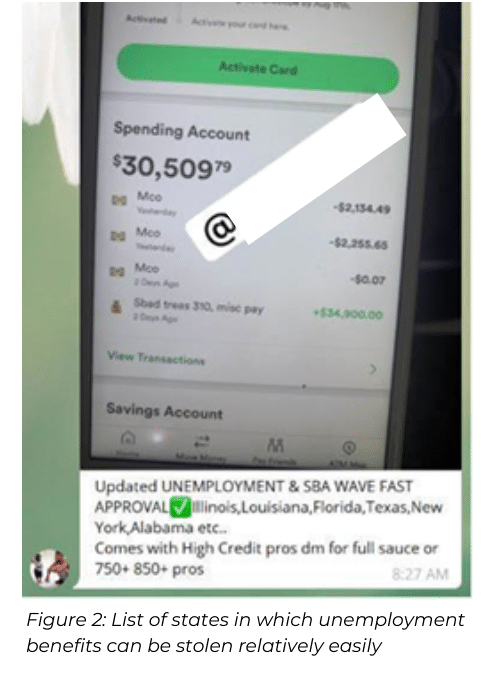
Fraudsters also studied direct deposit information, e.g., the fact that prepaid cards with direct deposit capabilities such as Cash App, Bluebird and Netspend are accepted.
Moreover, cyber criminals figured out: which states are currently paying the unemployment assistance, which states stopped paying, and which states are strict in their processes and track applicants down if there are any anomalies in the information provided.
Information is being shared regarding the best way to fill out the unemployment forms – and tips are available describing how to receive as much financial aid as possible.
For example, when filling out information about annual earnings, sources indicate that one can obtain optimal results by writing an amount that is between $16,850 and $42,100. When choosing an occupation, one guide in a closed Telegram group recommended choosing “self-employed wedding photographer” – since almost all weddings and large gatherings have been cancelled, so no income could have been earned since the pandemic began.
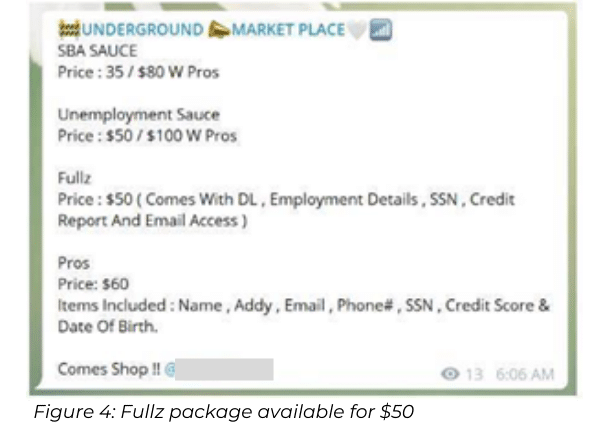
Personal Data Packages Can Be Purchased for $50
Because fraudsters need specific personal data in order to cash in and obtain the unemployment relief, a wave of black-market sellers have started offering these digital goods. For instance, the market for Fullz – packages of personal information used by cyber criminals to steal identities – has notably increased.
On average, one can purchase a full personal data package for $50. The package usually provides all of a U.S. citizen’s personal data – including the details one needs to fill out the paperwork and obtain unemployment payments.
New Tactics Used with the Current Stimulus Payments
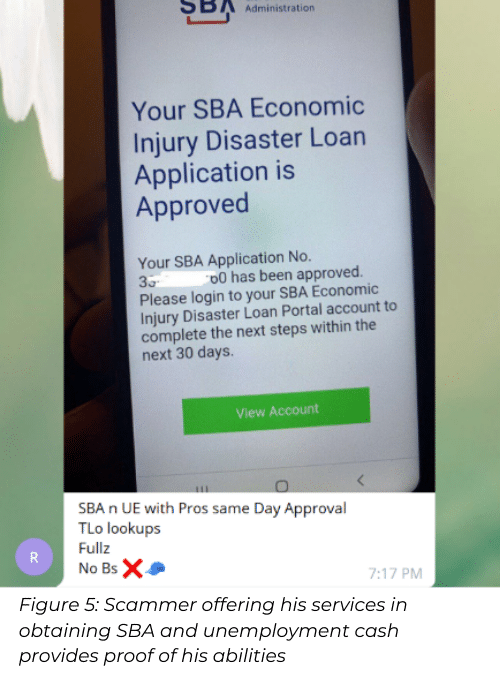
Previous scams involving SBA loans and unemployment benefits focused on phishing for credentials and malware distribution, both using themed fake domains. (For more about this topic, see this post by Check Point.)
In contrast, the current scams being discussed and sold on the hacking communities consist of fooling government organizations and stealing taxpayers’ money from people who are in real need of it.
If a cyber criminal successfully cashes an unemployment check, the unemployed person, whose identity was stolen, is left without the aid that the government intended to provide the individual.
Recommendations for Protecting Individuals Against Identity Theft
For people who are entitled to receive stimulus payments, there are definitely ways to limit the risk. Here are our recommendations to be aware of:
- Anyone entitled to a relief payment should be sensitized to the fact that scammers are trying to steal personal information via phishing emails, social media, phone calls, and texts.
- When submitting information to claim stimulus payments, applicants should only use official government websites (usually ending in .gov).
- Emails claiming to be from the Center for Disease Control (CDC) or World Health Organization (WHO) should be ignored, as they are usually fake emails that are used for phishing activities.
- Any U.S. citizen who believes that their stimulus payment was diverted to a scammer can report this theft to the Federal Trade Commission (FTC) and the Internal Revenue Service (IRS). See the U.S. Government’s official one-stop service for reporting different kinds of identity theft: https://identitytheft.gov
For additional insights on how to protect personal information, take a look at these data hygiene and security monitoring tips. And, as always, if you are concerned about the robustness of your organization and its ability to protect itself from cyber attack, contact us. We’re here to help.