What is proactive threat hunting?
Cybersecurity threat hunting is the proactive search for malicious activity that is hidden within an IT network. Working on the assumption that attackers have already gained access, and there are threat actors or their malware already within the network, a cyber threat hunter searches for evidence of their activities, as well as assisting in reducing the entire attack surface of the enterprise as a whole.
In this guide, we will discuss the different benefits of threat hunting, how threat hunting reduces risk, and practical guidance for adopting threat hunting methodologies, techniques, and best practices in any organization.
What is proactive threat hunting?
Proactive threat hunting or proactive hunting is another way to describe threat hunting. The idea is that an expert cyber hunt team will act ahead of time to search an enterprise IT environment for signs of infiltration, assuming that a hacker has already breached the perimeter or established access through a vulnerability or misconfiguration.
Threat hunting is as much a shift in mindset as it is a practical methodology. By working on pre-empting any threats and anticipating how hackers may be behaving before there are any signs of a threat, security hunting teams can find issues before they turn into crises and share hardening techniques that reduce risk.
Are all types of threat hunting proactive?
One of the main differences between threat hunting and other kinds of cybersecurity is the proactive nature of hunting.
In today’s complex enterprise IT environments, it’s common for businesses to rely on a security operations center (SOC). This team handles incoming alerts about security risks, and will often include an incident response team who can escalate and mitigate ongoing threats. On a continuous basis, the SOC team will offer key information and insight about threat detection and risk trends, and may perform vulnerability assessments and pen testing. However, this is not the same as threat hunting.
One way to understand threat hunters vs. the SOC, is that while the SOC team mainly acts reactively, threat hunting acts as an additional, proactive layer of support.
Distinguishing threat hunting from threat intelligence
This opens up the question, what is threat hunting in cybersecurity, compared to threat intelligence?
First, let’s understand what threat intelligence is, and who performs that task. Threat intelligence may include certain proactive actions, such as taking known Indicators of Compromise (IOCs) and searching for them. The Cyber Threat Intelligence (CTI) team searches the clear, deep and dark web and gathers information about potential attacks against an organization. They organize and analyze the data and leverage it to mitigate the risk of attack. This process could be considered a basic level of threat hunting, and often threat intelligence teams will provide this information to the threat hunting team to support them in tasks such as hunting malware.
While threat intelligence is cardinal in developing hypotheses and supporting threat hunters in finding signs of attack, the threat hunting process goes much deeper. Instead of searching the deep and dark web for information about potential attacks on an organization, threat hunters assume that known attacks have been successful in the network already. A well-planned threat hunting program will reflect a deep understanding of infrastructure, recognize the context of different kinds of attacks and adversaries, and include the ability to detect and monitor long-term trends with the help of several sources of data, including a wide variety of logs.
How can cyber threat hunting tools complement the CTI team?
Threat hunting tools are not the same as threat intelligence, but the work that the threat hunters do is a natural complement to the way the CTI team functions, and the two teams will often work in tandem.
Threat hunters will use the data found by the CTI team to create baselines, and provide the SOC with feedback, creating a symbiotic relationship between the two. The strongest threat hunting initiatives will result from working holistically with threat intelligence and SOC teams, where information is shared openly, and goals and communication are aligned.
Who should be involved in threat hunting?
As threat hunting works best when it’s performed holistically as part of the enterprise security strategy, the whole security team should be on board. While a dedicated threat hunting team may be responsible for performing the practical hunt, information and support can also come from SIEM experts, forensic intelligence teams, or even from customers themselves.
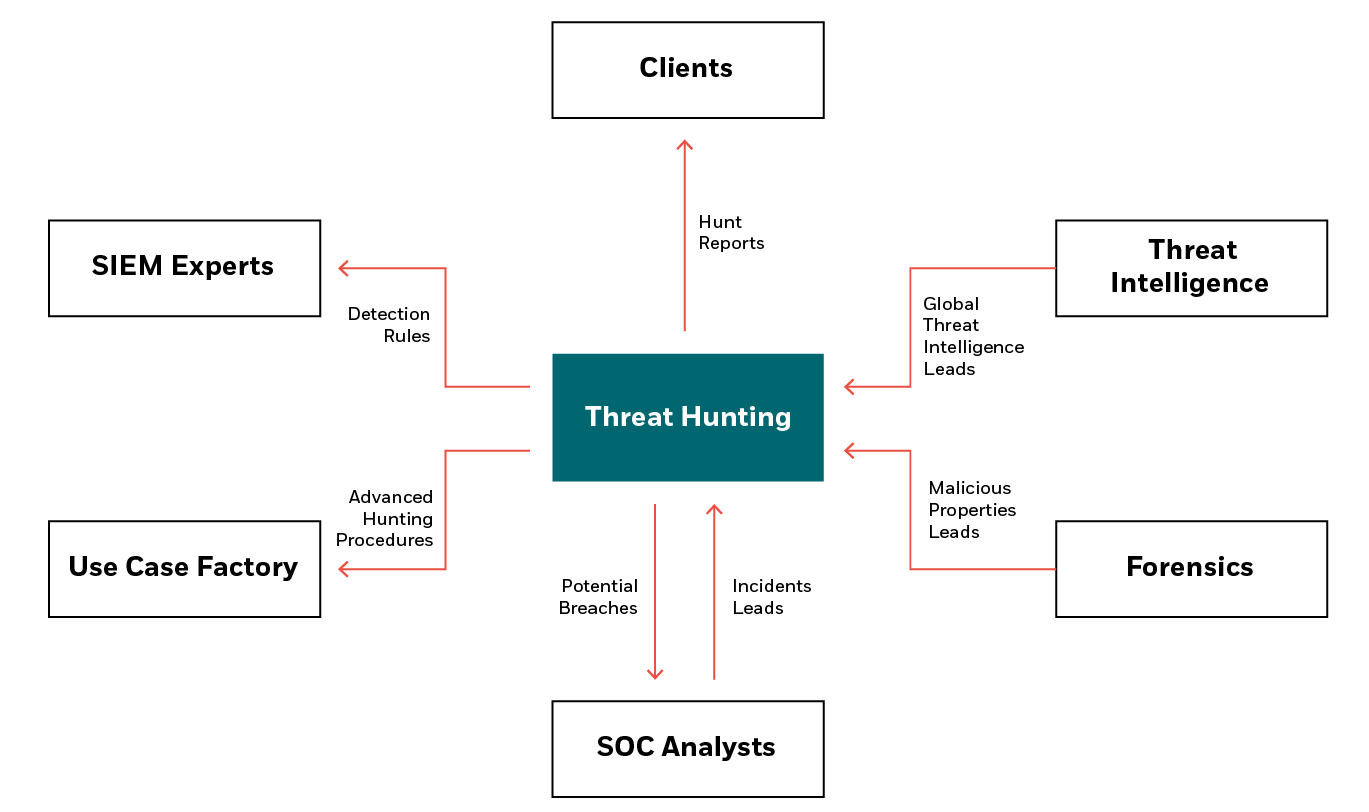
What are the benefits of proactive threat hunting?
Threat hunting strengthens an organization’s cybersecurity posture by moving from a reactive to a proactive approach for reducing risk. This has been found to:
- Identify a greater number of threats: 44% of attacks bypass traditional security defenses. Threat hunting teams are trained to find these risks.
- Ensure earlier detection of threats: The longer the dwell time, the greater the risk. Threat hunters use behavioral analysis to find malware and attackers faster.
- Improve incident response: A SOC team will be focused on the incident at hand. Threat hunters look for the plan B, and support the team with greater insight.
Another benefit of a threat hunting program is that it can support enterprises in finding unique threats which are targeted specifically at their network. We often get asked, “What is a structured threat?” and threat hunting is a robust way to alleviate any fear about this kind of cyberattack. Simply put, a structured threat is when cybercriminals use sophisticated skills and knowledge to attack a client’s network in a targeted way, rather than casting a wide net and hoping an attack makes it through. As threat hunting is not only relying on widespread IOCs or known attack patterns, structured threats are more likely to be uncovered when using cyber threat hunting services.
How does cyber threat hunting work?
Cyber threat hunting works best when threat hunters use a number of different threat hunting techniques to add layers of sophistication into their work. One example is the following threat hunting framework, which has six layers of distinct activity.
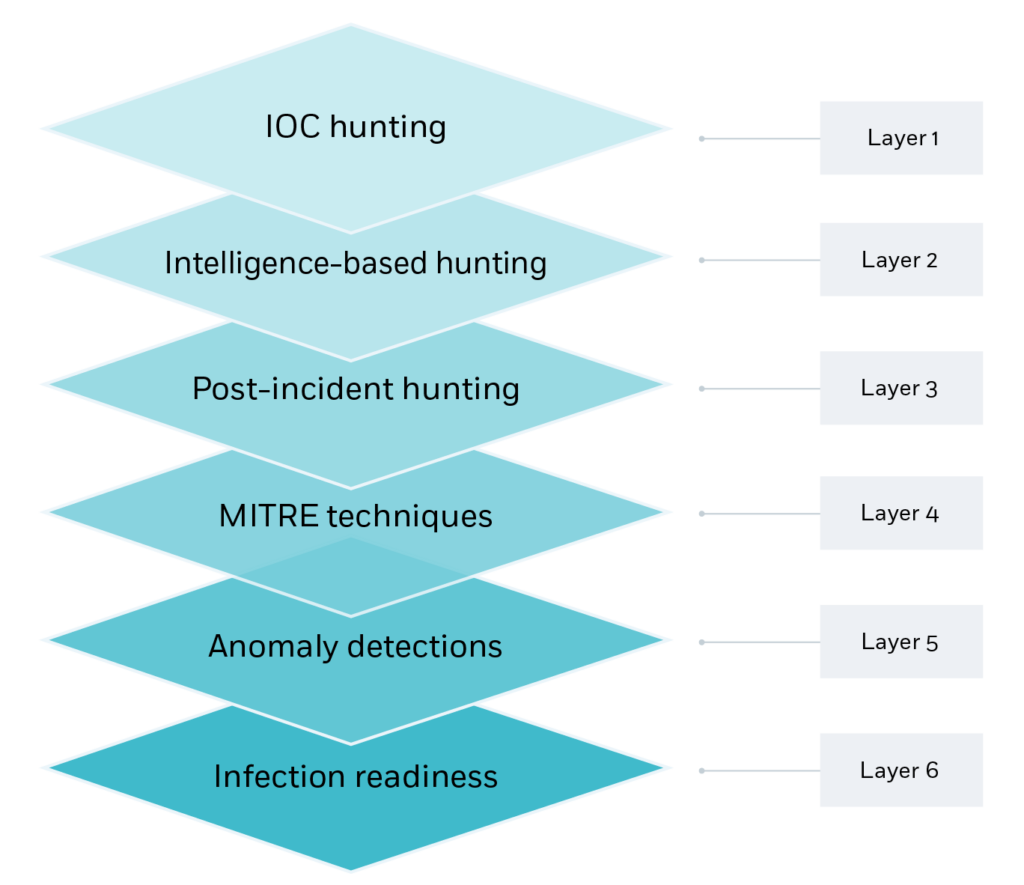
- IOC hunting: Retro-hunts using IOCs –i.e., where known IOCs are queried across the multiple tools used by the SOC, including EDR, SIEM, Proxy, Firewall, and more.
- Intelligence-based hunting: Reports are gathered and recent threats, techniques, and unpatched vulnerabilities are searched for in the environment.
- Post-incident hunting: Leveraging the incident report from an event, workflows are used to identify additional backdoors or infected hosts.
- MITRE techniques: After mapping the environment, any MITRE TTP blind spots are used to create a customized, dedicated plan for a specific organization.
- Anomaly detection: A wealth of data is used to detect anomalies from a customized baseline, such as cryptomining, malware beaconing or unauthorized data transfer.
- Infection readiness: As no threat hunting process is airtight, this layer is about hardening response, deploying deception, and preparing response for attack.
The five steps of threat hunting
There are proactive threat hunting hunting steps that an organization can take in order to ensure that their threat hunting approach is more successful.

The first step is to prepare baselines. Ask questions such as what applications and services are deployed on each endpoint, and which protocols are communicating with the network? Check for policy violations, for example at the endpoint or in the network.
Next, as threat hunting is a proactive pursuit, threat hunters should develop their hypothesis. Without a clear hypothesis, time can be wasted – as there is no clear goal in mind. Next, it’s important to focus in on a time frame, and to ascertain when the hunt will be called off if no evidence of infection occurs.
The penultimate step is to validate all the events that have been identified, calling out data that lines up with the hypothesis, and recognizing false positives. Finally, and critically – improve future threat hunting attempts by taking feedback and implementing detection rules where possible on what has been found.
Measuring the success of threat hunting techniques
Many people believe that in threat hunting, attacks need to be discovered in order to call the mission a success. In reality, there are many signs of a successful threat hunt. This could be anything from developing use cases for protecting a new cloud environment, to adding details to a threat hunting playbook or threat hunting guide that will help speed up the process next time around. If every time your threat hunting team delves into the network, they uncover signs of malware or an established foothold, they are probably looking at an extremely insecure network that needs to improve its defenses.
Best practices in threat hunting investigation types
Different organizations will approach threat hunting through their own specific lens. But from years in the industry, we’ve developed some best practices for threat hunting solutions, split into three categories.
- Choose the right people: In many organizations, threat hunting activities are handled by SOC teams, but in reality, threat hunting needs dedicated experts with highly technical skills.
- Create a practical plan: Threat hunters should validate the log coverage, and then create relevant baselines which are contextually suited to the specific organization. Once a baseline has been established, threat hunting teams need to create a multi-layered plan for the hunt.
- Utilize a holistic approach: A holistic approach is what makes a business one strong entity. Collaborating with the SOC is critical, and will help the organization to drive productivity. Whatever knowledge is available – make sure to share it!
How often should you threat hunt?
Threat hunting shouldn’t be performed ad-hoc, or just one hour a week or two hours a month. To be effective in reducing the attack surface, threat hunting should be a full-time job.
Threat hunting teams will work alongside other cybersecurity and intelligence teams, continually working to reduce the attack surface.
How to start proactive threat hunting?
As we have discussed, before the practical hunt can begin, threat hunting teams will need to form baselines by looking at existing data and logs. Here are a few examples of data that can be used to create different baselines:
- Environmental review: A baseline of the whole environment will include the OS, domain names, working hours in different branches, and naming conventions for assets such as endpoints, servers and services.
- Attack vectors: Which vectors are the most attacked, in which regions, and by what adversary groups? Understand which products are the least effective, and where initial access may have occurred.
- Endpoint and users: Who are the power users, what scripts are most regularly used, and what are common software tools that need to be whitelisted, or common services?
- Network and applications: Pen testing reports can be used to find known vulnerabilities, and the processes which have outbound communications, including what protocols and ports are utilized.
Threat hunting methodologies for complex enterprise environments
One important question that many clients ask is whether to consider automating threat hunting using threat hunting software, or looking for managed threat hunting services. The real answer is, both! While certain elements of threat hunting can be performed by a platform, the human element is critical.
For example, automation via threat hunting platforms can be used for visibility, to retrieve and consolidate data from different sources such as network sensors, cloud instances and the email gateway. However, hypothesis formation relies on a human understanding of attacker behavior, and how they might operate during a multi-stage attack.
At CyberProof, we automate as much as possible, for example using our Use Case Factory, but we never lose sight of the need for human input and expertise.
CyberProof’s proactive threat hunting services
At CyberProof, we have a dedicated threat hunting team, with experts who are continually focused on proactive threat hunting activities. Instead of building out a threat hunting team in-house, you can save valuable resources, and receive peace of mind that you are being protected by the most experienced and technical experts available.
Unlike other threat hunting services that rely on retro-hunting or basic intelligence feeds, we have access to a wide range of data and investigation methods, including incident and threat information from our SOC clients, and we lean on advanced procedures including incident and intelligence-based hunting, TTPs, and anomaly hunting. We use a multi-layered approach to threat hunting, fully developing baselines for any scenario, and creating a customized roadmap to adopt threat hunting, deepening and enhancing these strategies over time.
Interested in CyberProof’s advanced threat hunting services, and proactively searching for malware and attackers hiding in your network?
Speak to a threat hunting expert to learn more.
Frequently asked questions
What is cyber threat hunting?
What is meant by threat hunting?
What are cyber threats?
How does threat hunting work?
What are the types of threat hunting?
What are threat hunting tools?
Why is threat hunting important?
What are the 4 categories of threats?
Is threat hunting difficult?
RESOURCES
Learn more about Advanced Threat Hunting

Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.
SPEAK WITH AN EXPERT