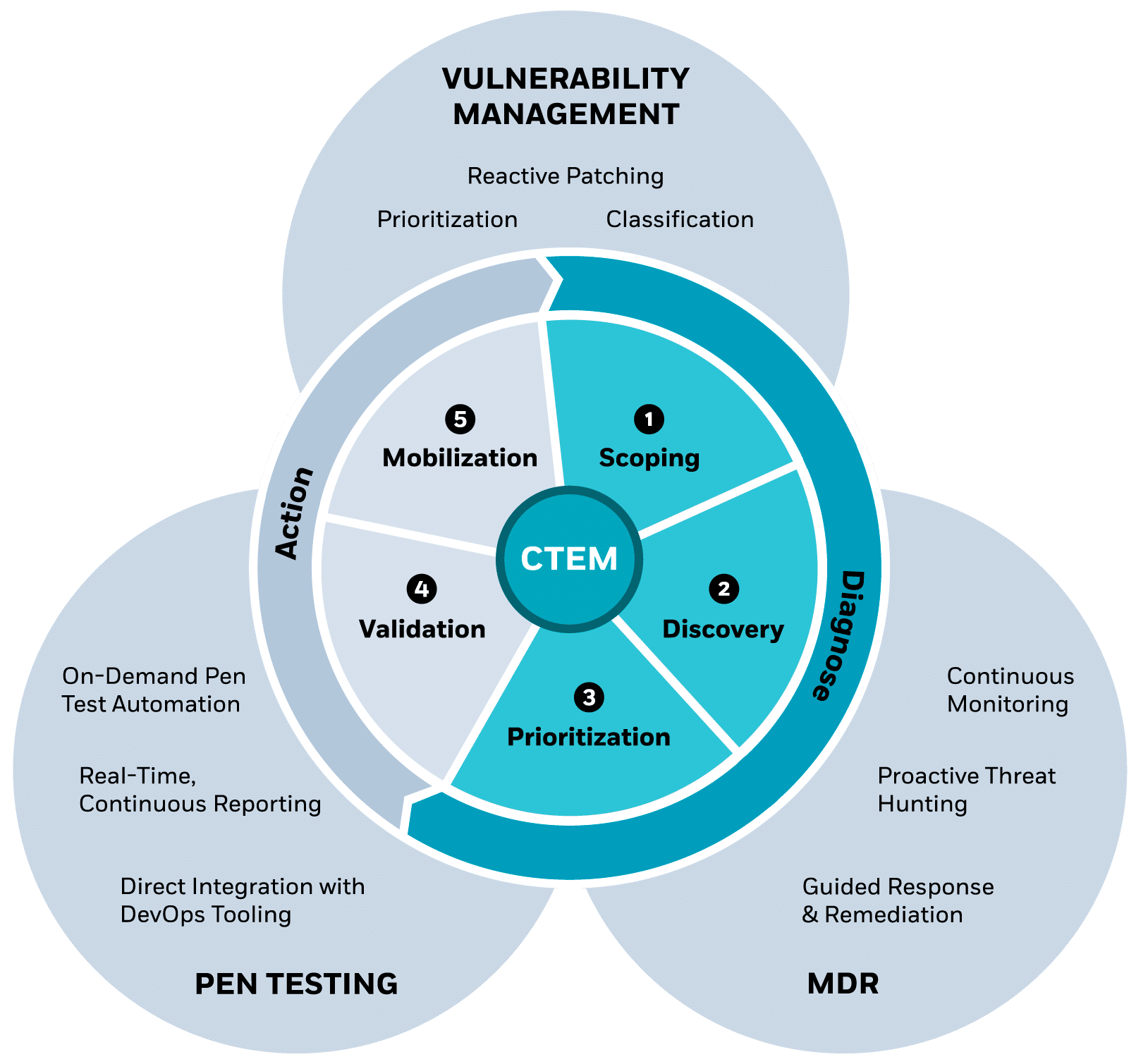
Continuous Threat Exposure Management (CTEM)
The CyberProof platform, powered by Interpres Security, enables an organization’s CTEM strategy. It helps enterprises understand their unique threat profile and focus resources on prioritized threats that matter. With a threat-led approach that’s different from other solutions in the market, CyberProof’s solution automatically curates TTP-based threat intelligence from an extensive set of sources to continuously provide operationalized context across your security ecosystem.
CyberProof’s platform enables your CTEM strategy and provides a real-time, ongoing view of your organization’s threat exposure enabling you to:

ANALYZE
Analyze the dynamic relationship between defensive and adversarial capabilities, assets, and vulnerabilities.

PRIORITIZE
Prioritize recommended actions to harden your defenses against specific threats that matter.

OPTIMIZE
Optimize your security ecosystem through continuous improvement to security posture, costs, and the number of overall threats.
RECOGNIZED AS INDUSTRY LEADERS
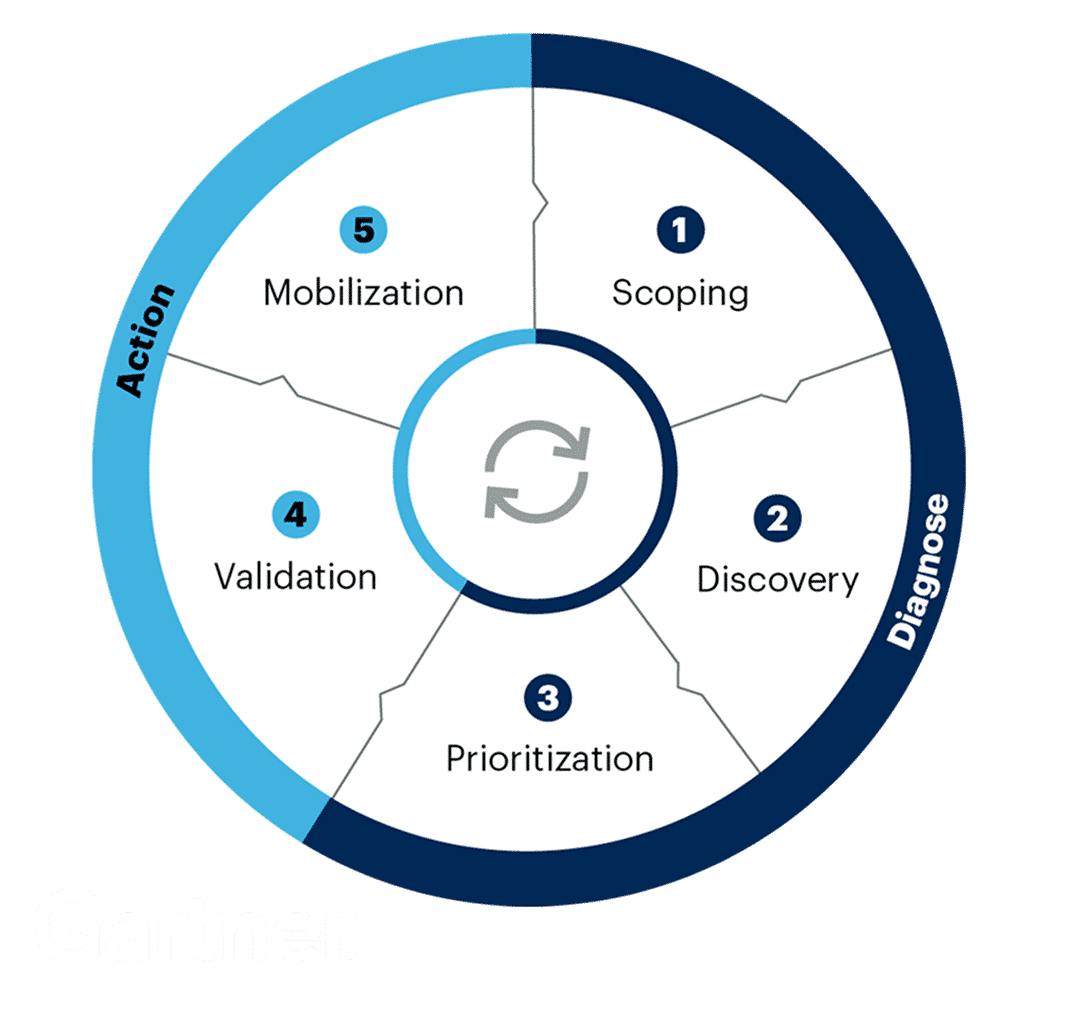
What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a proactive strategy for identifying, assessing, and mitigating security risks within an organization’s digital infrastructure. It involves ongoing monitoring of technology systems, threat intelligence feeds, and vulnerability databases to identify threats, vulnerabilities, and exposures that adversaries may exploit. Many enterprises are adopting CTEM programs to strengthen their security posture and focus resources on the most critical threats.
Revolutionizing Cybersecurity with CTEM and Interpres
The integration of CTEM capabilities into the CyberProof platform, powered by Interpres Security, elevates CyberProof’s services by delivering prioritized insights and automation across key cybersecurity domains. CTEM enhances efficiency, accuracy, and focus, allowing us to deliver faster, more effective threat management while reducing operational overhead.
Use Case Management (UCM)
CTEM automates the mapping of detection capabilities, weaknesses, and relevant threat intelligence, enabling engineers to focus on developing prioritized use cases that address critical risks with reduced manual effort.
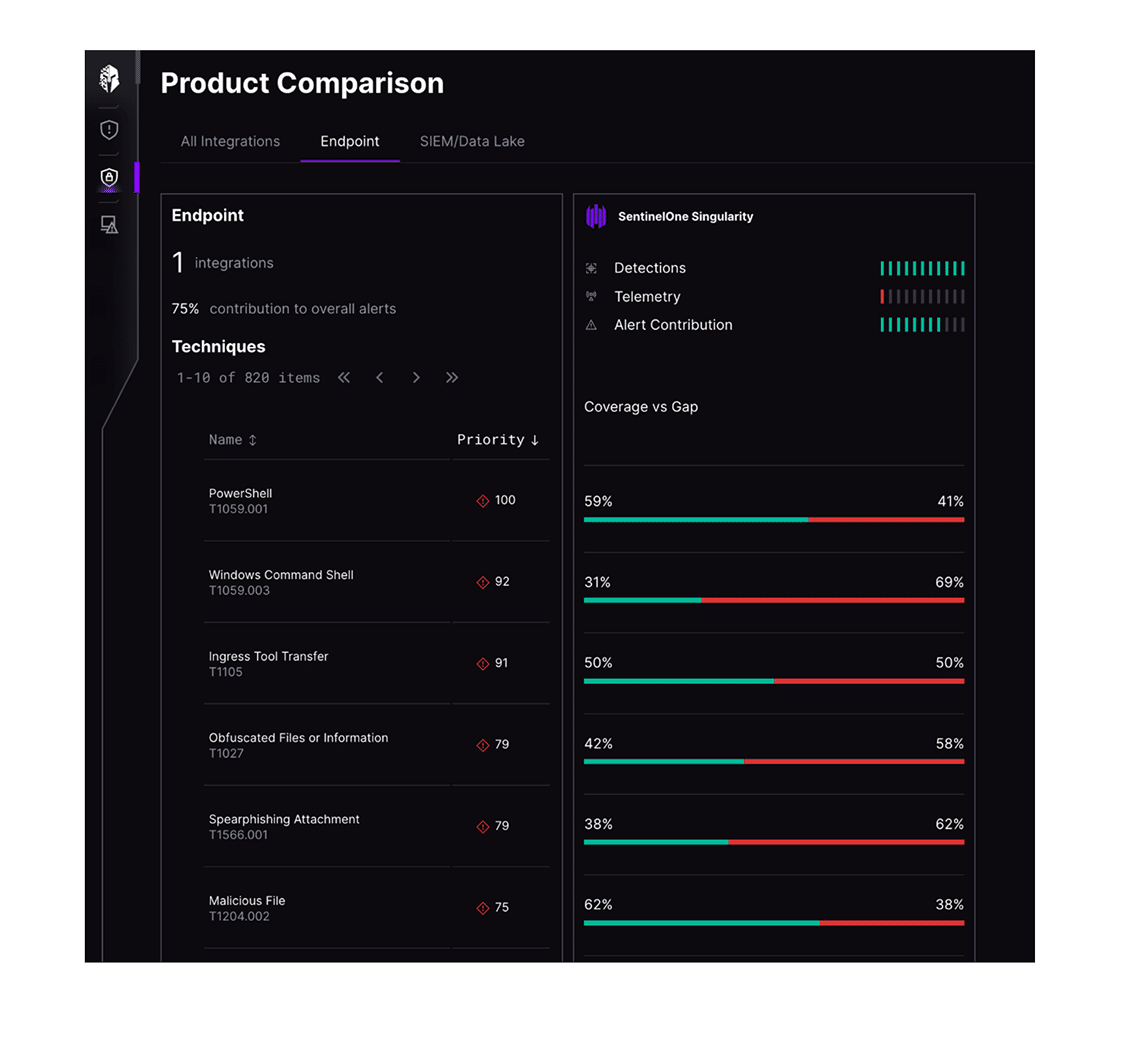
Vulnerability Management (VM)
CTEM enhances vulnerability prioritization by analyzing active exploit campaigns and linking them to specific assets, ensuring patching efforts are focused on the most urgent threats.
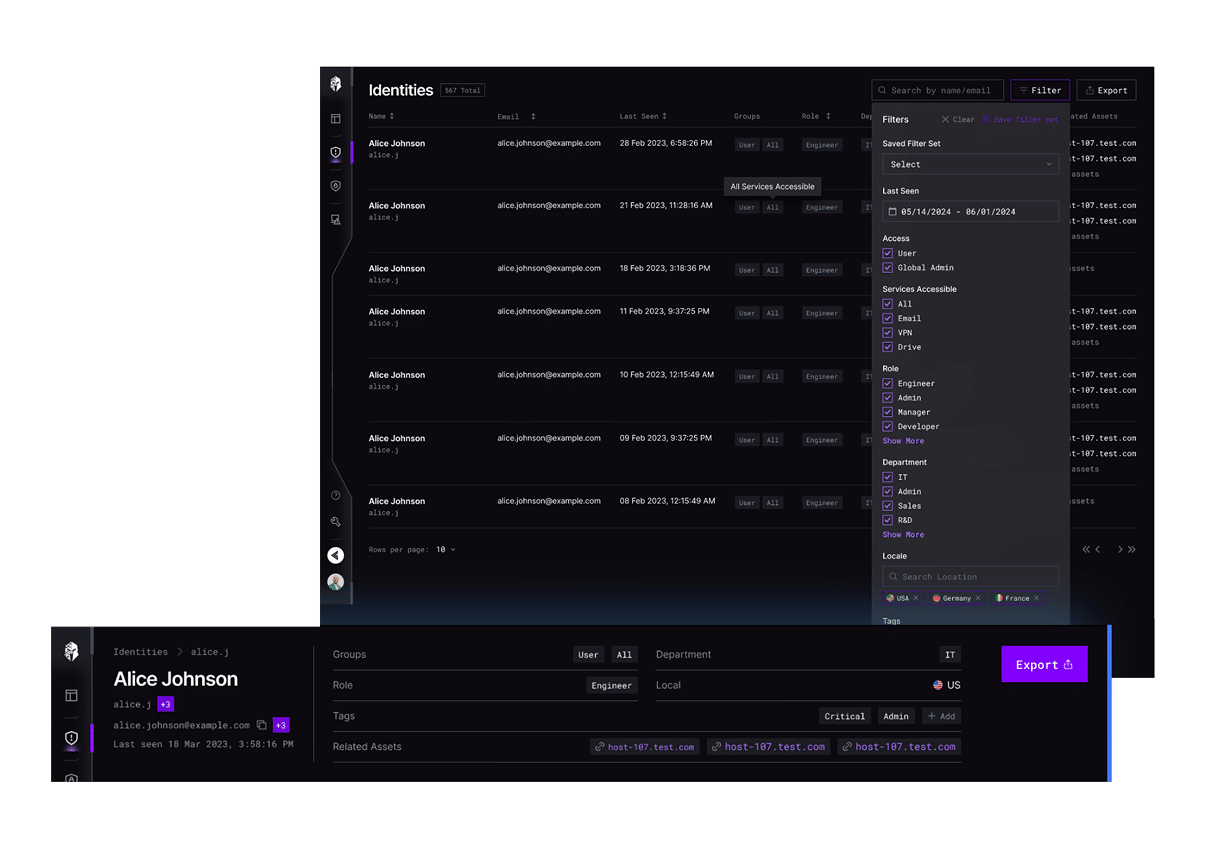
Threat Intelligence
CTEM streamlines the collation and filtering of multiple intelligence feeds into a clean, actionable dataset, freeing analysts to focus on validating TTPs and crafting advanced detection rules.
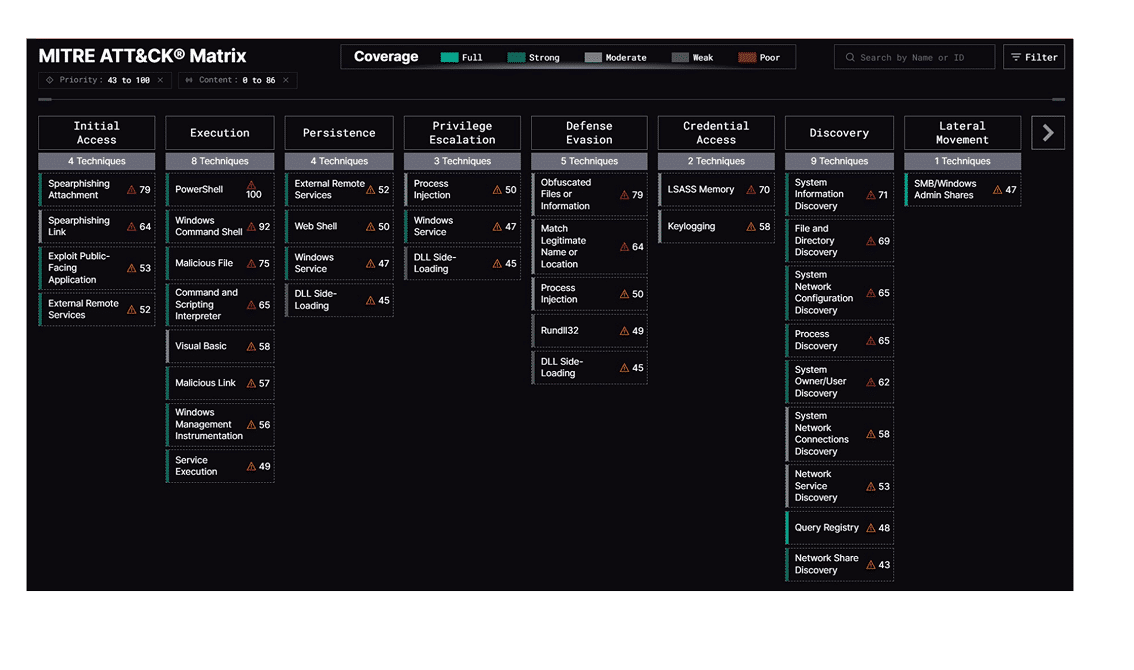
Managed Detection and Response (MDR)
CTEM improves alert prioritization by dynamically correlating vulnerable assets with active campaigns, enabling faster and more targeted responses to emerging threats.
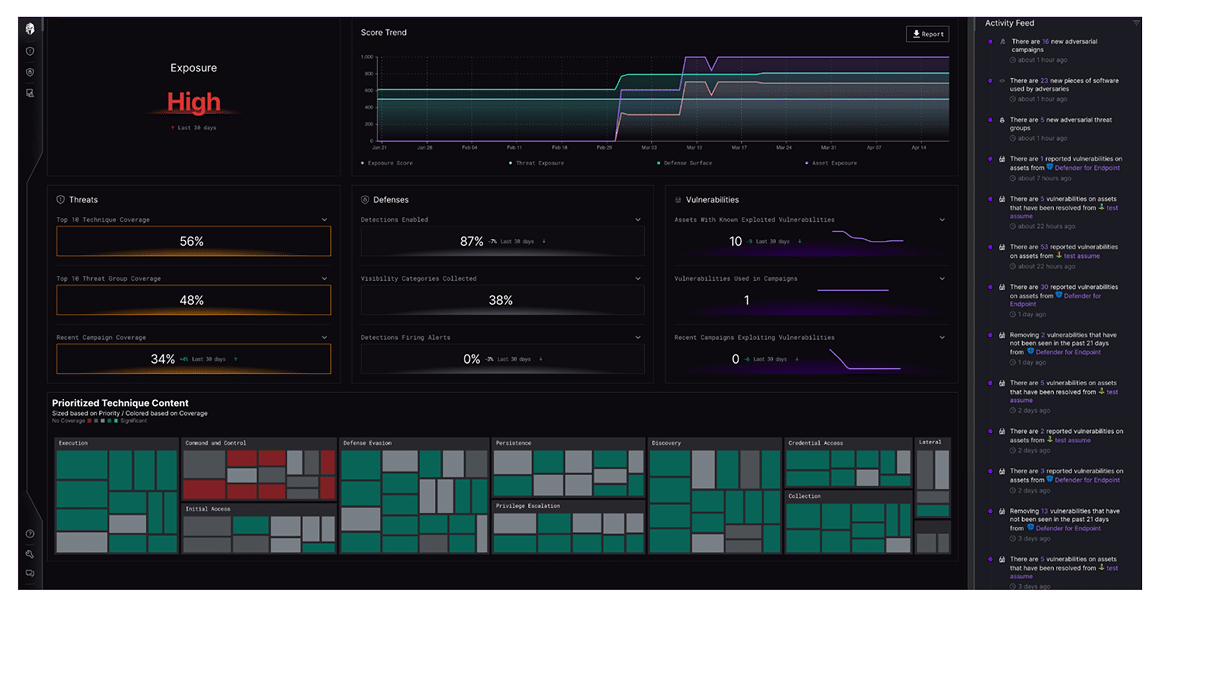




With the acquisition and integration of Interpres Security, CyberProof has become the first and only managed security service company to provide a seamless, risk-prioritized view of your exposure and defenses against the most relevant threat actors targeting your industry.

Harnessing Interpres Security’s CTEM & ASCA Technology
Powered by Interpres Security, CyberProof’s CTEM and ASCA technology stands out with its holistic approach to continuous threat exposure management, offering a comprehensive solution that covers the entire cybersecurity lifecycle—from identifying threat actors and campaigns to evaluating exposure and defensive gaps. By integrating Interpres’ technology with CyberProof’s cyber defense services like MDR, Vulnerability Management, and Pen Testing, organizations gain continuous, automated risk exposure assessments, while optimizing defense management technology and tools to stay ahead of evolving threats.

Understand Your Top Threats and Vulnerabilities
Here’s what you can expect from CyberProof’s solution:
- Identify the most significant threats likely to target your organization.
- Establish a baseline for your current risk exposure and assess your organization’s cyber defense readiness.
- Prioritize exploitable vulnerabilities that adversaries are leveraging against businesses like yours.
- Ensure your detection and prevention controls are aligned with the most critical threats and vulnerabilities.
- Continuously update detection rules and playbooks to reflect relevant business use cases.
- Identify coverage gaps in your security posture against industry standards and best practices.
- Receive tailored recommendations to optimize and enhance your overall security framework.


Manage Risk and Drive Security Business Priorities
The CyberProof platform not only gives you visibility into the threats that matter, but helps you monitor report and prioritize the risk of your business at the board level.
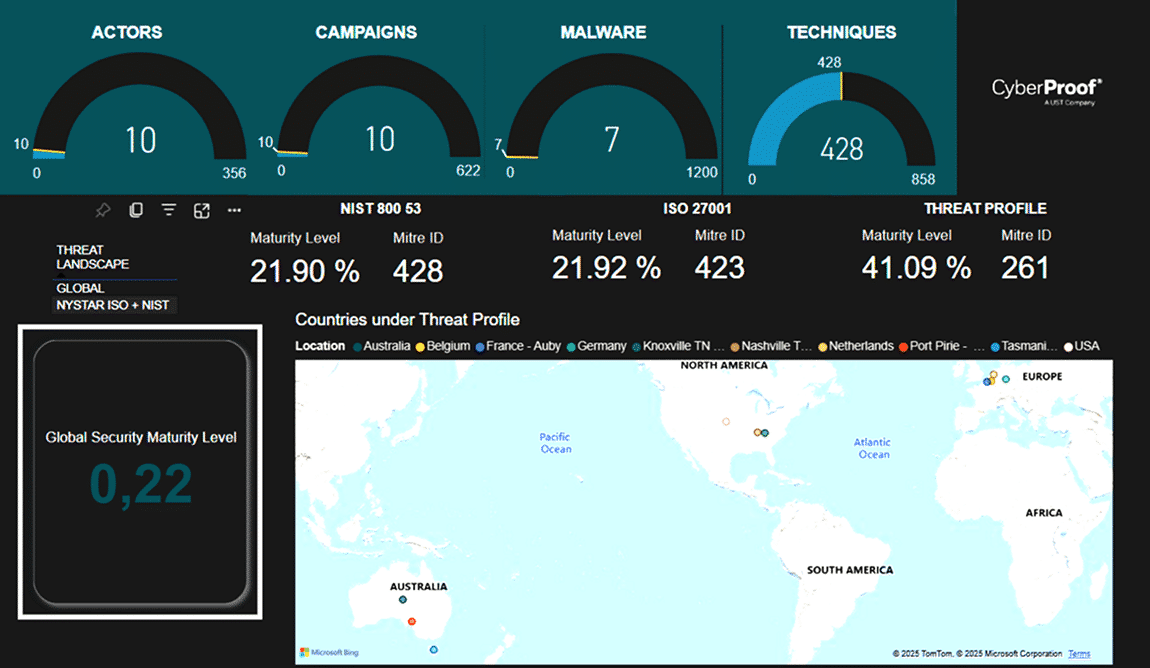

Who coined the term “CTEM”?
The term Continuous Threat Exposure Management (CTEM) was introduced by Gartner in July 2022, highlighting the need for organizations to better assess and prioritize vulnerabilities and threats. Gartner coined CTEM to promote a more proactive and dynamic cybersecurity approach, focused on continuous evaluation and prioritization to effectively manage and reduce risks.
Gartner predicts that by 2026, organizations implementing CTEM programs will be three times less likely to experience a cyberattack compared to those that don’t, underscoring its potential to strengthen defenses against cyber threats.