Google Chronicle, a powerful security operations platform, provides robust capabilities for threat detection, investigation, and response. Leveraging cutting-edge AI technologies, such as Google’s Gemini, Chronicle transforms security operations, making them more efficient and effective.
Google Chronicle integrates seamlessly with various AI systems, utilizing natural language processing (NLP) and deep learning to enhance security analysts’ capabilities. By understanding the nuances of security events and providing actionable insights, Chronicle helps organizations maintain a proactive security posture. This article explores the key features and benefits of Google Chronicle, focusing on its integration with Gemini, responsible AI practices, and the future of AI in security operations.
Introduction to Google Chronicle
Google Chronicle, and it application within Managed Detection and Response (MXDR), is an advanced security operations platform designed to enhance the capabilities of cybersecurity teams by leveraging the power of artificial intelligence (AI) and machine learning (ML). As cyber threats become increasingly sophisticated, the need for effective threat detection, investigation, and response tools is more critical than ever. Chronicle addresses this need by offering a comprehensive suite of features that streamline and optimize security operations.
One of the standout features of Google Chronicle is its integration with Gemini, a suite of AI tools that utilizes natural language processing (NLP) and deep learning. This integration allows security professionals to interact with the system using natural language queries, making it easier to search, analyze, and investigate security events. Gemini’s capabilities extend beyond simple search functions; it can generate rules, provide incident remediation suggestions, and offer detailed threat intelligence analysis.
In addition to its robust security features, Google Chronicle is designed to be user-friendly, allowing security operations center (SOC) managers, chief information security officers (CISOs), and chief information officers (CIOs) to manage security events effectively. Its intuitive interface and powerful AI-driven tools make it an invaluable asset in the fight against cyber threats.
The following sections will delve into the specific features and capabilities of Google Chronicle, demonstrating how it revolutionizes security operations and provides organizations with the tools they need to stay ahead of evolving threats.
Features of Google Chronicle
Google Chronicle offers a range of features designed to enhance security operations by leveraging the latest advancements in artificial intelligence and machine learning. These features streamline the processes of threat detection, investigation, and response, making it easier for security teams to protect their organizations from cyber threats.
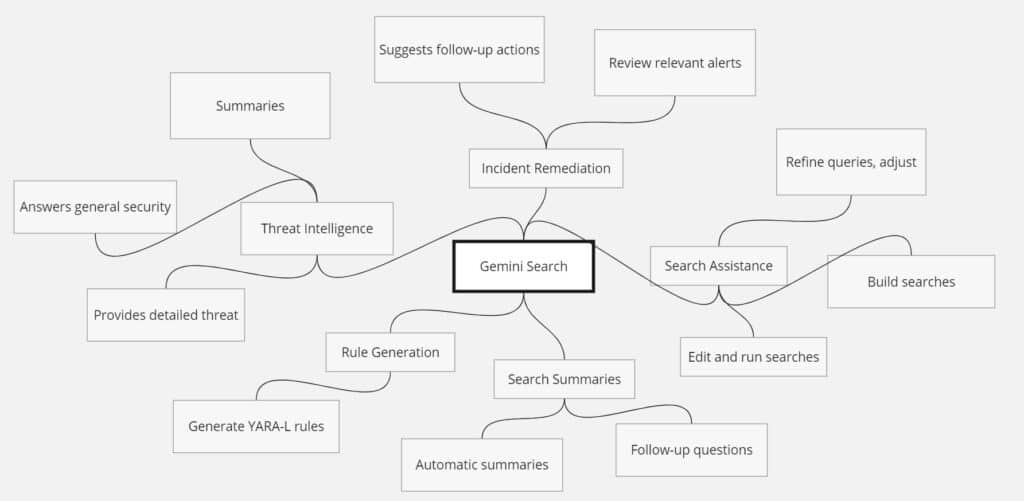
Access to Gemini in Google SecOps
Gemini, a suite of large language models integrated within Google SecOps, plays a pivotal role in enhancing Google Chronicle’s capabilities.
Key Features of Gemini in Google SecOps:
- Search Assistance: Gemini helps build, edit, and run searches using natural language prompts. This capability allows security analysts to interact with the system more intuitively, refining search queries, adjusting scopes, expanding time ranges, and adding filters effortlessly.
- Search Summaries: After each search, Gemini provides automatic summaries of the results, presenting the information in a concise and understandable format. Analysts can also ask follow-up questions to delve deeper into the summaries provided.
- Rule Generation: Gemini can generate YARA-L rules from UDM search queries, streamlining the creation of new security rules based on search results.
- Threat Intelligence and Security Questions: Gemini answers general security questions and provides detailed threat intelligence, including summaries about threat actors, indicators of compromise (IOCs), and other critical information.
- Incident Remediation: Based on the event information returned, Gemini suggests follow-up actions, such as reviewing relevant alerts or filtering specific hosts or users.
Google Chronicle Security and Data Governance
Ensuring the security and proper governance of data is a top priority for Google Chronicle. The platform incorporates several features to protect sensitive information and comply with industry standards.
Key Security and Data Governance Features:
- Data Processing and Routing: Data is processed in various global regions, ensuring that customer requests are handled efficiently and securely.
- Certifications: Gemini in Google SecOps complies with numerous certifications, ensuring adherence to industry standards and best practices.
- Data Governance Practices: The platform follows stringent data governance practices to ensure that data is used responsibly and securely. Detailed documentation on how Gemini uses data is available to help organizations understand and comply with these practices.
By integrating these robust security and data governance features, Google Chronicle provides a secure and efficient environment for managing security operations. The following sections will explore how Gemini’s natural language processing capabilities and AI-driven tools further enhance the platform’s effectiveness in threat detection and incident response.
Gemini and Natural Language Processing (NLP) in Security Operations
Gemini, integrated within Google Chronicle, leverages advanced natural language processing (NLP) capabilities to transform security operations. By enabling security analysts to interact with the system using natural language, Gemini simplifies the process of searching, investigating, and responding to security events.
Search and Investigation Capabilities
One of the core strengths of Gemini in Google Chronicle is its powerful search and investigation capabilities. These features allow security teams to quickly and efficiently find relevant security events and gain insights into potential threats.
Key Search and Investigation Features:
- Natural Language Search: Analysts can enter search queries in natural language, making it easier to find specific events or data points. For example, a query like “Show me all failed logins for the last 7 days” can be entered directly, and Gemini will generate the appropriate UDM search query.
- Search Summaries: After executing a search, Gemini provides automatic summaries of the results. These summaries help analysts quickly understand the key findings and decide on the next steps.
- Iterative Search: Analysts can refine their searches by adding follow-up questions or modifying the original query. Gemini supports this iterative process, allowing for a more in-depth investigation.
- Contextual Follow-Up: Gemini can answer contextual follow-up questions based on the search results, providing deeper insights and aiding in thorough investigations.
Incident Remediation and Response
In addition to its search capabilities, Gemini offers powerful tools for incident remediation and response. These features help security teams respond to threats more effectively and mitigate potential damage.
Key Incident Remediation Features:
- Rule Generation: Gemini can generate YARA-L rules based on UDM search queries. For instance, a prompt like “Generate a rule to detect logins from firstname.lastname” will result in a specific rule to monitor such activities.
- Suggested Actions: Based on the search results, Gemini suggests follow-up actions, such as reviewing specific alerts, filtering results by user or host, or taking other remediation steps.
- Incident Insights: Gemini provides detailed insights into incidents, helping analysts understand the context and severity of the threat. This includes information about threat actors, their tactics, techniques, and procedures (TTPs), and potential impact.
Example Remediation Prompts:
- “Generate a rule to help detect repeated failed login attempts.”
- “Show me events associated with a specific user and suggest follow-up actions.”
By integrating advanced NLP capabilities and AI-driven tools, Gemini in Google Chronicle significantly enhances the efficiency and effectiveness of security operations. The next section will explore how AI systems are leveraged for problem-solving and integration with Google Workspace, further empowering security teams.
Leveraging Google Chronicle’s AI Systems for Problem Solving
Google Chronicle, through its integration with advanced AI systems like Gemini, significantly enhances the problem-solving capabilities of security teams. By leveraging AI models, training data, and seamless integration with Google Workspace, Chronicle empowers security professionals to tackle complex security challenges more efficiently and effectively.
AI Models and Training Data
At the heart of Google Chronicle’s advanced capabilities are sophisticated AI models and extensive training data. These models, including large language models (LLMs), are trained on diverse datasets to ensure they can handle a wide range of security scenarios.
Key Aspects of AI Models and Training Data:
- Deep Learning: Google Chronicle uses deep learning techniques to train its AI models. This approach enables the models to recognize patterns and make predictions based on vast amounts of data, mimicking the way the human brain processes information.
- Comprehensive Training Data: The AI models are trained on a variety of data sources, including security blogs, threat intelligence reports, malware scripts, and vulnerability information. This extensive training helps ensure that the models are well-equipped to handle real-world security challenges.
- Specialized Models: In addition to general-purpose AI models, Google Chronicle includes specialized models like Sec-PaLM, which is trained on data specific to security operations. This specialization enhances the accuracy and relevance of the AI’s insights and recommendations.
Benefits of Google Chronicle’s AI Models and Training Data:
- Enhanced Detection: The AI models can detect nuanced security threats that might be missed by traditional methods.
- Improved Response: By leveraging extensive training data, the models can provide more accurate and actionable recommendations for incident response.
- Scalability: The use of AI models allows Google Chronicle to scale its capabilities to handle large volumes of security data efficiently.
Integration between Google Chronicle and Google Workspace
Google Chronicle’s integration with Google Workspace further enhances its utility for security teams. This seamless integration allows for better collaboration, data sharing, and streamlined workflows.
Key Integration Features:
- Unified Platform: By integrating with Google Workspace, Chronicle provides a unified platform where security teams can access all the tools and data they need. This integration eliminates the need for switching between multiple applications, saving time and reducing the risk of errors.
- Real-Time Collaboration: Security teams can collaborate in real-time using Google Workspace tools like Google Docs, Sheets, and Slides. This real-time collaboration is crucial during incident response, where timely communication and coordination are essential.
- Data Sharing and Access: Google Workspace integration ensures that security teams have easy access to relevant data and can share insights quickly. For example, security alerts and investigation findings can be shared directly within Google Workspace applications, facilitating prompt action.
Benefits of Google Workspace Integration:
- Streamlined Workflows: Integration with Google Workspace simplifies workflows, making it easier for security teams to manage their tasks and collaborate effectively.
- Enhanced Efficiency: Real-time collaboration and easy data sharing enhance the efficiency of security operations, allowing teams to respond to threats more swiftly.
- Improved Accessibility: Security teams can access and manage their tools and data from a single platform, improving accessibility and usability.
By leveraging advanced AI models and training data, along with seamless integration with Google Workspace, Google Chronicle significantly enhances the problem-solving capabilities of security teams. The next section will explore practical applications of Google Chronicle, including generating UDM search queries and creating YARA-L rules.
Google Chronicle in Action
Google Chronicle stands out for its practical applications that streamline and enhance security operations. Through features like generating UDM search queries and creating YARA-L rules, Chronicle empowers security teams to handle complex security challenges with greater efficiency and precision.
Generating UDM Search Queries
One of the key capabilities of Google Chronicle is its ability to generate Unified Data Model (UDM) search queries using natural language prompts. This feature simplifies the process of searching and analyzing security data, making it more accessible even to those without deep technical expertise.
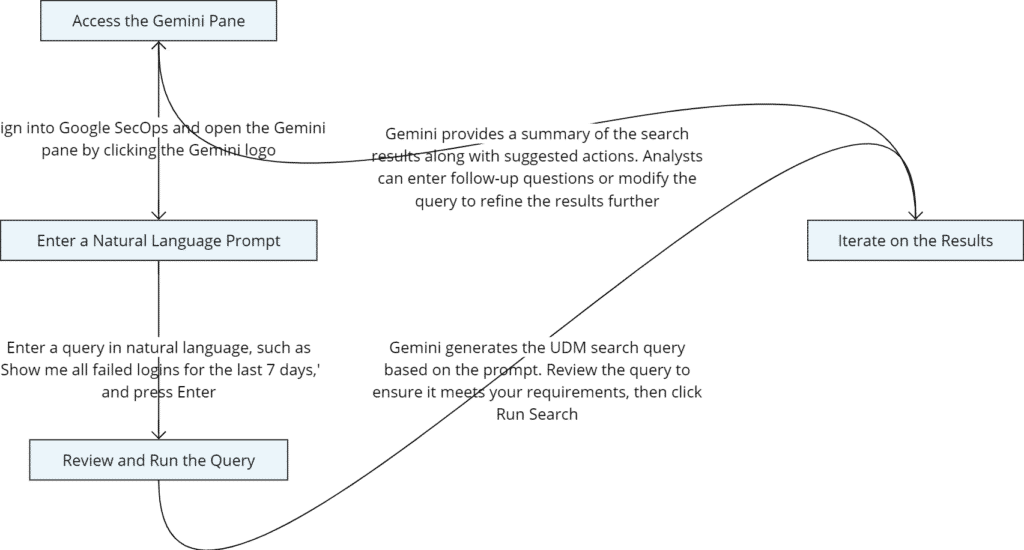
Steps to Generate UDM Search Queries:
- Access the Gemini Pane: Sign into Google SecOps and open the Gemini pane by clicking the Gemini logo.
- Enter a Natural Language Prompt: Enter a query in natural language, such as “Show me all failed logins for the last 7 days,” and press Enter.
- Review and Run the Query: Gemini generates the UDM search query based on the prompt. Review the query to ensure it meets your requirements, then click Run Search.
- Iterate on the Results: Gemini provides a summary of the search results along with suggested actions. Analysts can enter follow-up questions or modify the query to refine the results further.
Example Prompts:
- “Create a rule to monitor for multiple failed login attempts within a short time frame.”
- “Identify all outbound network connections to suspicious websites.”
- “Show firewall event logs from the last 24 hours.”
Benefits of UDM Search Queries:
- Ease of Use: Natural language processing makes it easier for analysts to formulate complex queries without needing extensive technical knowledge.
- Efficiency: Quickly generate accurate search queries, saving time and reducing the effort required for data analysis.
- Flexibility: Easily modify and iterate on search queries to hone in on the most relevant security events.
Creating YARA-L Rules in Google Chronicle
Another powerful feature of Google Chronicle is the ability to create YARA-L rules using natural language prompts. YARA-L rules are essential for identifying and categorizing malware, making them a crucial tool in the security analyst’s arsenal.
Steps to Create YARA-L Rules:
- Enter a Natural Language Prompt: Use a prompt like “Create a rule to detect logins from firstname.lastname” in the Gemini pane.
- Review the Generated Rule: Gemini generates a YARA-L rule based on the prompt. Review the rule to ensure it meets your needs.
- Modify and Save the Rule: Click “Open in rule editor” to view and modify the rule in the Rules Editor. Once satisfied, click “Save New Rule” to activate it.
- Activate the Rule: The new rule appears in the list of rules. Toggle the “Live Rule” option to activate it.
Example Rule Prompt:
- Create a rule to identify logins originating from unauthorized locations.
- Generate a rule to detect unusual file modifications.
Benefits of YARA-L Rules:
- Automation: Automate the creation of complex rules, reducing the time and effort required by security analysts.
- Precision: Generate precise and effective rules tailored to specific security needs and scenarios.
- Scalability: Easily create and manage multiple rules to address various security threats.
By leveraging features like generating UDM search queries and creating YARA-L rules, Google Chronicle enhances the practical capabilities of security teams, enabling them to respond more effectively to threats. The following section will delve into responsible AI practices and the ethical considerations surrounding the use of AI in security operations.
Responsible AI and Ethical Considerations
As AI technologies become increasingly integrated into security operations, it is essential to address the ethical considerations and ensure responsible use of these powerful tools. Google Chronicle, through its integration with Gemini, emphasizes responsible AI practices, ensuring that the deployment of AI in security operations is both ethical and effective.
Human Intelligence and AI Synergy
The synergy between human intelligence and AI is a cornerstone of responsible AI use in Google Chronicle. By combining the strengths of both, security operations can be significantly enhanced.
Key Aspects of Human-AI Synergy:
- Augmentation, Not Replacement: AI in Google Chronicle is designed to augment human intelligence, not replace it. This approach ensures that security analysts remain in control, using AI to enhance their capabilities and efficiency.
- Decision Support: AI provides valuable decision support by analyzing vast amounts of data and presenting actionable insights. However, the final decision-making authority rests with human analysts, ensuring that ethical considerations and contextual understanding are applied.
- Continuous Learning: The interaction between human analysts and AI systems like Gemini is a continuous learning process. Analysts provide feedback on AI-generated outputs, helping to improve the system’s accuracy and relevance over time.
Benefits of Human-AI Synergy:
- Enhanced Capabilities: AI enhances the capabilities of human analysts, enabling them to detect and respond to threats more effectively.
- Reduced Workload: By automating routine tasks and providing decision support, AI reduces the workload on security teams, allowing them to focus on more complex and strategic issues.
- Improved Accuracy: The combination of human judgment and AI analysis improves the overall accuracy and reliability of security operations.
Ensuring Responsible AI Use
Google Chronicle is committed to ensuring that its AI technologies are used responsibly. This commitment involves implementing best practices and adhering to ethical guidelines to safeguard against potential risks and biases.
Key Practices for Responsible AI Use:
- Transparency: Google Chronicle maintains transparency in how AI models are trained and deployed. Clear documentation and user guides help security teams understand how AI works and how to interact with it effectively.
- Bias Mitigation: Efforts are made to identify and mitigate biases in AI models. This includes using diverse training data and continuously monitoring AI outputs for signs of bias or unfairness.
- User Privacy: User privacy is a top priority. Google Chronicle adheres to strict data governance practices to ensure that user data is handled responsibly and securely. User history and conversation data with Gemini are never used to train models, preserving privacy and confidentiality.
- Feedback Mechanisms: Users are encouraged to provide feedback on AI-generated outputs. This feedback loop helps improve the system’s performance and ensures that it aligns with the needs and expectations of security teams.
Ethical Considerations:
- Accountability: Clear accountability mechanisms are in place to ensure that AI-driven decisions can be traced and reviewed. This accountability is crucial for maintaining trust and ensuring that AI use aligns with ethical standards.
- Fairness: AI systems are designed to operate fairly and without discrimination. Continuous efforts are made to ensure that AI models treat all data and users equitably.
- Safety: The safety and security of AI systems are paramount. Rigorous testing and validation processes are in place to ensure that AI tools do not introduce new vulnerabilities or risks.
By focusing on responsible AI practices and ethical considerations, Google Chronicle ensures that its AI-driven security operations are not only effective but also align with the highest standards of integrity and fairness. The next section will explore the future of AI in security operations, including advancements in deep learning and computer vision.
Future of AI in Security Operations
The future of AI in security operations is promising, with advancements in technologies like deep learning and computer vision paving the way for more robust and effective security solutions. Google Chronicle is at the forefront of these innovations, continually enhancing its capabilities to meet the evolving needs of security teams.
Advances in Deep Learning and Computer Vision
Deep learning and computer vision are two areas where AI is making significant strides, offering new possibilities for enhancing security operations.
Key Advances in Deep Learning:
- Enhanced Threat Detection: Deep learning models are capable of analyzing vast amounts of data to identify patterns and anomalies that might indicate a security threat. These models learn from historical data and continuously improve their detection capabilities.
- Behavioral Analysis: By analyzing user and entity behaviors, deep learning models can detect deviations from normal patterns that may suggest malicious activity. This behavioral analysis is crucial for identifying advanced persistent threats (APTs) and insider threats.
- Automated Response: Deep learning enables more accurate and timely automated responses to security incidents. For example, when a threat is detected, the system can automatically isolate affected systems, block malicious activities, and alert security teams.
Key Advances in Computer Vision:
- Surveillance and Monitoring: Computer vision technologies can enhance surveillance systems by automatically detecting and recognizing suspicious activities in real-time. This capability is particularly useful for monitoring critical infrastructure and sensitive areas.
- Image and Video Analysis: AI-driven image and video analysis can identify security threats that might be missed by human operators. For example, computer vision can detect unauthorized access, identify weapons, or recognize known threat actors from video feeds.
- Integration with Existing Systems: Computer vision can be integrated with existing security systems, such as CCTV cameras and access control systems, to provide a more comprehensive security solution.
Benefits of Advances in Deep Learning and Computer Vision:
- Improved Accuracy: Advanced AI models offer higher accuracy in threat detection and analysis, reducing false positives and ensuring that real threats are addressed promptly.
- Proactive Security: AI enables proactive security measures by predicting potential threats and enabling preemptive actions. This proactive approach helps prevent incidents before they occur.
- Scalability: AI-driven solutions can scale to handle large volumes of data and monitor extensive networks, making them suitable for organizations of all sizes.
AI Research and Innovations
Ongoing AI research and innovations continue to drive the development of new security capabilities. Google Chronicle is committed to staying at the cutting edge of these advancements to provide the most effective security solutions.
Key Areas of AI Research and Innovations:
- Generative AI: Innovations in generative AI are creating new opportunities for automating and enhancing security operations. For example, generative models can create realistic simulations of cyber-attacks to test and improve security defenses.
- Natural Language Processing (NLP): Advances in NLP are enhancing the ability of AI systems to understand and respond to complex security queries. Improved NLP capabilities allow for more intuitive interactions between security teams and AI tools.
- AI Ethics and Fairness: Research into AI ethics and fairness ensures that AI systems are developed and deployed responsibly. This research focuses on eliminating biases, ensuring transparency, and maintaining user trust.
Future Directions for Google Chronicle:
- Integration of Emerging Technologies: Google Chronicle plans to integrate emerging AI technologies to enhance its security capabilities further. This includes leveraging advancements in quantum computing and blockchain for security applications.
- User-Centric Innovations: Future developments will focus on user-centric innovations, making AI tools more accessible and easier to use for security professionals. This includes improving user interfaces and expanding natural language capabilities.
- Collaboration with the Security Community: Google Chronicle will continue to collaborate with the broader security community to share insights, develop best practices, and stay ahead of emerging threats.
By embracing advances in deep learning, computer vision, and other AI technologies, Google Chronicle is poised to lead the future of security operations. These innovations will enable more effective threat detection, proactive security measures, and seamless integration with existing systems, ensuring that organizations can stay ahead of the ever-evolving cyber threat landscape.
Conclusion
In the dynamic and ever-evolving landscape of cybersecurity, Google Chronicle stands out as a transformative platform that leverages advanced AI technologies to enhance security operations. By integrating tools like Gemini, which harness natural language processing (NLP) and deep learning, Chronicle provides security teams with powerful capabilities for threat detection, investigation, and response.
Google Chronicle’s ability to generate UDM search queries and create YARA-L rules using natural language prompts simplifies complex security tasks, making advanced security operations accessible even to those without deep technical expertise. This functionality not only improves the efficiency of security teams but also enhances their ability to respond to threats swiftly and accurately.
The platform’s commitment to responsible AI practices ensures that the deployment of AI in security operations is both ethical and effective. By emphasizing the synergy between human intelligence and AI, Google Chronicle augments the capabilities of security analysts while maintaining transparency, fairness, and accountability.
Looking ahead, the future of AI in security operations is promising, with advancements in deep learning, computer vision, and other AI technologies paving the way for more robust and proactive security measures. Google Chronicle is poised to lead these advancements, continually innovating to meet the evolving needs of security teams and ensuring that organizations can stay ahead of emerging threats.
By embracing these cutting-edge technologies and maintaining a focus on responsible AI use, Google Chronicle provides a comprehensive and effective solution for modern security challenges. Security teams, including CISOs, CIOs, and SOC Managers, can rely on Google Chronicle to enhance their operations, streamline workflows, and improve their overall security posture.
In summary, Google Chronicle represents a significant advancement in the field of security operations, offering a blend of sophisticated AI capabilities and responsible practices. This combination ensures that organizations are well-equipped to navigate the complexities of cybersecurity and maintain a proactive stance against potential threats.







