Introduction to Google Chronicle and Its Impact on Modern Cybersecurity
In an era where cyber threats are becoming increasingly sophisticated, the demand for more advanced security information and event management (SIEM) tools has never been higher. Google Chronicle emerges as a pivotal solution in this landscape, redefining the capabilities of SIEM and security orchestration, automation, and response (SOAR) systems. This platform, developed atop Google’s robust infrastructure, offers unprecedented speed and scalability in processing security data, making it a standout choice for enterprise security teams.
Google Chronicle was designed to address the multifaceted challenges that Chief Information Security Officers (CISOs), Chief Information Officers (CIOs), and Security Operations Center (SOC) managers face daily. These challenges range from managing vast volumes of security data to ensuring timely threat detection and response. Chronicle’s cloud-native architecture allows organizations to retain, analyze, and search massive amounts of security and network telemetry data with ease, providing insights that were previously unattainable due to technological and financial constraints.
One of the core strengths of Google Chronicle is its ability to integrate deep security analytics with comprehensive threat intelligence. This integration empowers security teams to detect and respond to threats more rapidly and accurately than ever before. The platform’s efficiency in handling and analyzing data not only boosts the productivity of security analysts but also significantly reduces the time to remediate potential threats.
Moreover, Chronicle’s pricing model, which does not rely on data volume, provides organizations with predictable costs and the flexibility to scale their security operations without worrying about escalating expenses. This aspect is particularly crucial for enterprises that are expanding their digital footprints and require a SIEM system that can grow with their increasing security needs.
In summary, Google Chronicle stands at the forefront of the next generation of cybersecurity tools, providing robust, scalable, and cost-effective solutions that enhance the overall security posture of organizations. As we delve deeper into its features and capabilities, it becomes clear why more and more enterprises are turning to Chronicle to safeguard their digital environments.
Core Features of Google Chronicle: A Deep Dive
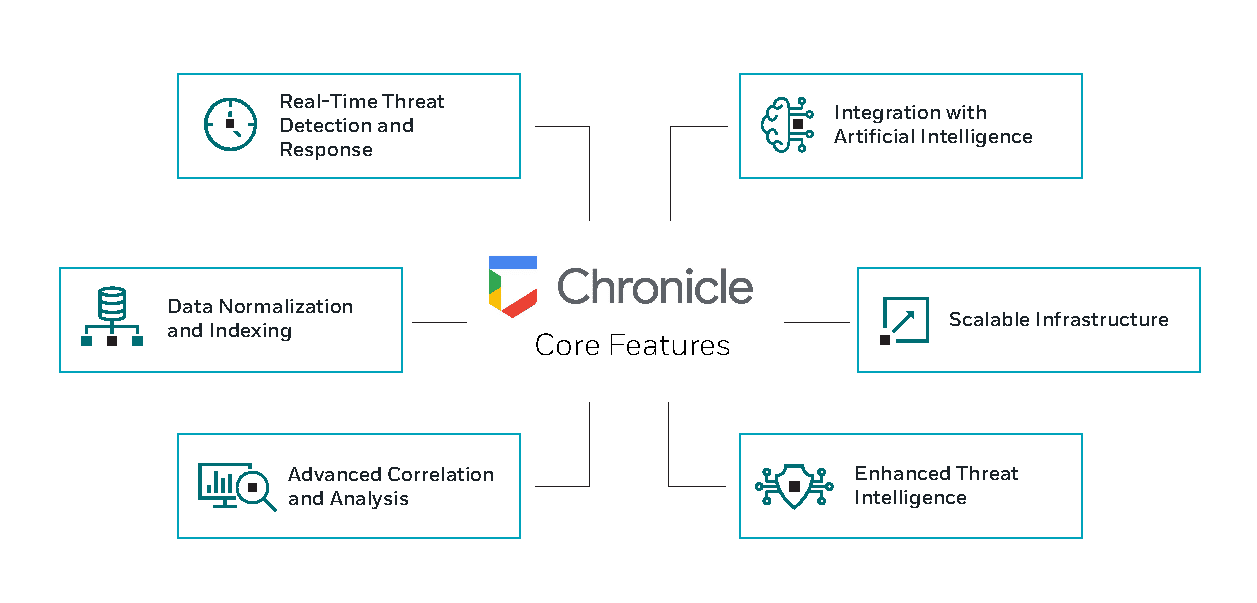
Google Chronicle sets itself apart in the cybersecurity landscape through a suite of advanced features that cater to the complex needs of modern security operations. At its core, Chronicle is built to enhance the efficiency and effectiveness of security information and event management (SIEM) systems. Let’s explore the key features that make Google Chronicle a leader in the SIEM market:
Real-Time Threat Detection and Response
One of the hallmark capabilities of Google Chronicle is its real-time threat detection. Utilizing Google’s vast infrastructure, Chronicle processes and analyzes security data at unprecedented speeds. This allows security teams to detect malicious activities as they happen, significantly reducing the attacker’s dwell time and the potential damage they can inflict.
Data Normalization and Indexing
Chronicle excels in handling diverse data types from various sources. It normalizes and indexes vast amounts of security telemetry, including logs from endpoints, networks, and cloud services. This normalization ensures that data is consistently formatted, making it easier for security systems to analyze and extract meaningful insights.
Advanced Correlation and Analysis
Through its sophisticated algorithms, Chronicle correlates events across different data sources to identify patterns that may indicate a security threat. This capability is enhanced by machine learning models that learn from a broad range of inputs, improving their accuracy over time in detecting complex, multi-stage attacks.
Integration with Artificial Intelligence
Artificial intelligence (AI) plays a pivotal role in Chronicle’s operations, particularly in automating threat detection and response processes. AI helps in sifting through false positives, thereby allowing analysts to focus on genuine threats. This integration not only speeds up the response times but also enhances the precision of threat detection strategies.
Scalable Infrastructure
Built on Google Cloud, Chronicle offers a scalable SIEM solution that can handle petabytes of data without performance degradation. This scalability is crucial for large enterprises that generate enormous volumes of logs and network telemetry, providing them with the ability to maintain and analyze historical data over extended periods.
Enhanced Threat Intelligence
Chronicle leverages Google’s vast threat intelligence network to provide up-to-date and comprehensive threat data. This information is continuously integrated into the system, allowing Chronicle to offer proactive security measures by identifying and responding to new threats as they emerge.
The combination of these features makes Google Chronicle not just a tool but a comprehensive platform that enhances the operational capabilities of security teams. By providing detailed, real-time insights into security events and automating critical processes, Chronicle significantly boosts the productivity and effectiveness of SOC environments. This deep dive into its core functionalities reveals why Chronicle is not only a leader but also a revolutionary force in the field of cybersecurity.
Core Features of Google Chronicle
Comparing Google Chronicle to Other SIEM Tools
In the competitive landscape of security information and event management (SIEM) tools, Google Chronicle stands out due to its innovative features and integration capabilities. To better understand how Chronicle measures against its peers, we compare it with other leading SIEM solutions such as Splunk (Cisco’s SIEM platform), and Microsoft Sentinel. This comparative analysis highlights the distinctive advantages and capabilities of each platform, providing CISOs, CIOs, and SOC managers with critical insights to make informed decisions.
| Feature | Google Chronicle | Splunk (acquired by Cisco) | Microsoft Sentinel |
| Data Management | Petabyte-scale, no per-volume pricing | Data indexed by volume, high cost | Scalable but may incur high costs |
| Real-Time Analytics | Sub-second response times | Fast but dependent on data size | Near real-time, depends on setup |
| Threat Intelligence | Integrated with Google’s global database | Extensive marketplace integrations | Native integration with Azure services |
| AI and Machine Learning | Advanced machine learning capabilities | Strong AI capabilities | Integrated AI from Azure |
| User Interface | Intuitive, user-friendly | Complex, steep learning curve | User-friendly, integrated with other Microsoft products |
| Cost Effectiveness | Predictable pricing, no data volume charge | High operational costs | Cost-effective for Azure users |
| Customization | High flexibility and customization | Highly customizable | Moderate customization options |
| Integration Capabilities | Extensive API access, easy integration | Wide range of integrations | Seamless integration within Azure ecosystem |
Comparative Analysis of Google Chronicle to Other SIEMs
Google Chronicle excels in handling large volumes of data with its innovative pricing model that does not charge based on data volume. This feature alone makes it particularly attractive for large organizations that generate vast amounts of telemetry data. Moreover, its integration with Google’s threat intelligence and advanced AI capabilities provides a robust platform for proactive threat detection and response.
Splunk (Cisco SIEM) is known for its powerful analytics and extensive integration capabilities through its marketplace. However, its cost can be prohibitively high, especially for organizations that need to scale their data ingestion significantly.
Microsoft Sentinel offers excellent integration within the Azure ecosystem, making it a preferred choice for enterprises heavily invested in Microsoft products. Its AI capabilities, powered by Azure, provide strong analytics, although sometimes at an additional cost.
Conclusion
Choosing the right SIEM tool depends on specific organizational needs, existing infrastructure, and budget constraints. Google Chronicle’s unique selling points—scalability without additional cost, superior threat intelligence, and rapid analytics—make it a compelling option for organizations looking to enhance their cybersecurity posture efficiently and cost-effectively. This comparison underscores Chronicle’s position as a frontrunner in the SIEM tool landscape, particularly for enterprises seeking to leverage high volumes of data and advanced threat intelligence capabilities.
Integration of Chronicle with Siemplify and Other Platforms
Integrating Google Chronicle with Siemplify and other platforms significantly enhances the capabilities of security operations centers (SOCs) by streamlining workflows and automating responses. This section provides a step-by-step guide on how Chronicle’s integration with Siemplify benefits SOCs and explores the integration with other key platforms.
Integrating Google Chronicle with Siemplify
Siemplify, known for its SOAR (Security Orchestration, Automation, and Response) capabilities, complements Google Chronicle’s SIEM features by providing an environment where security teams can manage and automate their security operations effectively. Here’s how you can integrate these two powerful tools:
- Service Account Setup: Obtain the service account details from your Chronicle provider. These are crucial for the integration as they allow Siemplify to interact securely with Chronicle’s data.
- Marketplace Installation:
- Navigate to the Siemplify Marketplace.
- Search for the Google Chronicle integration.
- Install the integration by following the on-screen instructions.
- Configure the Integration:
- In Siemplify, go to Settings -> Integrations.
- Select the Chronicle integration and enter the service account details.
- Configure the API root settings as per your Chronicle environment.
- Test the Integration:
- Use the test functionality in Siemplify to ensure the integration is set up correctly.
- Check for the green check mark indicating a successful connection.
- Operational Deployment:
- Begin using the integrated tools for enhanced threat detection and response.
- Utilize Siemplify’s automated playbooks to respond to alerts generated by Chronicle.
Key Benefits of Integrating Chronicle with Siemplify
- Automated Response: Automate responses to alerts using Siemplify’s playbooks, reducing the time from detection to resolution.
- Enhanced Case Management: Streamline case management processes by integrating Chronicle’s data insights with Siemplify’s case management tools.
- Increased Operational Efficiency: Reduce manual tasks and focus on strategic decision-making by leveraging automation and integration.
Integration with Other Platforms
Google Chronicle’s API-first design facilitates its integration with a wide array of other platforms and tools, enhancing its versatility. Here are a few notable integrations:
- Threat Intelligence Platforms: Chronicle can ingest threat intelligence from multiple sources, enhancing its native intelligence capabilities.
- Cloud Services: Integration with cloud platforms like AWS and Azure improves visibility across cloud infrastructures.
- Endpoint Protection Tools: Chronicle integrates seamlessly with endpoint protection platforms to provide comprehensive visibility into endpoint security.
Step-by-Step Guide for Broader Integrations
- Identify Integration Needs: Determine which platforms and tools need to be integrated with Chronicle based on your security requirements.
- API Configuration: Use Chronicle’s APIs to set up integrations with these platforms, ensuring secure data sharing and actions.
- Customization and Testing: Customize the integrations to fit your operational workflows and test thoroughly to ensure reliability.
- Deployment and Monitoring: Deploy the integrated solution across your environment and continuously monitor for effectiveness and improvements.
Conclusion
Integrating Google Chronicle with Siemplify and other essential security platforms empowers SOCs to leverage advanced automation, enhance their threat response capabilities, and streamline security operations. By following these integration steps, organizations can maximize their investment in Chronicle and build a more resilient and responsive security infrastructure.
Real-World Applications of Google Chronicle
Google Chronicle’s deployment in various industries highlights its versatility and effectiveness in addressing complex cybersecurity challenges. This section explores the real-world applications of Google Chronicle, focusing on how its features are utilized across different sectors to enhance security operations and threat response capabilities.
Financial Services
In the financial sector, security is paramount due to the sensitive nature of the data involved and the high risk of cyber-attacks. Google Chronicle is employed to monitor and analyze vast amounts of transaction data in real time. Its ability to detect anomalies and potential threats swiftly allows financial institutions to preemptively address risks before they escalate into breaches. Additionally, Chronicle’s scalable infrastructure supports the rapid growth of data volumes in finance, ensuring comprehensive coverage without performance trade-offs.
Healthcare
Healthcare organizations use Google Chronicle to protect patient data and ensure compliance with strict regulatory requirements like HIPAA. By integrating Chronicle with their existing health information systems, these organizations can enhance their monitoring capabilities, quickly identifying and responding to potential data breaches. Chronicle’s efficient data normalization and indexing make it easier for healthcare providers to manage diverse data types, from patient records to connected medical devices.
Retail and E-Commerce
Retailers and e-commerce platforms leverage Google Chronicle to secure their online transactions and customer data. Chronicle’s real-time threat detection is crucial for identifying fraudulent activities and preventing data breaches that could lead to significant financial losses and damage to reputation. Moreover, its integration capabilities allow retailers to combine security data from various sources, including online platforms, physical stores, and supply chain operations, creating a unified security posture.
Manufacturing
In manufacturing, the integration of IoT devices into production processes has increased the attack surface. Google Chronicle helps manufacturers monitor these devices and the data they generate. By analyzing network traffic and device behavior, Chronicle can spot potential vulnerabilities and unauthorized access, ensuring that production lines are not disrupted by cyber threats.
Government
Government agencies use Google Chronicle to protect critical infrastructure and sensitive data against sophisticated cyber threats. Chronicle’s comprehensive threat intelligence capabilities are particularly valuable, enabling agencies to stay ahead of potential threats from nation-state actors and cybercriminals. Furthermore, Chronicle’s ability to handle high-volume data ensures that large-scale public sector networks remain secure and resilient.
Education
Educational institutions are increasingly targeted by cyber-attacks, particularly ransomware. Google Chronicle aids these institutions by monitoring network activities and quickly identifying malware or unauthorized access attempts. Its cost-effective data management is crucial for educational organizations, often operating under tight budget constraints, allowing them to maintain robust cybersecurity measures.
Conclusion
Google Chronicle’s application across diverse industries demonstrates its adaptability and effectiveness in addressing a wide range of cybersecurity challenges. By harnessing Chronicle’s advanced SIEM and SOAR capabilities, organizations across sectors can enhance their ability to detect, analyze, and respond to threats swiftly, thereby safeguarding their critical assets and data. This broad applicability underscores Chronicle’s role as a transformative tool in the realm of cybersecurity, capable of meeting the unique needs of various sectors.
Future Trends in SIEM: The Role of Google Chronicle
The landscape of cybersecurity is constantly evolving, and with it, the tools and technologies used to protect digital assets and infrastructures must also adapt. Security Information and Event Management (SIEM) systems like Google Chronicle are at the forefront of this evolution, driving significant changes in how security operations are conducted. This section explores the future trends in SIEM and the integral role Google Chronicle is poised to play in shaping these advancements.
Cloud-Native SIEM Solutions
As organizations continue to migrate their operations to the cloud, the demand for cloud-native SIEM solutions grows. Google Chronicle, built on Google’s secure cloud infrastructure, exemplifies the shift towards cloud-native security systems that offer scalability, flexibility, and integrated threat intelligence. Future SIEM solutions will likely emphasize seamless integration with cloud services, multi-cloud environments, and hybrid setups, areas where Chronicle already excels.
Integration of AI and Machine Learning
The integration of artificial intelligence (AI) and machine learning (ML) into SIEM systems is transforming the landscape of threat detection and response. Google Chronicle leverages AI to enhance its analytics capabilities, enabling it to detect complex threats more quickly and reduce false positives significantly. As AI and ML technologies advance, their incorporation into SIEM systems like Chronicle will become more sophisticated, leading to even more efficient and autonomous security operations.
Increased Emphasis on Proactive Threat Hunting
Proactive threat hunting is becoming a critical component of SIEM capabilities. Google Chronicle supports this trend by providing tools that allow security teams to actively search for potential threats before they manifest into attacks. The future of SIEM involves not just responding to alerts but using predictive analytics to anticipate threats and mitigate them proactively.
Greater Focus on Regulatory Compliance
With increasing regulatory demands across various industries, future SIEM systems will need to offer enhanced capabilities to help organizations comply with legal and regulatory standards. Google Chronicle facilitates this by providing comprehensive data coverage and retention capabilities that aid in meeting compliance requirements such as GDPR, HIPAA, and more. As regulations continue to evolve, SIEM tools will need to adapt quickly to keep pace with new compliance needs.
Automation and Orchestration
The future of SIEM will see a greater emphasis on automation and orchestration, aspects where Google Chronicle is set to lead. By automating routine tasks and orchestrating complex workflows, Chronicle reduces the workload on security teams, allowing them to focus on more strategic tasks. This trend is likely to continue as organizations seek to streamline their security operations further and improve response times.
User and Entity Behavior Analytics (UEBA)
User and Entity Behavior Analytics (UEBA) will play an increasingly significant role in SIEM solutions. Google Chronicle integrates UEBA to provide a deeper understanding of user behavior and detect anomalies that could indicate potential security incidents. As cyber threats become more sophisticated, incorporating UEBA into SIEM systems will be crucial for detecting insider threats and advanced persistent threats (APTs).
Conclusion
The future of SIEM is dynamic and promising, with Google Chronicle leading the way in several key areas. As organizations adapt to an ever-changing threat landscape, the capabilities provided by Chronicle—such as cloud-native operations, advanced AI analytics, and proactive threat hunting—will become indispensable. The ongoing evolution of Chronicle and its role in these future trends will continue to set benchmarks for what effective, modern-day SIEM solutions should offer, making it a cornerstone in the next generation of cybersecurity defenses.
Practical Guide: Implementing Chronicle in Your SOC
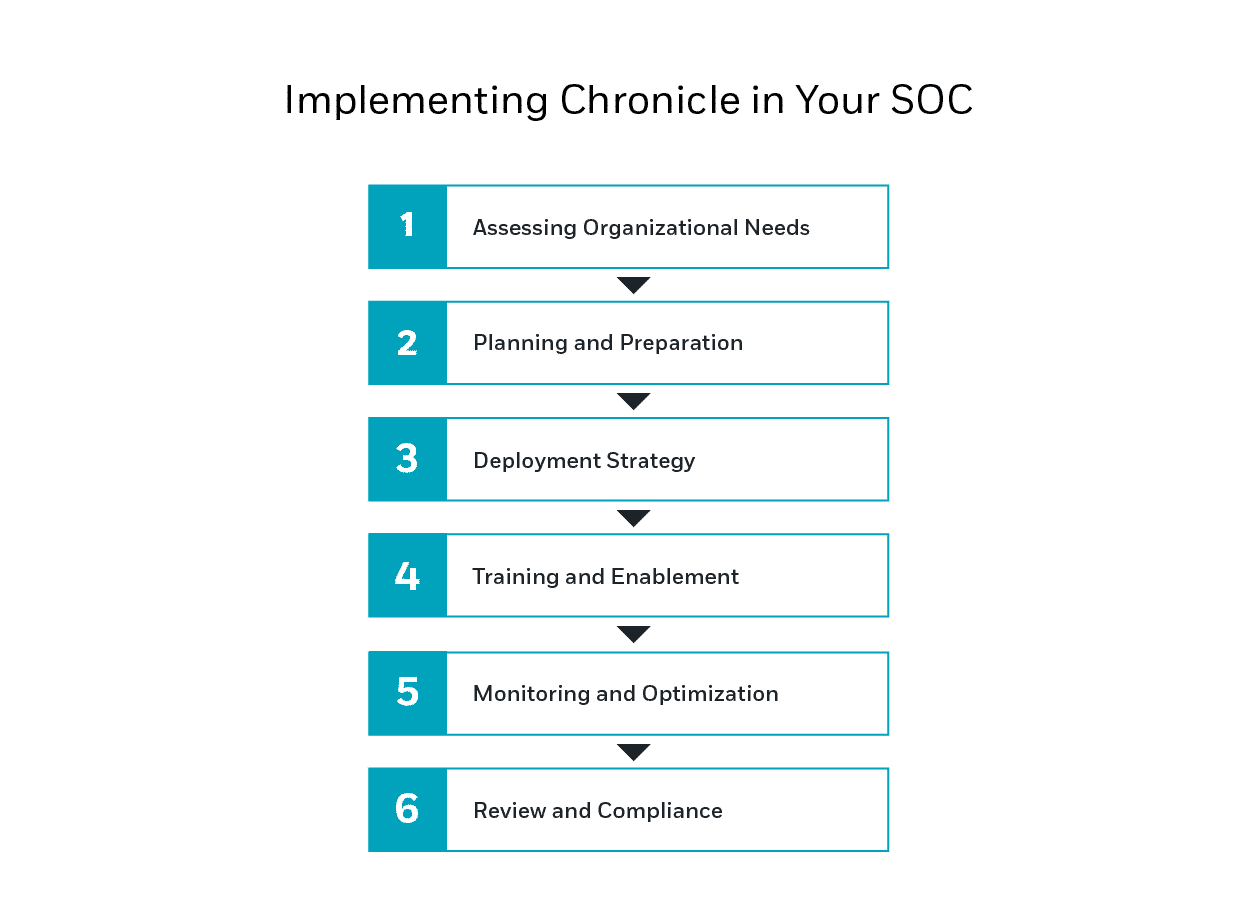
Implementing Google Chronicle in your Security Operations Center (SOC) represents a strategic move towards enhancing cybersecurity defenses and operational efficiency. This section provides a concise guide on best practices and key considerations for deploying Google Chronicle effectively within your organization’s SOC.
Assessing Organizational Needs
Before integrating Google Chronicle, it’s crucial to assess your organization’s specific security needs, which can be conducted by means of a vulnerability assessment. Evaluate the current security infrastructure, identify gaps, and determine how Chronicle can address these deficiencies. Consider factors such as existing SIEM tools, the volume of data processed, and specific security challenges like compliance requirements or advanced persistent threats.
Planning and Preparation
- Infrastructure Readiness: Ensure that your infrastructure is capable of integrating with a cloud-native SIEM solution like Chronicle. This includes checking network configurations, data storage capabilities, and ensuring compatibility with existing tools.
- Stakeholder Engagement: Involve all relevant stakeholders from the beginning. This includes IT staff, security analysts, compliance officers, and executive management. Their input will be valuable in aligning the deployment with business and security objectives.
Deployment Strategy
- Phased Rollout: Consider a phased approach to deploying Chronicle. Start with a pilot program covering critical areas to monitor its performance and impact. Gradually expand the deployment to other areas based on the results and learned experiences.
- Integration with Existing Tools: Chronicle should complement and enhance your current security setup. Plan the integration points carefully to ensure seamless data flow and functionality between Chronicle and other security tools.
Training and Enablement
- Technical Training: Provide comprehensive training for your security analysts and IT team to ensure they are proficient in using Chronicle. Focus on features specific to your security operations, such as threat analysis, alert management, and response procedures.
- Ongoing Learning: Cybersecurity is a rapidly evolving field. Encourage continuous learning and certification opportunities for team members to keep pace with new Chronicle features and broader cybersecurity trends.
Monitoring and Optimization
- Performance Monitoring: Regularly monitor the performance of Chronicle within your SOC. Look for improvements in threat detection rates, response times, and analyst productivity.
- Feedback Loop: Establish a feedback mechanism to gather insights from users and adjust configurations. Continuous improvement will help in optimizing the performance and effectiveness of Chronicle in your security operations.
Review and Compliance
- Regular Reviews: Conduct regular reviews to assess the effectiveness of Chronicle in meeting your security needs. This includes analyzing the ROI, compliance with regulatory requirements, and the overall impact on your SOC’s operational efficiency.
- Compliance Audits: Ensure that Chronicle’s deployment aligns with all relevant compliance standards. Utilize Chronicle’s data logging and reporting features to simplify compliance audits and reporting.
Implementing Chronicle in Your SOC
Conclusion
Implementing Google Chronicle in your SOC can significantly enhance your cybersecurity posture and operational efficiency. By following this practical guide, your organization can ensure a smooth transition to a more advanced and integrated SIEM solution. As Chronicle continues to evolve, staying updated and adapting to its new features will further strengthen your security operations against an increasingly complex threat landscape.










