Organizations face a constant barrage of cyber threats, ranging from sophisticated attacks by organized criminal groups to targeted campaigns by nation-states. To effectively safeguard their critical assets and protect their reputation, organizations must adopt a proactive and comprehensive approach to cybersecurity. Continuous Threat Exposure Management (CTEM) emerges as a crucial solution, providing a framework for organizations to continuously monitor their IT environment, identify potential vulnerabilities, and mitigate risks before they can be exploited. By embracing CTEM, organizations can gain a competitive edge, enhance their security posture, and protect their business from the ever-present threat of cyberattacks.
What is Continuous Threat Exposure Management?
Continuous Threat Exposure Management (CTEM) is a proactive security framework designed to provide organizations with a comprehensive view of their potential vulnerabilities and risks. Unlike traditional security measures that focus on reactive incident response, CTEM empowers organizations to anticipate and mitigate threats before they can materialize.
At the core of CTEM lies the ability to continuously monitor an organization’s IT environment for vulnerabilities, identify potential attack paths, and assess the potential impact of a successful breach. By proactively addressing these threats, CTEM helps organizations safeguard their critical assets and reduce the likelihood of costly cyberattacks.
Why is Continuous Threat Exposure Management Crucial in Today’s Threat Landscape?
The modern cyber threat landscape is characterized by its constant evolution, with new attack vectors and techniques emerging rapidly. This makes it increasingly challenging for security teams to keep pace with the latest threats and ensure their organization’s protection.
CTEM plays a vital role in addressing these challenges by providing organizations with a proactive defense mechanism. By continuously monitoring for vulnerabilities and identifying potential attack paths, CTEM enables security teams to stay ahead of the curve and mitigate risks before they can be exploited. Additionally, CTEM helps organizations prioritize their security efforts, focusing on the most critical vulnerabilities and threats to their business.
Key Benefits of Implementing a Continuous Threat Exposure Management Approach
Implementing a CTEM approach offers numerous benefits for organizations, including:
- Improved threat visibility: CTEM provides organizations with a comprehensive view of their potential vulnerabilities and risks, enabling them to identify and address threats before they can be exploited.
- Reduced risk of breaches: By proactively addressing vulnerabilities and mitigating threats, CTEM helps organizations reduce the likelihood of successful cyberattacks and minimize the potential impact of breaches.
- Efficient resource allocation: CTEM enables organizations to prioritize their security efforts, focusing on the most critical vulnerabilities and threats to their business. This helps ensure that security resources are allocated effectively and efficiently.
- Enhanced incident response: CTEM can also aid in incident response by providing organizations with a better understanding of the potential impact of a breach and the steps necessary to contain and mitigate it.

The Continuous Threat Exposure Management Process: A Five-Stage Framework
A typical CTEM program involves five key stages:
- Scoping: This stage involves defining the scope of the CTEM program, including identifying critical assets, defining the boundaries of the assessment, and establishing key performance indicators (KPIs).
- Discovery: During the discovery stage, organizations collect data on their IT infrastructure, applications, and systems. This data is used to identify potential vulnerabilities and risks.
- Prioritization: Once vulnerabilities and risks have been identified, they are prioritized based on factors such as severity, likelihood of exploitation, and potential impact on the business.
- Validation: In the validation stage, identified vulnerabilities are verified through techniques like penetration testing and vulnerability scanning.
- Mobilization: The final stage involves implementing remediation measures to address identified vulnerabilities and risks. This may include patching systems, updating software, and implementing security controls.
By following this five-stage framework, organizations can effectively implement a CTEM program and continuously improve their security posture.
Continuous Threat Exposure Management vs. External Attack Surface Management (EASM): Understanding the Differences
While CTEM and External Attack Surface Management (EASM) are both focused on identifying and mitigating security risks, they have distinct approaches and scopes.
EASM specifically focuses on the external attack surface of an organization, identifying and assessing vulnerabilities that are exposed to external attackers. This includes vulnerabilities in websites, web applications, and other publicly accessible systems.
CTEM, on the other hand, takes a broader approach, encompassing the entire organization’s IT infrastructure and identifying potential attack paths both internally and externally. CTEM also considers the potential impact of vulnerabilities on critical assets and business operations.
In essence, EASM is a subset of CTEM, focusing on a specific aspect of the organization’s external attack surface. CTEM provides a more comprehensive view of an organization’s overall security posture.
Implementing a Continuous Threat Exposure Management Program: Tools and Strategies
Implementing a CTEM program requires a combination of tools and strategies. Some key components include:
- Continuous monitoring: Organizations should implement continuous monitoring solutions to identify and track vulnerabilities and threats in real-time.
- Penetration testing: Regular penetration testing can help identify vulnerabilities that may have been missed by other security measures.
- Threat intelligence feeds: By subscribing to threat intelligence feeds, organizations can stay informed about emerging threats and trends.
- Integration with existing security tools: CTEM can be integrated with existing security tools, such as Security Operations Centers (SOCs) and Security Information and Event Management (SIEM) systems, to provide a more comprehensive view of an organization’s security posture.
By leveraging these tools and strategies, organizations can effectively implement a CTEM program and enhance their cybersecurity capabilities.
The SOC’s Pivotal Role in Continuous Threat Exposure Management (CTEM)
The Security Operations Center (SOC) serves as the nerve center of an organization’s cybersecurity defense, playing a critical role in implementing and managing Continuous Threat Exposure Management (CTEM) programs. By leveraging the SOC’s expertise, organizations can effectively monitor their IT environment, detect potential threats, and respond swiftly to incidents.
Key Roles of the SOC in CTEM
- Threat Detection and Monitoring
- The SOC utilizes advanced security tools and techniques to continuously monitor the organization’s network, systems, and applications for signs of malicious activity.
- By analyzing logs, network traffic, and other data, the SOC can identify potential threats such as unauthorized access, malware infections, and data breaches.
- Incident Response and Management:
- When a security incident occurs, the SOC is responsible for coordinating the response efforts and containing the damage.
- They may need to isolate affected systems, investigate the root cause of the incident, and implement remediation measures.
- Vulnerability Management:
- The SOC plays a crucial role in identifying and prioritizing vulnerabilities within the organization’s IT infrastructure.
- They can work with other teams to patch vulnerabilities, implement security controls, and reduce the risk of exploitation.
- Threat Intelligence Analysis:
- The SOC can leverage threat intelligence feeds to stay informed about emerging threats and trends.
- By analyzing threat intelligence data, the SOC can identify potential risks to the organization and take proactive measures to mitigate them.
- Integration with CTEM Tools:
- The SOC is responsible for integrating CTEM tools and technologies into the organization’s security infrastructure.
- This ensures that the SOC has access to the necessary data and tools to effectively monitor for threats and respond to incidents.
Challenges and Best Practices
- Overburdened SOC Teams: SOC teams often face the challenge of being overwhelmed by the volume of alerts and incidents. Implementing effective prioritization and automation techniques can help alleviate this burden.
- Skills Gap: Ensuring that SOC personnel have the necessary skills and expertise to effectively manage CTEM programs is crucial. Investing in training and development can help address this challenge.
- Integration with Existing Tools: Integrating CTEM tools with existing security infrastructure can be complex. Careful planning and coordination are essential to ensure a smooth integration process.
By effectively leveraging the SOC’s capabilities, organizations can strengthen their CTEM programs and enhance their overall cybersecurity posture. The SOC’s expertise in threat detection, incident response, and vulnerability management is essential for protecting against the ever-evolving cyber threat landscape.
The CISO’s Role in Adopting a Continuous Threat Exposure Management (CTEM) Program
The Chief Information Security Officer (CISO) plays a pivotal role in driving the adoption of a CTEM program within an organization. Their responsibilities include:
- Championing CTEM: The CISO must advocate for the importance of CTEM as a strategic security initiative, convincing executive leadership and other stakeholders of its benefits.
- Defining the Scope: The CISO helps define the scope of the CTEM program, identifying critical assets, defining the boundaries of the assessment, and establishing key performance indicators (KPIs).
- Allocating Resources: The CISO is responsible for securing the necessary resources, including budget, personnel, and technology, to support the implementation and ongoing operation of the CTEM program.
- Overseeing Implementation: The CISO oversees the implementation of the CTEM program, ensuring that it aligns with the organization’s overall security strategy and meets regulatory requirements.
- Monitoring and Evaluation: The CISO is responsible for monitoring the effectiveness of the CTEM program and evaluating its performance against established KPIs. They may also need to make adjustments to the program as needed to address evolving threats and risks.
- Building a Security Culture: The CISO plays a crucial role in fostering a security-conscious culture within the organization, encouraging employees to be aware of and report potential security threats.
By actively driving the adoption and implementation of a CTEM program, the CISO can help organizations proactively identify and mitigate risks, improve their security posture, and protect their critical assets.
Getting Buy-In from Senior Management for a Continuous Threat Exposure Management (CTEM) Program
Gaining buy-in from senior management is crucial for the successful implementation of a CTEM program. Here are some strategies to help you secure their support:
Highlight the Business Value
- Quantify the risks: Demonstrate the potential financial and reputational damage that a cyberattack could cause to the organization.
- Showcase the benefits: Emphasize how CTEM can improve operational efficiency, reduce downtime, and enhance customer trust.
- Present a strong ROI: Develop a cost-benefit analysis that highlights the potential savings from preventing breaches and reducing the costs associated with incident response.
Align with Strategic Objectives
- Connect CTEM to business goals: Explain how CTEM aligns with the organization’s overall strategic objectives, such as improving customer satisfaction, enhancing operational efficiency, or mitigating regulatory risks.
- Demonstrate how CTEM supports business continuity: Highlight how CTEM can help ensure business continuity by identifying and addressing potential threats before they can disrupt operations.
Showcase the Competitive Advantage
- Position CTEM as a differentiator: Explain how implementing CTEM can give the organization a competitive advantage by demonstrating a strong commitment to security and risk management.
- Highlight the benefits to customers: Emphasize how a robust CTEM program can improve customer confidence and loyalty.
Provide a Clear Roadmap
- Develop a comprehensive plan: Create a detailed roadmap outlining the goals, objectives, and timeline for implementing the CTEM program.
- Address concerns and questions: Be prepared to address any concerns or questions from senior management, providing clear and concise answers.
Engage with Key Stakeholders
- Involve relevant departments: Collaborate with key stakeholders from departments such as IT, finance, legal, and risk management to build consensus and support for the CTEM program.
- Address concerns and needs: Understand the specific concerns and needs of each stakeholder and tailor your messaging accordingly.
Leverage External Validation
- Cite industry best practices: Refer to industry standards and best practices to demonstrate the importance of CTEM.
- Highlight case studies: Share success stories of other organizations that have benefited from implementing CTEM programs.
By following these strategies, you can increase the likelihood of securing buy-in from senior management for your CTEM program and pave the way for its successful implementation.
Budgeting for Continuous Threat Exposure Management (CTEM)
Allocating sufficient budget for Continuous Threat Exposure Management (CTEM) is essential for ensuring the long-term success of your organization’s cybersecurity program. However, determining the exact budget requirements can be challenging, as it depends on various factors such as the size of your organization, the complexity of your IT infrastructure, and the specific CTEM tools and services you choose to implement.
Key Factors Influencing CTEM Budget
- Organization Size and Complexity: Larger organizations with more complex IT environments will typically require a higher budget for CTEM.
- Scope of CTEM Program: The scope of your CTEM program, including the number of assets to be monitored and the level of risk assessment required, will also impact the budget.
- CTEM Tools and Technologies: The cost of CTEM tools and technologies can vary widely depending on the features and capabilities they offer.
- In-House vs. Outsourced Resources: The decision to manage CTEM internally or outsource to a managed security service provider (MSSP) will affect the budget.
- Regulatory Requirements: Compliance with industry-specific regulations may necessitate additional investments in CTEM.
Budget Allocation Considerations
- Initial Investment: Implementing a CTEM program often requires a significant upfront investment to purchase necessary tools, hire staff, and conduct initial assessments.
- Ongoing Costs: Once the program is established, ongoing costs will include software licenses, maintenance, and personnel expenses.
- Return on Investment (ROI): Consider the potential ROI of CTEM, such as reduced risk of data breaches, improved operational efficiency, and enhanced customer confidence.
- Scalability: Ensure that your CTEM budget is scalable to accommodate future growth and changes in your organization’s IT environment.
Budget Allocation Strategies
- Prioritize Critical Assets: Focus on protecting your most critical assets and allocate resources accordingly.
- Phase Implementation: Consider a phased approach to CTEM implementation, starting with essential components and gradually expanding the program over time.
- Leverage Cloud-Based Solutions: Cloud-based CTEM tools can often be more cost-effective than on-premises solutions.
- Outsourcing vs. In-House: Evaluate the costs and benefits of outsourcing CTEM services to an MSSP/MDR company compared to building an in-house team.
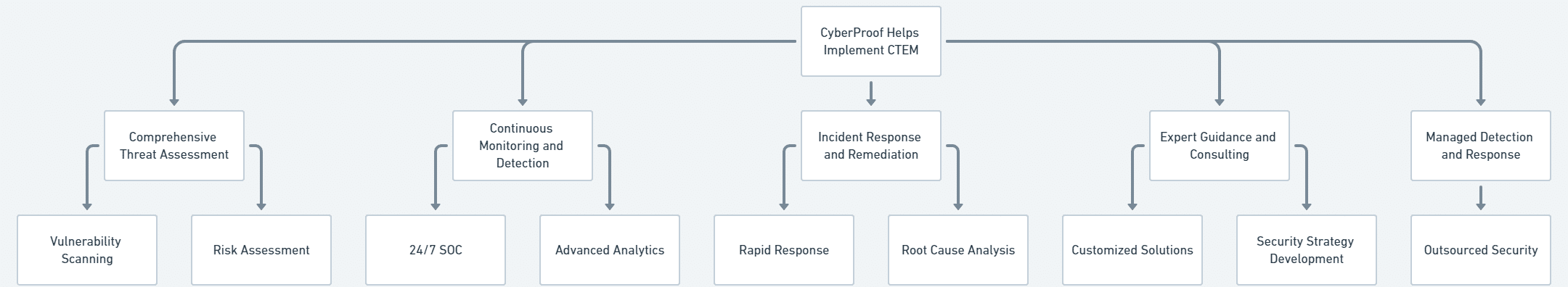
CyberProof Helps Your Company Adopt Continuous Threat Exposure Management (CTEM)
CyberProof offers valuable assistance in implementing and maintaining a Continuous Threat Exposure Management (CTEM) program for your company. As a leading provider of managed security services, CyberProof specializes in helping organizations proactively identify, assess, and mitigate cybersecurity risks.
Here’s how CyberProof can support your CTEM efforts:
Comprehensive Threat Assessment
- Vulnerability Scanning: CyberProof can conduct thorough vulnerability assessments to identify potential weaknesses in your systems and applications.
- Risk Assessment: They can evaluate the potential impact of these vulnerabilities and prioritize them based on risk level.
Continuous Monitoring and Detection
- 24/7 Security Operations Center (SOC): CyberProof’s SOC can monitor your network for suspicious activity and potential threats in real-time.
- Advanced Analytics: They use advanced analytics and threat intelligence to detect and respond to emerging threats.
Incident Response and Remediation
- Rapid Response: In the event of a security incident, CyberProof’s team can respond quickly to contain the damage and restore normal operations.
- Root Cause Analysis: They can conduct a thorough investigation to determine the root cause of the incident and implement preventive measures.
Expert Guidance and Consulting
- Customized Solutions: CyberProof can tailor their services to meet your specific needs and provide expert guidance on best practices for CTEM.
- Security Strategy Development: They can help you develop a comprehensive security strategy that aligns with your business objectives.
Managed Detection and Response (MDR)
- Outsourced Security: CyberProof’s MDR service can provide a fully managed security solution, freeing up your internal resources to focus on other priorities.
By partnering with CyberProof, you can benefit from their expertise and experience in implementing a robust CTEM program, helping to protect your organization from cyber threats and ensure business continuity.
Conclusion: Staying Ahead of the Curve with Continuous Threat Exposure Management
In today’s dynamic threat landscape, organizations must adopt a proactive approach to security to protect their critical assets and mitigate the risk of cyberattacks. Continuous Threat Exposure Management (CTEM) provides a valuable framework for achieving this goal by enabling organizations to identify, prioritize, and address vulnerabilities before they can be exploited.
By implementing a CTEM program, organizations can enhance their overall cybersecurity posture, reduce the likelihood of breaches, and protect their reputation and bottom line. CTEM is essential for organizations of all sizes and industries that want to stay ahead of the curve and safeguard their digital assets.












