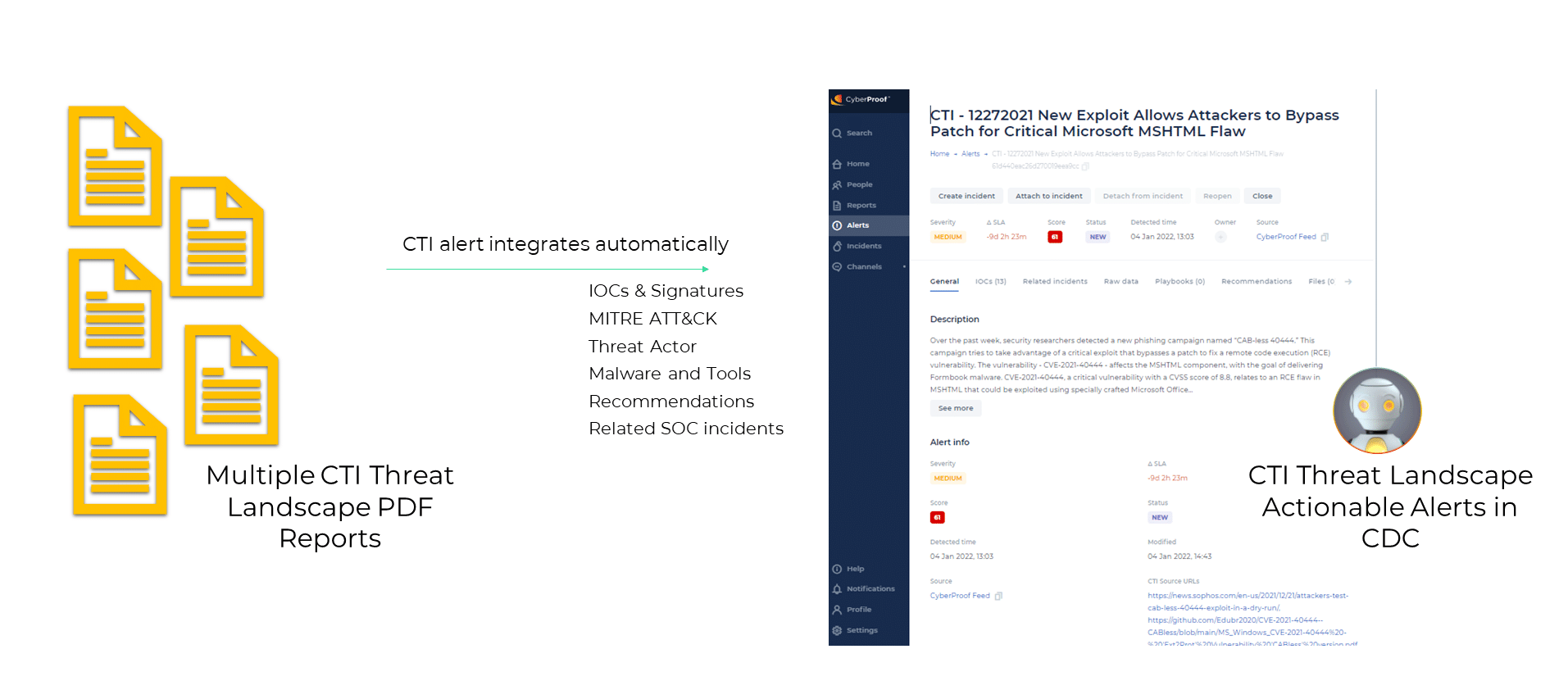
Security Operations Center (SOC) teams typically rely on manual processes to obtain the cyber threat intelligence (CTI) information they need. Analysts read CTI reports, sent at weekly or monthly intervals in PDF format so the analysts are always catching up – receiving information gleaned days or weeks previously.
SOC teams also search for information online – then paste the most relevant data into a SOC portal or share it with the rest of the team by email. Some teams rely on information they receive from threat intelligence platforms (TIPs), which provide an ongoing stream of alerts that creates many false positives. All this means there’s a delay in conveying updated CTI information. It creates extra work for analysts, increasing the daily load and leaving room for human error.
For teams struggling to keep up with the ongoing responsibilities of the SOC, reading periodic CTI reports or sorting through false positives to identify relevant CTI data requires a huge time investment – and because time is short, the process probably isn’t handled consistently. This problem can be eliminated entirely by integrating and automating threat intelligence – ingesting CTI updates into a common orchestration platform so that they are viewed together with other perimeter alerts.
Let’s have a look at some of the many ways CTI integration & automation not only lightens the workload for SOC teams but also contributes to faster incident detection & response.
1. Providing Enrichment
Automating CTI notification in a common orchestration platform eliminates delay and the possibility for human error – and facilitates sharing context and actionable recommendations.
Automating CTI notification in a common orchestration platform not only eliminates delay and the possibility for human error – it also facilitates sharing additional context and actionable recommendations with the SOC team.
At CyberProof, for example, the CTI alerts ingested into the automation and orchestration platform are enriched by a virtual bot we call SeeMo. SeeMo enriches each alert with additional information, including:
- Observables
- Indicators of Compromise (IOCs)
- Tactics, Techniques and Procedures (TTPs)
- Associated threat actor
- Related incidents
- Specific detection rules
- Suggestions regarding how to change company policies at the executive level to improve security
- Other technical recommendations
Security alerts are viewed in real time – with each new CTI report automatically fed into the platform as soon as the investigation is completed. Within the platform, the same language is used for CTI alerts as for SOC perimeter alerts, and each alert is scored – making it easier for the SOC team to prioritize their workload.
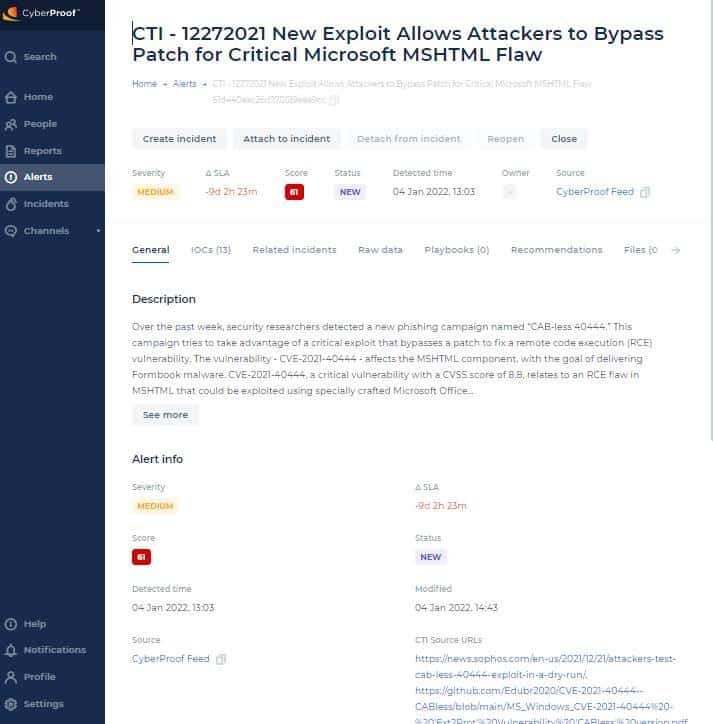
CTI Alert in the CyberProof Defense Center Platform
2. Connecting External and Internal Threats
CTI alert integration & automation provides a new level of visibility into threat coverage, connecting external threats to internal threats. In other words, SOC perimeter alerts are enriched with CTI information.
When an observable is triggered by a SIEM alert, for example, the platform automatically correlates it with related threat intelligence – providing more extensive context. This gives SOC analysts greater visibility about a range of details for each new alert: malware, threat actors, and more.
An incident that takes place inside the network could be connected to a CTI alert that had been provided months ago – providing analysts with additional context for internal incidents in real-time. Having this information available empowers L1 analysts to do more and collaborate proactively with the CTI team. It gives L1 analysts the ability to view observables proactively and understand how they relate to other alerts.
Visibility into Threat Coverage with CTI Alert Integration
3. Searchability and Reporting
Where CTI alerts are fully integrated with a common orchestration platform, the platform database – which serves as a repository of all the data – can be indexed. CTI updates stored as individual incidents are fully searchable.
Information about CTI alerts can be searched based on a variety of fields, including:
- MITRE ATT&CK mapping
- Threat actor
- Threat type
- Malware
- Tools
- Alert source
These search and reporting capabilities allow analysts to review trends so that, over time, information can be obtained about the most common threat actors or most recent threats. Reports can be generated, for example, that list all attackers coming through, or all threat intelligence provided for a specific tool.
4. Automating Documentation
When threat intelligence is handled manually, alerts tend not to be fully documented. SOC analysts copy/paste some of the CTI information – but generally, they don’t document all the available data.
Integrating and automating CTI alerts means that all intelligence-related information is fully documented – all the time.
Integrating & automating CTI alerts in a common orchestration platform means that all intelligence-related information is fully documented – all the time. CTI alerts become trackable; it’s easy to verify that each alert was handled fully and that the necessary steps were taken to mitigate the risk. Moreover, where a platform offers ChatOps communication, steps taken for each alert can be viewed in real-time.
5. Streamlining Cybersecurity Training
Information provided in a common orchestration platform can be used by the SOC team to share timely information about specific dangers with the rest of the company.
Where phishing campaigns are listed, for example, a description of a campaign provided by the platform could be shared with employees, as part of a cybersecurity training program.
6. Improving Communication with the C-Suite
With threat intelligence fully integrated with a common orchestration platform, you have full visibility into what steps were taken by the team. The work is more transparent.
This facilitates more effective communication with CISOs and meets the needs of the C-suite – so that you can respond with confidence.
Having threat intelligence fully integrated with a common orchestration platform facilitates more effective communication with CISOs.
Introducing the CyberProof Feed
CyberProof has a unique advantage over other common orchestration platforms: the CyberProof feed, which provides exclusive information based on our CTI team’s own research. The CyberProof feed combines data validated by the CTI team and data from Incident Response (IR) investigations. We also include data based on attacker information and observables we’ve seen through our work with clients. We extract new indicators of attack based on an internal investigation, and this information is integrated with the CyberProof Defense Center (CDC) platform and shared with our clients.
CTI Integration & Automation Facilitates More Effective SOC Processes
Integrating & automating CTI alerts in a common orchestration platform has a wide range of advantages. As opposed to relying on manual processes, an integrated & automated approach helps SOC teams stay up to date about new threats in real-time. It facilitates automated enrichment of CTI alerts and additional context for SOC perimeter alerts and facilitates full searchability and reporting that allows SOC analysts to uncover trends.
Moreover, the integration & automation of CTI alerts ensure consistent documentation of how CTI alerts are handled, contributes to better cybersecurity training across the enterprise, and supports effective communication with the C-suite. At CyberProof, integrating CTI alerts with the CDC platform has its own added value in the form of the CyberProof feed, which incorporates data based on observables we’ve seen through our own work with clients.
While most SOC teams today continue to use a combination of periodic PDF reports and TIPs for their threat intelligence, adopting a platform that supports full CTI integration & automation leads to faster, more consistent threat detection and response.
Adopting a platform that supports full CTI integration & automation leads to faster, more consistent threat detection and response.
Want to learn more about how your SOC can benefit from integrating & automating CTI alerts? Contact us today!